mirror of https://git.rancher.io/rke2-charts
Add tolerations to network plugins and coredns (#98)
* Add toleration for calico * Add coredns tolerations * Add multus tolerations * Add sriov tolerations * Add cilium tolerations * fix sriov * Fix corednspull/473/head
parent
73fd5c914b
commit
f35f681969
Binary file not shown.
Binary file not shown.
Binary file not shown.
Binary file not shown.
Binary file not shown.
Binary file not shown.
Binary file not shown.
|
|
@ -0,0 +1,5 @@
|
|||
apiVersion: v1
|
||||
description: Installs the CRDs for rke2-calico
|
||||
name: rke2-calico-crd
|
||||
type: application
|
||||
version: v1.0.005
|
||||
|
|
@ -0,0 +1,75 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.3.0
|
||||
name: imagesets.operator.tigera.io
|
||||
spec:
|
||||
group: operator.tigera.io
|
||||
names:
|
||||
kind: ImageSet
|
||||
listKind: ImageSetList
|
||||
plural: imagesets
|
||||
singular: imageset
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: ImageSet is used to specify image digests for the images that
|
||||
the operator deploys. The name of the ImageSet is expected to be in the
|
||||
format `<variang>-<release>`. The `variant` used is `enterprise` if the
|
||||
InstallationSpec Variant is `TigeraSecureEnterprise` otherwise it is `calico`.
|
||||
The `release` must match the version of the variant that the operator is
|
||||
built to deploy, this version can be obtained by passing the `--version`
|
||||
flag to the operator binary.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: ImageSetSpec defines the desired state of ImageSet.
|
||||
properties:
|
||||
images:
|
||||
description: Images is the list of images to use digests. All images
|
||||
that the operator will deploy must be specified.
|
||||
items:
|
||||
properties:
|
||||
digest:
|
||||
description: Digest is the image identifier that will be used
|
||||
for the Image. The field should not include a leading `@`
|
||||
and must be prefixed with `sha256:`.
|
||||
type: string
|
||||
image:
|
||||
description: Image is an image that the operator deploys and
|
||||
instead of using the built in tag the operator will use the
|
||||
Digest for the image identifier. The value should be the image
|
||||
name without registry or tag or digest. For the image `docker.io/calico/node:v3.17.1`
|
||||
it should be represented as `calico/node`
|
||||
type: string
|
||||
required:
|
||||
- digest
|
||||
- image
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
subresources:
|
||||
status: {}
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,104 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
annotations:
|
||||
controller-gen.kubebuilder.io/version: v0.3.0
|
||||
name: tigerastatuses.operator.tigera.io
|
||||
spec:
|
||||
group: operator.tigera.io
|
||||
names:
|
||||
kind: TigeraStatus
|
||||
listKind: TigeraStatusList
|
||||
plural: tigerastatuses
|
||||
singular: tigerastatus
|
||||
scope: Cluster
|
||||
versions:
|
||||
- additionalPrinterColumns:
|
||||
- description: Whether the component running and stable.
|
||||
jsonPath: .status.conditions[?(@.type=='Available')].status
|
||||
name: Available
|
||||
type: string
|
||||
- description: Whether the component is processing changes.
|
||||
jsonPath: .status.conditions[?(@.type=='Progressing')].status
|
||||
name: Progressing
|
||||
type: string
|
||||
- description: Whether the component is degraded.
|
||||
jsonPath: .status.conditions[?(@.type=='Degraded')].status
|
||||
name: Degraded
|
||||
type: string
|
||||
- description: The time the component's Available status last changed.
|
||||
jsonPath: .status.conditions[?(@.type=='Available')].lastTransitionTime
|
||||
name: Since
|
||||
type: date
|
||||
name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: TigeraStatus represents the most recently observed status for
|
||||
Calico or a Calico Enterprise functional area.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: TigeraStatusSpec defines the desired state of TigeraStatus
|
||||
type: object
|
||||
status:
|
||||
description: TigeraStatusStatus defines the observed state of TigeraStatus
|
||||
properties:
|
||||
conditions:
|
||||
description: Conditions represents the latest observed set of conditions
|
||||
for this component. A component may be one or more of Available,
|
||||
Progressing, or Degraded.
|
||||
items:
|
||||
description: TigeraStatusCondition represents a condition attached
|
||||
to a particular component.
|
||||
properties:
|
||||
lastTransitionTime:
|
||||
description: The timestamp representing the start time for the
|
||||
current status.
|
||||
format: date-time
|
||||
type: string
|
||||
message:
|
||||
description: Optionally, a detailed message providing additional
|
||||
context.
|
||||
type: string
|
||||
reason:
|
||||
description: A brief reason explaining the condition.
|
||||
type: string
|
||||
status:
|
||||
description: The status of the condition. May be True, False,
|
||||
or Unknown.
|
||||
type: string
|
||||
type:
|
||||
description: The type of condition. May be Available, Progressing,
|
||||
or Degraded.
|
||||
type: string
|
||||
required:
|
||||
- lastTransitionTime
|
||||
- status
|
||||
- type
|
||||
type: object
|
||||
type: array
|
||||
required:
|
||||
- conditions
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
subresources:
|
||||
status: {}
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,7 @@
|
|||
annotations:
|
||||
catalog.cattle.io/namespace: tigera-operator
|
||||
apiVersion: v2
|
||||
appVersion: v3.19.1
|
||||
description: Installs the Tigera operator for Calico
|
||||
name: rke2-calico
|
||||
version: v3.19.1-105
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
{{/* generate the image name for a component*/}}
|
||||
{{- define "tigera-operator.image" -}}
|
||||
{{- if .Values.global.systemDefaultRegistry -}}
|
||||
{{- $_ := set .Values.tigeraOperator "registry" .Values.global.systemDefaultRegistry -}}
|
||||
{{- end -}}
|
||||
{{- if .Values.tigeraOperator.registry -}}
|
||||
{{- .Values.tigeraOperator.registry | trimSuffix "/" -}}/
|
||||
{{- end -}}
|
||||
{{- .Values.tigeraOperator.image -}}:{{- .Values.tigeraOperator.version -}}
|
||||
{{- end -}}
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
{{/* if any of .Values.certs.node or .Values.certs.typha is not nil */}}
|
||||
{{ if without (concat (values .Values.certs.node) (values .Values.certs.typha)) nil }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: node-certs
|
||||
namespace: tigera-operator
|
||||
type: Opaque
|
||||
data:
|
||||
cert.crt: {{ required "must set certs.node.cert" .Values.certs.node.cert | b64enc }}
|
||||
key.key: {{ required "must set certs.node.key" .Values.certs.node.key | b64enc }}
|
||||
common-name: {{ required "must set certs.node.commonName" .Values.certs.node.commonName | b64enc }}
|
||||
{{ end }}
|
||||
|
|
@ -0,0 +1,23 @@
|
|||
{{/* if any of .Values.certs.node or .Values.certs.typha is not nil */}}
|
||||
{{ if without (concat (values .Values.certs.node) (values .Values.certs.typha)) nil }}
|
||||
kind: ConfigMap
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: typha-ca
|
||||
namespace: tigera-operator
|
||||
data:
|
||||
caBundle: |
|
||||
{{ required "must set certs.typha.caBundle" .Values.certs.typha.caBundle | indent 4}}
|
||||
---
|
||||
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: typha-certs
|
||||
namespace: tigera-operator
|
||||
type: Opaque
|
||||
data:
|
||||
cert.crt: {{ required "must set certs.typha.cert" .Values.certs.typha.cert | b64enc }}
|
||||
key.key: {{ required "must set certs.typha.key" .Values.certs.typha.key | b64enc }}
|
||||
common-name: {{ required "must set certs.typha.commonName" .Values.certs.typha.commonName | b64enc }}
|
||||
{{ end }}
|
||||
|
|
@ -0,0 +1,141 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: bgpconfigurations.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: BGPConfiguration
|
||||
listKind: BGPConfigurationList
|
||||
plural: bgpconfigurations
|
||||
singular: bgpconfiguration
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: BGPConfiguration contains the configuration for any BGP routing.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: BGPConfigurationSpec contains the values of the BGP configuration.
|
||||
properties:
|
||||
asNumber:
|
||||
description: 'ASNumber is the default AS number used by a node. [Default:
|
||||
64512]'
|
||||
format: int32
|
||||
type: integer
|
||||
communities:
|
||||
description: Communities is a list of BGP community values and their
|
||||
arbitrary names for tagging routes.
|
||||
items:
|
||||
description: Community contains standard or large community value
|
||||
and its name.
|
||||
properties:
|
||||
name:
|
||||
description: Name given to community value.
|
||||
type: string
|
||||
value:
|
||||
description: Value must be of format `aa:nn` or `aa:nn:mm`.
|
||||
For standard community use `aa:nn` format, where `aa` and
|
||||
`nn` are 16 bit number. For large community use `aa:nn:mm`
|
||||
format, where `aa`, `nn` and `mm` are 32 bit number. Where,
|
||||
`aa` is an AS Number, `nn` and `mm` are per-AS identifier.
|
||||
pattern: ^(\d+):(\d+)$|^(\d+):(\d+):(\d+)$
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
listenPort:
|
||||
description: ListenPort is the port where BGP protocol should listen.
|
||||
Defaults to 179
|
||||
maximum: 65535
|
||||
minimum: 1
|
||||
type: integer
|
||||
logSeverityScreen:
|
||||
description: 'LogSeverityScreen is the log severity above which logs
|
||||
are sent to the stdout. [Default: INFO]'
|
||||
type: string
|
||||
nodeToNodeMeshEnabled:
|
||||
description: 'NodeToNodeMeshEnabled sets whether full node to node
|
||||
BGP mesh is enabled. [Default: true]'
|
||||
type: boolean
|
||||
prefixAdvertisements:
|
||||
description: PrefixAdvertisements contains per-prefix advertisement
|
||||
configuration.
|
||||
items:
|
||||
description: PrefixAdvertisement configures advertisement properties
|
||||
for the specified CIDR.
|
||||
properties:
|
||||
cidr:
|
||||
description: CIDR for which properties should be advertised.
|
||||
type: string
|
||||
communities:
|
||||
description: Communities can be list of either community names
|
||||
already defined in `Specs.Communities` or community value
|
||||
of format `aa:nn` or `aa:nn:mm`. For standard community use
|
||||
`aa:nn` format, where `aa` and `nn` are 16 bit number. For
|
||||
large community use `aa:nn:mm` format, where `aa`, `nn` and
|
||||
`mm` are 32 bit number. Where,`aa` is an AS Number, `nn` and
|
||||
`mm` are per-AS identifier.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: array
|
||||
serviceClusterIPs:
|
||||
description: ServiceClusterIPs are the CIDR blocks from which service
|
||||
cluster IPs are allocated. If specified, Calico will advertise these
|
||||
blocks, as well as any cluster IPs within them.
|
||||
items:
|
||||
description: ServiceClusterIPBlock represents a single allowed ClusterIP
|
||||
CIDR block.
|
||||
properties:
|
||||
cidr:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
serviceExternalIPs:
|
||||
description: ServiceExternalIPs are the CIDR blocks for Kubernetes
|
||||
Service External IPs. Kubernetes Service ExternalIPs will only be
|
||||
advertised if they are within one of these blocks.
|
||||
items:
|
||||
description: ServiceExternalIPBlock represents a single allowed
|
||||
External IP CIDR block.
|
||||
properties:
|
||||
cidr:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
serviceLoadBalancerIPs:
|
||||
description: ServiceLoadBalancerIPs are the CIDR blocks for Kubernetes
|
||||
Service LoadBalancer IPs. Kubernetes Service status.LoadBalancer.Ingress
|
||||
IPs will only be advertised if they are within one of these blocks.
|
||||
items:
|
||||
description: ServiceLoadBalancerIPBlock represents a single allowed
|
||||
LoadBalancer IP CIDR block.
|
||||
properties:
|
||||
cidr:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,106 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: bgppeers.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: BGPPeer
|
||||
listKind: BGPPeerList
|
||||
plural: bgppeers
|
||||
singular: bgppeer
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: BGPPeerSpec contains the specification for a BGPPeer resource.
|
||||
properties:
|
||||
asNumber:
|
||||
description: The AS Number of the peer.
|
||||
format: int32
|
||||
type: integer
|
||||
keepOriginalNextHop:
|
||||
description: Option to keep the original nexthop field when routes
|
||||
are sent to a BGP Peer. Setting "true" configures the selected BGP
|
||||
Peers node to use the "next hop keep;" instead of "next hop self;"(default)
|
||||
in the specific branch of the Node on "bird.cfg".
|
||||
type: boolean
|
||||
node:
|
||||
description: The node name identifying the Calico node instance that
|
||||
is targeted by this peer. If this is not set, and no nodeSelector
|
||||
is specified, then this BGP peer selects all nodes in the cluster.
|
||||
type: string
|
||||
nodeSelector:
|
||||
description: Selector for the nodes that should have this peering. When
|
||||
this is set, the Node field must be empty.
|
||||
type: string
|
||||
password:
|
||||
description: Optional BGP password for the peerings generated by this
|
||||
BGPPeer resource.
|
||||
properties:
|
||||
secretKeyRef:
|
||||
description: Selects a key of a secret in the node pod's namespace.
|
||||
properties:
|
||||
key:
|
||||
description: The key of the secret to select from. Must be
|
||||
a valid secret key.
|
||||
type: string
|
||||
name:
|
||||
description: 'Name of the referent. More info: https://kubernetes.io/docs/concepts/overview/working-with-objects/names/#names
|
||||
TODO: Add other useful fields. apiVersion, kind, uid?'
|
||||
type: string
|
||||
optional:
|
||||
description: Specify whether the Secret or its key must be
|
||||
defined
|
||||
type: boolean
|
||||
required:
|
||||
- key
|
||||
type: object
|
||||
type: object
|
||||
peerIP:
|
||||
description: The IP address of the peer followed by an optional port
|
||||
number to peer with. If port number is given, format should be `[<IPv6>]:port`
|
||||
or `<IPv4>:<port>` for IPv4. If optional port number is not set,
|
||||
and this peer IP and ASNumber belongs to a calico/node with ListenPort
|
||||
set in BGPConfiguration, then we use that port to peer.
|
||||
type: string
|
||||
peerSelector:
|
||||
description: Selector for the remote nodes to peer with. When this
|
||||
is set, the PeerIP and ASNumber fields must be empty. For each
|
||||
peering between the local node and selected remote nodes, we configure
|
||||
an IPv4 peering if both ends have NodeBGPSpec.IPv4Address specified,
|
||||
and an IPv6 peering if both ends have NodeBGPSpec.IPv6Address specified. The
|
||||
remote AS number comes from the remote node's NodeBGPSpec.ASNumber,
|
||||
or the global default if that is not set.
|
||||
type: string
|
||||
sourceAddress:
|
||||
description: Specifies whether and how to configure a source address
|
||||
for the peerings generated by this BGPPeer resource. Default value
|
||||
"UseNodeIP" means to configure the node IP as the source address. "None"
|
||||
means not to configure a source address.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,59 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: blockaffinities.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: BlockAffinity
|
||||
listKind: BlockAffinityList
|
||||
plural: blockaffinities
|
||||
singular: blockaffinity
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: BlockAffinitySpec contains the specification for a BlockAffinity
|
||||
resource.
|
||||
properties:
|
||||
cidr:
|
||||
type: string
|
||||
deleted:
|
||||
description: Deleted indicates that this block affinity is being deleted.
|
||||
This field is a string for compatibility with older releases that
|
||||
mistakenly treat this field as a string.
|
||||
type: string
|
||||
node:
|
||||
type: string
|
||||
state:
|
||||
type: string
|
||||
required:
|
||||
- cidr
|
||||
- deleted
|
||||
- node
|
||||
- state
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,62 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: clusterinformations.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: ClusterInformation
|
||||
listKind: ClusterInformationList
|
||||
plural: clusterinformations
|
||||
singular: clusterinformation
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: ClusterInformation contains the cluster specific information.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: ClusterInformationSpec contains the values of describing
|
||||
the cluster.
|
||||
properties:
|
||||
calicoVersion:
|
||||
description: CalicoVersion is the version of Calico that the cluster
|
||||
is running
|
||||
type: string
|
||||
clusterGUID:
|
||||
description: ClusterGUID is the GUID of the cluster
|
||||
type: string
|
||||
clusterType:
|
||||
description: ClusterType describes the type of the cluster
|
||||
type: string
|
||||
datastoreReady:
|
||||
description: DatastoreReady is used during significant datastore migrations
|
||||
to signal to components such as Felix that it should wait before
|
||||
accessing the datastore.
|
||||
type: boolean
|
||||
variant:
|
||||
description: Variant declares which variant of Calico should be active.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,561 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: felixconfigurations.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: FelixConfiguration
|
||||
listKind: FelixConfigurationList
|
||||
plural: felixconfigurations
|
||||
singular: felixconfiguration
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: Felix Configuration contains the configuration for Felix.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: FelixConfigurationSpec contains the values of the Felix configuration.
|
||||
properties:
|
||||
allowIPIPPacketsFromWorkloads:
|
||||
description: 'AllowIPIPPacketsFromWorkloads controls whether Felix
|
||||
will add a rule to drop IPIP encapsulated traffic from workloads
|
||||
[Default: false]'
|
||||
type: boolean
|
||||
allowVXLANPacketsFromWorkloads:
|
||||
description: 'AllowVXLANPacketsFromWorkloads controls whether Felix
|
||||
will add a rule to drop VXLAN encapsulated traffic from workloads
|
||||
[Default: false]'
|
||||
type: boolean
|
||||
awsSrcDstCheck:
|
||||
description: 'Set source-destination-check on AWS EC2 instances. Accepted
|
||||
value must be one of "DoNothing", "Enabled" or "Disabled". [Default:
|
||||
DoNothing]'
|
||||
enum:
|
||||
- DoNothing
|
||||
- Enable
|
||||
- Disable
|
||||
type: string
|
||||
bpfConnectTimeLoadBalancingEnabled:
|
||||
description: 'BPFConnectTimeLoadBalancingEnabled when in BPF mode,
|
||||
controls whether Felix installs the connection-time load balancer. The
|
||||
connect-time load balancer is required for the host to be able to
|
||||
reach Kubernetes services and it improves the performance of pod-to-service
|
||||
connections. The only reason to disable it is for debugging purposes. [Default:
|
||||
true]'
|
||||
type: boolean
|
||||
bpfDataIfacePattern:
|
||||
description: BPFDataIfacePattern is a regular expression that controls
|
||||
which interfaces Felix should attach BPF programs to in order to
|
||||
catch traffic to/from the network. This needs to match the interfaces
|
||||
that Calico workload traffic flows over as well as any interfaces
|
||||
that handle incoming traffic to nodeports and services from outside
|
||||
the cluster. It should not match the workload interfaces (usually
|
||||
named cali...).
|
||||
type: string
|
||||
bpfDisableUnprivileged:
|
||||
description: 'BPFDisableUnprivileged, if enabled, Felix sets the kernel.unprivileged_bpf_disabled
|
||||
sysctl to disable unprivileged use of BPF. This ensures that unprivileged
|
||||
users cannot access Calico''s BPF maps and cannot insert their own
|
||||
BPF programs to interfere with Calico''s. [Default: true]'
|
||||
type: boolean
|
||||
bpfEnabled:
|
||||
description: 'BPFEnabled, if enabled Felix will use the BPF dataplane.
|
||||
[Default: false]'
|
||||
type: boolean
|
||||
bpfExtToServiceConnmark:
|
||||
description: 'BPFExtToServiceConnmark in BPF mode, control a 32bit
|
||||
mark that is set on connections from an external client to a local
|
||||
service. This mark allows us to control how packets of that connection
|
||||
are routed within the host and how is routing intepreted by RPF
|
||||
check. [Default: 0]'
|
||||
type: integer
|
||||
bpfExternalServiceMode:
|
||||
description: 'BPFExternalServiceMode in BPF mode, controls how connections
|
||||
from outside the cluster to services (node ports and cluster IPs)
|
||||
are forwarded to remote workloads. If set to "Tunnel" then both
|
||||
request and response traffic is tunneled to the remote node. If
|
||||
set to "DSR", the request traffic is tunneled but the response traffic
|
||||
is sent directly from the remote node. In "DSR" mode, the remote
|
||||
node appears to use the IP of the ingress node; this requires a
|
||||
permissive L2 network. [Default: Tunnel]'
|
||||
type: string
|
||||
bpfKubeProxyEndpointSlicesEnabled:
|
||||
description: BPFKubeProxyEndpointSlicesEnabled in BPF mode, controls
|
||||
whether Felix's embedded kube-proxy accepts EndpointSlices or not.
|
||||
type: boolean
|
||||
bpfKubeProxyIptablesCleanupEnabled:
|
||||
description: 'BPFKubeProxyIptablesCleanupEnabled, if enabled in BPF
|
||||
mode, Felix will proactively clean up the upstream Kubernetes kube-proxy''s
|
||||
iptables chains. Should only be enabled if kube-proxy is not running. [Default:
|
||||
true]'
|
||||
type: boolean
|
||||
bpfKubeProxyMinSyncPeriod:
|
||||
description: 'BPFKubeProxyMinSyncPeriod, in BPF mode, controls the
|
||||
minimum time between updates to the dataplane for Felix''s embedded
|
||||
kube-proxy. Lower values give reduced set-up latency. Higher values
|
||||
reduce Felix CPU usage by batching up more work. [Default: 1s]'
|
||||
type: string
|
||||
bpfLogLevel:
|
||||
description: 'BPFLogLevel controls the log level of the BPF programs
|
||||
when in BPF dataplane mode. One of "Off", "Info", or "Debug". The
|
||||
logs are emitted to the BPF trace pipe, accessible with the command
|
||||
`tc exec bpf debug`. [Default: Off].'
|
||||
type: string
|
||||
chainInsertMode:
|
||||
description: 'ChainInsertMode controls whether Felix hooks the kernel''s
|
||||
top-level iptables chains by inserting a rule at the top of the
|
||||
chain or by appending a rule at the bottom. insert is the safe default
|
||||
since it prevents Calico''s rules from being bypassed. If you switch
|
||||
to append mode, be sure that the other rules in the chains signal
|
||||
acceptance by falling through to the Calico rules, otherwise the
|
||||
Calico policy will be bypassed. [Default: insert]'
|
||||
type: string
|
||||
dataplaneDriver:
|
||||
type: string
|
||||
debugDisableLogDropping:
|
||||
type: boolean
|
||||
debugMemoryProfilePath:
|
||||
type: string
|
||||
debugSimulateCalcGraphHangAfter:
|
||||
type: string
|
||||
debugSimulateDataplaneHangAfter:
|
||||
type: string
|
||||
defaultEndpointToHostAction:
|
||||
description: 'DefaultEndpointToHostAction controls what happens to
|
||||
traffic that goes from a workload endpoint to the host itself (after
|
||||
the traffic hits the endpoint egress policy). By default Calico
|
||||
blocks traffic from workload endpoints to the host itself with an
|
||||
iptables "DROP" action. If you want to allow some or all traffic
|
||||
from endpoint to host, set this parameter to RETURN or ACCEPT. Use
|
||||
RETURN if you have your own rules in the iptables "INPUT" chain;
|
||||
Calico will insert its rules at the top of that chain, then "RETURN"
|
||||
packets to the "INPUT" chain once it has completed processing workload
|
||||
endpoint egress policy. Use ACCEPT to unconditionally accept packets
|
||||
from workloads after processing workload endpoint egress policy.
|
||||
[Default: Drop]'
|
||||
type: string
|
||||
deviceRouteProtocol:
|
||||
description: This defines the route protocol added to programmed device
|
||||
routes, by default this will be RTPROT_BOOT when left blank.
|
||||
type: integer
|
||||
deviceRouteSourceAddress:
|
||||
description: This is the source address to use on programmed device
|
||||
routes. By default the source address is left blank, leaving the
|
||||
kernel to choose the source address used.
|
||||
type: string
|
||||
disableConntrackInvalidCheck:
|
||||
type: boolean
|
||||
endpointReportingDelay:
|
||||
type: string
|
||||
endpointReportingEnabled:
|
||||
type: boolean
|
||||
externalNodesList:
|
||||
description: ExternalNodesCIDRList is a list of CIDR's of external-non-calico-nodes
|
||||
which may source tunnel traffic and have the tunneled traffic be
|
||||
accepted at calico nodes.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
failsafeInboundHostPorts:
|
||||
description: 'FailsafeInboundHostPorts is a list of UDP/TCP ports
|
||||
and CIDRs that Felix will allow incoming traffic to host endpoints
|
||||
on irrespective of the security policy. This is useful to avoid
|
||||
accidentally cutting off a host with incorrect configuration. For
|
||||
back-compatibility, if the protocol is not specified, it defaults
|
||||
to "tcp". If a CIDR is not specified, it will allow traffic from
|
||||
all addresses. To disable all inbound host ports, use the value
|
||||
none. The default value allows ssh access and DHCP. [Default: tcp:22,
|
||||
udp:68, tcp:179, tcp:2379, tcp:2380, tcp:6443, tcp:6666, tcp:6667]'
|
||||
items:
|
||||
description: ProtoPort is combination of protocol, port, and CIDR.
|
||||
Protocol and port must be specified.
|
||||
properties:
|
||||
net:
|
||||
type: string
|
||||
port:
|
||||
type: integer
|
||||
protocol:
|
||||
type: string
|
||||
required:
|
||||
- port
|
||||
- protocol
|
||||
type: object
|
||||
type: array
|
||||
failsafeOutboundHostPorts:
|
||||
description: 'FailsafeOutboundHostPorts is a list of UDP/TCP ports
|
||||
and CIDRs that Felix will allow outgoing traffic from host endpoints
|
||||
to irrespective of the security policy. This is useful to avoid
|
||||
accidentally cutting off a host with incorrect configuration. For
|
||||
back-compatibility, if the protocol is not specified, it defaults
|
||||
to "tcp". If a CIDR is not specified, it will allow traffic from
|
||||
all addresses. To disable all outbound host ports, use the value
|
||||
none. The default value opens etcd''s standard ports to ensure that
|
||||
Felix does not get cut off from etcd as well as allowing DHCP and
|
||||
DNS. [Default: tcp:179, tcp:2379, tcp:2380, tcp:6443, tcp:6666,
|
||||
tcp:6667, udp:53, udp:67]'
|
||||
items:
|
||||
description: ProtoPort is combination of protocol, port, and CIDR.
|
||||
Protocol and port must be specified.
|
||||
properties:
|
||||
net:
|
||||
type: string
|
||||
port:
|
||||
type: integer
|
||||
protocol:
|
||||
type: string
|
||||
required:
|
||||
- port
|
||||
- protocol
|
||||
type: object
|
||||
type: array
|
||||
featureDetectOverride:
|
||||
description: FeatureDetectOverride is used to override the feature
|
||||
detection. Values are specified in a comma separated list with no
|
||||
spaces, example; "SNATFullyRandom=true,MASQFullyRandom=false,RestoreSupportsLock=".
|
||||
"true" or "false" will force the feature, empty or omitted values
|
||||
are auto-detected.
|
||||
type: string
|
||||
genericXDPEnabled:
|
||||
description: 'GenericXDPEnabled enables Generic XDP so network cards
|
||||
that don''t support XDP offload or driver modes can use XDP. This
|
||||
is not recommended since it doesn''t provide better performance
|
||||
than iptables. [Default: false]'
|
||||
type: boolean
|
||||
healthEnabled:
|
||||
type: boolean
|
||||
healthHost:
|
||||
type: string
|
||||
healthPort:
|
||||
type: integer
|
||||
interfaceExclude:
|
||||
description: 'InterfaceExclude is a comma-separated list of interfaces
|
||||
that Felix should exclude when monitoring for host endpoints. The
|
||||
default value ensures that Felix ignores Kubernetes'' IPVS dummy
|
||||
interface, which is used internally by kube-proxy. If you want to
|
||||
exclude multiple interface names using a single value, the list
|
||||
supports regular expressions. For regular expressions you must wrap
|
||||
the value with ''/''. For example having values ''/^kube/,veth1''
|
||||
will exclude all interfaces that begin with ''kube'' and also the
|
||||
interface ''veth1''. [Default: kube-ipvs0]'
|
||||
type: string
|
||||
interfacePrefix:
|
||||
description: 'InterfacePrefix is the interface name prefix that identifies
|
||||
workload endpoints and so distinguishes them from host endpoint
|
||||
interfaces. Note: in environments other than bare metal, the orchestrators
|
||||
configure this appropriately. For example our Kubernetes and Docker
|
||||
integrations set the ''cali'' value, and our OpenStack integration
|
||||
sets the ''tap'' value. [Default: cali]'
|
||||
type: string
|
||||
interfaceRefreshInterval:
|
||||
description: InterfaceRefreshInterval is the period at which Felix
|
||||
rescans local interfaces to verify their state. The rescan can be
|
||||
disabled by setting the interval to 0.
|
||||
type: string
|
||||
ipipEnabled:
|
||||
type: boolean
|
||||
ipipMTU:
|
||||
description: 'IPIPMTU is the MTU to set on the tunnel device. See
|
||||
Configuring MTU [Default: 1440]'
|
||||
type: integer
|
||||
ipsetsRefreshInterval:
|
||||
description: 'IpsetsRefreshInterval is the period at which Felix re-checks
|
||||
all iptables state to ensure that no other process has accidentally
|
||||
broken Calico''s rules. Set to 0 to disable iptables refresh. [Default:
|
||||
90s]'
|
||||
type: string
|
||||
iptablesBackend:
|
||||
description: IptablesBackend specifies which backend of iptables will
|
||||
be used. The default is legacy.
|
||||
type: string
|
||||
iptablesFilterAllowAction:
|
||||
type: string
|
||||
iptablesLockFilePath:
|
||||
description: 'IptablesLockFilePath is the location of the iptables
|
||||
lock file. You may need to change this if the lock file is not in
|
||||
its standard location (for example if you have mapped it into Felix''s
|
||||
container at a different path). [Default: /run/xtables.lock]'
|
||||
type: string
|
||||
iptablesLockProbeInterval:
|
||||
description: 'IptablesLockProbeInterval is the time that Felix will
|
||||
wait between attempts to acquire the iptables lock if it is not
|
||||
available. Lower values make Felix more responsive when the lock
|
||||
is contended, but use more CPU. [Default: 50ms]'
|
||||
type: string
|
||||
iptablesLockTimeout:
|
||||
description: 'IptablesLockTimeout is the time that Felix will wait
|
||||
for the iptables lock, or 0, to disable. To use this feature, Felix
|
||||
must share the iptables lock file with all other processes that
|
||||
also take the lock. When running Felix inside a container, this
|
||||
requires the /run directory of the host to be mounted into the calico/node
|
||||
or calico/felix container. [Default: 0s disabled]'
|
||||
type: string
|
||||
iptablesMangleAllowAction:
|
||||
type: string
|
||||
iptablesMarkMask:
|
||||
description: 'IptablesMarkMask is the mask that Felix selects its
|
||||
IPTables Mark bits from. Should be a 32 bit hexadecimal number with
|
||||
at least 8 bits set, none of which clash with any other mark bits
|
||||
in use on the system. [Default: 0xff000000]'
|
||||
format: int32
|
||||
type: integer
|
||||
iptablesNATOutgoingInterfaceFilter:
|
||||
type: string
|
||||
iptablesPostWriteCheckInterval:
|
||||
description: 'IptablesPostWriteCheckInterval is the period after Felix
|
||||
has done a write to the dataplane that it schedules an extra read
|
||||
back in order to check the write was not clobbered by another process.
|
||||
This should only occur if another application on the system doesn''t
|
||||
respect the iptables lock. [Default: 1s]'
|
||||
type: string
|
||||
iptablesRefreshInterval:
|
||||
description: 'IptablesRefreshInterval is the period at which Felix
|
||||
re-checks the IP sets in the dataplane to ensure that no other process
|
||||
has accidentally broken Calico''s rules. Set to 0 to disable IP
|
||||
sets refresh. Note: the default for this value is lower than the
|
||||
other refresh intervals as a workaround for a Linux kernel bug that
|
||||
was fixed in kernel version 4.11. If you are using v4.11 or greater
|
||||
you may want to set this to, a higher value to reduce Felix CPU
|
||||
usage. [Default: 10s]'
|
||||
type: string
|
||||
ipv6Support:
|
||||
type: boolean
|
||||
kubeNodePortRanges:
|
||||
description: 'KubeNodePortRanges holds list of port ranges used for
|
||||
service node ports. Only used if felix detects kube-proxy running
|
||||
in ipvs mode. Felix uses these ranges to separate host and workload
|
||||
traffic. [Default: 30000:32767].'
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
logFilePath:
|
||||
description: 'LogFilePath is the full path to the Felix log. Set to
|
||||
none to disable file logging. [Default: /var/log/calico/felix.log]'
|
||||
type: string
|
||||
logPrefix:
|
||||
description: 'LogPrefix is the log prefix that Felix uses when rendering
|
||||
LOG rules. [Default: calico-packet]'
|
||||
type: string
|
||||
logSeverityFile:
|
||||
description: 'LogSeverityFile is the log severity above which logs
|
||||
are sent to the log file. [Default: Info]'
|
||||
type: string
|
||||
logSeverityScreen:
|
||||
description: 'LogSeverityScreen is the log severity above which logs
|
||||
are sent to the stdout. [Default: Info]'
|
||||
type: string
|
||||
logSeveritySys:
|
||||
description: 'LogSeveritySys is the log severity above which logs
|
||||
are sent to the syslog. Set to None for no logging to syslog. [Default:
|
||||
Info]'
|
||||
type: string
|
||||
maxIpsetSize:
|
||||
type: integer
|
||||
metadataAddr:
|
||||
description: 'MetadataAddr is the IP address or domain name of the
|
||||
server that can answer VM queries for cloud-init metadata. In OpenStack,
|
||||
this corresponds to the machine running nova-api (or in Ubuntu,
|
||||
nova-api-metadata). A value of none (case insensitive) means that
|
||||
Felix should not set up any NAT rule for the metadata path. [Default:
|
||||
127.0.0.1]'
|
||||
type: string
|
||||
metadataPort:
|
||||
description: 'MetadataPort is the port of the metadata server. This,
|
||||
combined with global.MetadataAddr (if not ''None''), is used to
|
||||
set up a NAT rule, from 169.254.169.254:80 to MetadataAddr:MetadataPort.
|
||||
In most cases this should not need to be changed [Default: 8775].'
|
||||
type: integer
|
||||
mtuIfacePattern:
|
||||
description: MTUIfacePattern is a regular expression that controls
|
||||
which interfaces Felix should scan in order to calculate the host's
|
||||
MTU. This should not match workload interfaces (usually named cali...).
|
||||
type: string
|
||||
natOutgoingAddress:
|
||||
description: NATOutgoingAddress specifies an address to use when performing
|
||||
source NAT for traffic in a natOutgoing pool that is leaving the
|
||||
network. By default the address used is an address on the interface
|
||||
the traffic is leaving on (ie it uses the iptables MASQUERADE target)
|
||||
type: string
|
||||
natPortRange:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: NATPortRange specifies the range of ports that is used
|
||||
for port mapping when doing outgoing NAT. When unset the default
|
||||
behavior of the network stack is used.
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
netlinkTimeout:
|
||||
type: string
|
||||
openstackRegion:
|
||||
description: 'OpenstackRegion is the name of the region that a particular
|
||||
Felix belongs to. In a multi-region Calico/OpenStack deployment,
|
||||
this must be configured somehow for each Felix (here in the datamodel,
|
||||
or in felix.cfg or the environment on each compute node), and must
|
||||
match the [calico] openstack_region value configured in neutron.conf
|
||||
on each node. [Default: Empty]'
|
||||
type: string
|
||||
policySyncPathPrefix:
|
||||
description: 'PolicySyncPathPrefix is used to by Felix to communicate
|
||||
policy changes to external services, like Application layer policy.
|
||||
[Default: Empty]'
|
||||
type: string
|
||||
prometheusGoMetricsEnabled:
|
||||
description: 'PrometheusGoMetricsEnabled disables Go runtime metrics
|
||||
collection, which the Prometheus client does by default, when set
|
||||
to false. This reduces the number of metrics reported, reducing
|
||||
Prometheus load. [Default: true]'
|
||||
type: boolean
|
||||
prometheusMetricsEnabled:
|
||||
description: 'PrometheusMetricsEnabled enables the Prometheus metrics
|
||||
server in Felix if set to true. [Default: false]'
|
||||
type: boolean
|
||||
prometheusMetricsHost:
|
||||
description: 'PrometheusMetricsHost is the host that the Prometheus
|
||||
metrics server should bind to. [Default: empty]'
|
||||
type: string
|
||||
prometheusMetricsPort:
|
||||
description: 'PrometheusMetricsPort is the TCP port that the Prometheus
|
||||
metrics server should bind to. [Default: 9091]'
|
||||
type: integer
|
||||
prometheusProcessMetricsEnabled:
|
||||
description: 'PrometheusProcessMetricsEnabled disables process metrics
|
||||
collection, which the Prometheus client does by default, when set
|
||||
to false. This reduces the number of metrics reported, reducing
|
||||
Prometheus load. [Default: true]'
|
||||
type: boolean
|
||||
removeExternalRoutes:
|
||||
description: Whether or not to remove device routes that have not
|
||||
been programmed by Felix. Disabling this will allow external applications
|
||||
to also add device routes. This is enabled by default which means
|
||||
we will remove externally added routes.
|
||||
type: boolean
|
||||
reportingInterval:
|
||||
description: 'ReportingInterval is the interval at which Felix reports
|
||||
its status into the datastore or 0 to disable. Must be non-zero
|
||||
in OpenStack deployments. [Default: 30s]'
|
||||
type: string
|
||||
reportingTTL:
|
||||
description: 'ReportingTTL is the time-to-live setting for process-wide
|
||||
status reports. [Default: 90s]'
|
||||
type: string
|
||||
routeRefreshInterval:
|
||||
description: 'RouteRefreshInterval is the period at which Felix re-checks
|
||||
the routes in the dataplane to ensure that no other process has
|
||||
accidentally broken Calico''s rules. Set to 0 to disable route refresh.
|
||||
[Default: 90s]'
|
||||
type: string
|
||||
routeSource:
|
||||
description: 'RouteSource configures where Felix gets its routing
|
||||
information. - WorkloadIPs: use workload endpoints to construct
|
||||
routes. - CalicoIPAM: the default - use IPAM data to construct routes.'
|
||||
type: string
|
||||
routeTableRange:
|
||||
description: Calico programs additional Linux route tables for various
|
||||
purposes. RouteTableRange specifies the indices of the route tables
|
||||
that Calico should use.
|
||||
properties:
|
||||
max:
|
||||
type: integer
|
||||
min:
|
||||
type: integer
|
||||
required:
|
||||
- max
|
||||
- min
|
||||
type: object
|
||||
serviceLoopPrevention:
|
||||
description: 'When service IP advertisement is enabled, prevent routing
|
||||
loops to service IPs that are not in use, by dropping or rejecting
|
||||
packets that do not get DNAT''d by kube-proxy. Unless set to "Disabled",
|
||||
in which case such routing loops continue to be allowed. [Default:
|
||||
Drop]'
|
||||
type: string
|
||||
sidecarAccelerationEnabled:
|
||||
description: 'SidecarAccelerationEnabled enables experimental sidecar
|
||||
acceleration [Default: false]'
|
||||
type: boolean
|
||||
usageReportingEnabled:
|
||||
description: 'UsageReportingEnabled reports anonymous Calico version
|
||||
number and cluster size to projectcalico.org. Logs warnings returned
|
||||
by the usage server. For example, if a significant security vulnerability
|
||||
has been discovered in the version of Calico being used. [Default:
|
||||
true]'
|
||||
type: boolean
|
||||
usageReportingInitialDelay:
|
||||
description: 'UsageReportingInitialDelay controls the minimum delay
|
||||
before Felix makes a report. [Default: 300s]'
|
||||
type: string
|
||||
usageReportingInterval:
|
||||
description: 'UsageReportingInterval controls the interval at which
|
||||
Felix makes reports. [Default: 86400s]'
|
||||
type: string
|
||||
useInternalDataplaneDriver:
|
||||
type: boolean
|
||||
vxlanEnabled:
|
||||
type: boolean
|
||||
vxlanMTU:
|
||||
description: 'VXLANMTU is the MTU to set on the tunnel device. See
|
||||
Configuring MTU [Default: 1440]'
|
||||
type: integer
|
||||
vxlanPort:
|
||||
type: integer
|
||||
vxlanVNI:
|
||||
type: integer
|
||||
wireguardEnabled:
|
||||
description: 'WireguardEnabled controls whether Wireguard is enabled.
|
||||
[Default: false]'
|
||||
type: boolean
|
||||
wireguardInterfaceName:
|
||||
description: 'WireguardInterfaceName specifies the name to use for
|
||||
the Wireguard interface. [Default: wg.calico]'
|
||||
type: string
|
||||
wireguardListeningPort:
|
||||
description: 'WireguardListeningPort controls the listening port used
|
||||
by Wireguard. [Default: 51820]'
|
||||
type: integer
|
||||
wireguardMTU:
|
||||
description: 'WireguardMTU controls the MTU on the Wireguard interface.
|
||||
See Configuring MTU [Default: 1420]'
|
||||
type: integer
|
||||
wireguardRoutingRulePriority:
|
||||
description: 'WireguardRoutingRulePriority controls the priority value
|
||||
to use for the Wireguard routing rule. [Default: 99]'
|
||||
type: integer
|
||||
xdpEnabled:
|
||||
description: 'XDPEnabled enables XDP acceleration for suitable untracked
|
||||
incoming deny rules. [Default: true]'
|
||||
type: boolean
|
||||
xdpRefreshInterval:
|
||||
description: 'XDPRefreshInterval is the period at which Felix re-checks
|
||||
all XDP state to ensure that no other process has accidentally broken
|
||||
Calico''s BPF maps or attached programs. Set to 0 to disable XDP
|
||||
refresh. [Default: 90s]'
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,769 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: globalnetworkpolicies.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: GlobalNetworkPolicy
|
||||
listKind: GlobalNetworkPolicyList
|
||||
plural: globalnetworkpolicies
|
||||
singular: globalnetworkpolicy
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
properties:
|
||||
applyOnForward:
|
||||
description: ApplyOnForward indicates to apply the rules in this policy
|
||||
on forward traffic.
|
||||
type: boolean
|
||||
doNotTrack:
|
||||
description: DoNotTrack indicates whether packets matched by the rules
|
||||
in this policy should go through the data plane's connection tracking,
|
||||
such as Linux conntrack. If True, the rules in this policy are
|
||||
applied before any data plane connection tracking, and packets allowed
|
||||
by this policy are marked as not to be tracked.
|
||||
type: boolean
|
||||
egress:
|
||||
description: The ordered set of egress rules. Each rule contains
|
||||
a set of packet match criteria and a corresponding action to apply.
|
||||
items:
|
||||
description: "A Rule encapsulates a set of match criteria and an
|
||||
action. Both selector-based security Policy and security Profiles
|
||||
reference rules - separated out as a list of rules for both ingress
|
||||
and egress packet matching. \n Each positive match criteria has
|
||||
a negated version, prefixed with \"Not\". All the match criteria
|
||||
within a rule must be satisfied for a packet to match. A single
|
||||
rule can contain the positive and negative version of a match
|
||||
and both must be satisfied for the rule to match."
|
||||
properties:
|
||||
action:
|
||||
type: string
|
||||
destination:
|
||||
description: Destination contains the match criteria that apply
|
||||
to destination entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
http:
|
||||
description: HTTP contains match criteria that apply to HTTP
|
||||
requests.
|
||||
properties:
|
||||
methods:
|
||||
description: Methods is an optional field that restricts
|
||||
the rule to apply only to HTTP requests that use one of
|
||||
the listed HTTP Methods (e.g. GET, PUT, etc.) Multiple
|
||||
methods are OR'd together.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
paths:
|
||||
description: 'Paths is an optional field that restricts
|
||||
the rule to apply to HTTP requests that use one of the
|
||||
listed HTTP Paths. Multiple paths are OR''d together.
|
||||
e.g: - exact: /foo - prefix: /bar NOTE: Each entry may
|
||||
ONLY specify either a `exact` or a `prefix` match. The
|
||||
validator will check for it.'
|
||||
items:
|
||||
description: 'HTTPPath specifies an HTTP path to match.
|
||||
It may be either of the form: exact: <path>: which matches
|
||||
the path exactly or prefix: <path-prefix>: which matches
|
||||
the path prefix'
|
||||
properties:
|
||||
exact:
|
||||
type: string
|
||||
prefix:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
icmp:
|
||||
description: ICMP is an optional field that restricts the rule
|
||||
to apply to a specific type and code of ICMP traffic. This
|
||||
should only be specified if the Protocol field is set to "ICMP"
|
||||
or "ICMPv6".
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
ipVersion:
|
||||
description: IPVersion is an optional field that restricts the
|
||||
rule to only match a specific IP version.
|
||||
type: integer
|
||||
metadata:
|
||||
description: Metadata contains additional information for this
|
||||
rule
|
||||
properties:
|
||||
annotations:
|
||||
additionalProperties:
|
||||
type: string
|
||||
description: Annotations is a set of key value pairs that
|
||||
give extra information about the rule
|
||||
type: object
|
||||
type: object
|
||||
notICMP:
|
||||
description: NotICMP is the negated version of the ICMP field.
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
notProtocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: NotProtocol is the negated version of the Protocol
|
||||
field.
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
protocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: "Protocol is an optional field that restricts the
|
||||
rule to only apply to traffic of a specific IP protocol. Required
|
||||
if any of the EntityRules contain Ports (because ports only
|
||||
apply to certain protocols). \n Must be one of these string
|
||||
values: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",
|
||||
\"UDPLite\" or an integer in the range 1-255."
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
source:
|
||||
description: Source contains the match criteria that apply to
|
||||
source entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
required:
|
||||
- action
|
||||
type: object
|
||||
type: array
|
||||
ingress:
|
||||
description: The ordered set of ingress rules. Each rule contains
|
||||
a set of packet match criteria and a corresponding action to apply.
|
||||
items:
|
||||
description: "A Rule encapsulates a set of match criteria and an
|
||||
action. Both selector-based security Policy and security Profiles
|
||||
reference rules - separated out as a list of rules for both ingress
|
||||
and egress packet matching. \n Each positive match criteria has
|
||||
a negated version, prefixed with \"Not\". All the match criteria
|
||||
within a rule must be satisfied for a packet to match. A single
|
||||
rule can contain the positive and negative version of a match
|
||||
and both must be satisfied for the rule to match."
|
||||
properties:
|
||||
action:
|
||||
type: string
|
||||
destination:
|
||||
description: Destination contains the match criteria that apply
|
||||
to destination entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
http:
|
||||
description: HTTP contains match criteria that apply to HTTP
|
||||
requests.
|
||||
properties:
|
||||
methods:
|
||||
description: Methods is an optional field that restricts
|
||||
the rule to apply only to HTTP requests that use one of
|
||||
the listed HTTP Methods (e.g. GET, PUT, etc.) Multiple
|
||||
methods are OR'd together.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
paths:
|
||||
description: 'Paths is an optional field that restricts
|
||||
the rule to apply to HTTP requests that use one of the
|
||||
listed HTTP Paths. Multiple paths are OR''d together.
|
||||
e.g: - exact: /foo - prefix: /bar NOTE: Each entry may
|
||||
ONLY specify either a `exact` or a `prefix` match. The
|
||||
validator will check for it.'
|
||||
items:
|
||||
description: 'HTTPPath specifies an HTTP path to match.
|
||||
It may be either of the form: exact: <path>: which matches
|
||||
the path exactly or prefix: <path-prefix>: which matches
|
||||
the path prefix'
|
||||
properties:
|
||||
exact:
|
||||
type: string
|
||||
prefix:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
icmp:
|
||||
description: ICMP is an optional field that restricts the rule
|
||||
to apply to a specific type and code of ICMP traffic. This
|
||||
should only be specified if the Protocol field is set to "ICMP"
|
||||
or "ICMPv6".
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
ipVersion:
|
||||
description: IPVersion is an optional field that restricts the
|
||||
rule to only match a specific IP version.
|
||||
type: integer
|
||||
metadata:
|
||||
description: Metadata contains additional information for this
|
||||
rule
|
||||
properties:
|
||||
annotations:
|
||||
additionalProperties:
|
||||
type: string
|
||||
description: Annotations is a set of key value pairs that
|
||||
give extra information about the rule
|
||||
type: object
|
||||
type: object
|
||||
notICMP:
|
||||
description: NotICMP is the negated version of the ICMP field.
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
notProtocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: NotProtocol is the negated version of the Protocol
|
||||
field.
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
protocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: "Protocol is an optional field that restricts the
|
||||
rule to only apply to traffic of a specific IP protocol. Required
|
||||
if any of the EntityRules contain Ports (because ports only
|
||||
apply to certain protocols). \n Must be one of these string
|
||||
values: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",
|
||||
\"UDPLite\" or an integer in the range 1-255."
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
source:
|
||||
description: Source contains the match criteria that apply to
|
||||
source entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
required:
|
||||
- action
|
||||
type: object
|
||||
type: array
|
||||
namespaceSelector:
|
||||
description: NamespaceSelector is an optional field for an expression
|
||||
used to select a pod based on namespaces.
|
||||
type: string
|
||||
order:
|
||||
description: Order is an optional field that specifies the order in
|
||||
which the policy is applied. Policies with higher "order" are applied
|
||||
after those with lower order. If the order is omitted, it may be
|
||||
considered to be "infinite" - i.e. the policy will be applied last. Policies
|
||||
with identical order will be applied in alphanumerical order based
|
||||
on the Policy "Name".
|
||||
type: number
|
||||
preDNAT:
|
||||
description: PreDNAT indicates to apply the rules in this policy before
|
||||
any DNAT.
|
||||
type: boolean
|
||||
selector:
|
||||
description: "The selector is an expression used to pick pick out
|
||||
the endpoints that the policy should be applied to. \n Selector
|
||||
expressions follow this syntax: \n \tlabel == \"string_literal\"
|
||||
\ -> comparison, e.g. my_label == \"foo bar\" \tlabel != \"string_literal\"
|
||||
\ -> not equal; also matches if label is not present \tlabel in
|
||||
{ \"a\", \"b\", \"c\", ... } -> true if the value of label X is
|
||||
one of \"a\", \"b\", \"c\" \tlabel not in { \"a\", \"b\", \"c\",
|
||||
... } -> true if the value of label X is not one of \"a\", \"b\",
|
||||
\"c\" \thas(label_name) -> True if that label is present \t! expr
|
||||
-> negation of expr \texpr && expr -> Short-circuit and \texpr
|
||||
|| expr -> Short-circuit or \t( expr ) -> parens for grouping \tall()
|
||||
or the empty selector -> matches all endpoints. \n Label names are
|
||||
allowed to contain alphanumerics, -, _ and /. String literals are
|
||||
more permissive but they do not support escape characters. \n Examples
|
||||
(with made-up labels): \n \ttype == \"webserver\" && deployment
|
||||
== \"prod\" \ttype in {\"frontend\", \"backend\"} \tdeployment !=
|
||||
\"dev\" \t! has(label_name)"
|
||||
type: string
|
||||
serviceAccountSelector:
|
||||
description: ServiceAccountSelector is an optional field for an expression
|
||||
used to select a pod based on service accounts.
|
||||
type: string
|
||||
types:
|
||||
description: "Types indicates whether this policy applies to ingress,
|
||||
or to egress, or to both. When not explicitly specified (and so
|
||||
the value on creation is empty or nil), Calico defaults Types according
|
||||
to what Ingress and Egress rules are present in the policy. The
|
||||
default is: \n - [ PolicyTypeIngress ], if there are no Egress rules
|
||||
(including the case where there are also no Ingress rules) \n
|
||||
- [ PolicyTypeEgress ], if there are Egress rules but no Ingress
|
||||
rules \n - [ PolicyTypeIngress, PolicyTypeEgress ], if there are
|
||||
both Ingress and Egress rules. \n When the policy is read back again,
|
||||
Types will always be one of these values, never empty or nil."
|
||||
items:
|
||||
description: PolicyType enumerates the possible values of the PolicySpec
|
||||
Types field.
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,51 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: globalnetworksets.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: GlobalNetworkSet
|
||||
listKind: GlobalNetworkSetList
|
||||
plural: globalnetworksets
|
||||
singular: globalnetworkset
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: GlobalNetworkSet contains a set of arbitrary IP sub-networks/CIDRs
|
||||
that share labels to allow rules to refer to them via selectors. The labels
|
||||
of GlobalNetworkSet are not namespaced.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: GlobalNetworkSetSpec contains the specification for a NetworkSet
|
||||
resource.
|
||||
properties:
|
||||
nets:
|
||||
description: The list of IP networks that belong to this set.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,106 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: hostendpoints.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: HostEndpoint
|
||||
listKind: HostEndpointList
|
||||
plural: hostendpoints
|
||||
singular: hostendpoint
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: HostEndpointSpec contains the specification for a HostEndpoint
|
||||
resource.
|
||||
properties:
|
||||
expectedIPs:
|
||||
description: "The expected IP addresses (IPv4 and IPv6) of the endpoint.
|
||||
If \"InterfaceName\" is not present, Calico will look for an interface
|
||||
matching any of the IPs in the list and apply policy to that. Note:
|
||||
\tWhen using the selector match criteria in an ingress or egress
|
||||
security Policy \tor Profile, Calico converts the selector into
|
||||
a set of IP addresses. For host \tendpoints, the ExpectedIPs field
|
||||
is used for that purpose. (If only the interface \tname is specified,
|
||||
Calico does not learn the IPs of the interface for use in match
|
||||
\tcriteria.)"
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
interfaceName:
|
||||
description: "Either \"*\", or the name of a specific Linux interface
|
||||
to apply policy to; or empty. \"*\" indicates that this HostEndpoint
|
||||
governs all traffic to, from or through the default network namespace
|
||||
of the host named by the \"Node\" field; entering and leaving that
|
||||
namespace via any interface, including those from/to non-host-networked
|
||||
local workloads. \n If InterfaceName is not \"*\", this HostEndpoint
|
||||
only governs traffic that enters or leaves the host through the
|
||||
specific interface named by InterfaceName, or - when InterfaceName
|
||||
is empty - through the specific interface that has one of the IPs
|
||||
in ExpectedIPs. Therefore, when InterfaceName is empty, at least
|
||||
one expected IP must be specified. Only external interfaces (such
|
||||
as \"eth0\") are supported here; it isn't possible for a HostEndpoint
|
||||
to protect traffic through a specific local workload interface.
|
||||
\n Note: Only some kinds of policy are implemented for \"*\" HostEndpoints;
|
||||
initially just pre-DNAT policy. Please check Calico documentation
|
||||
for the latest position."
|
||||
type: string
|
||||
node:
|
||||
description: The node name identifying the Calico node instance.
|
||||
type: string
|
||||
ports:
|
||||
description: Ports contains the endpoint's named ports, which may
|
||||
be referenced in security policy rules.
|
||||
items:
|
||||
properties:
|
||||
name:
|
||||
type: string
|
||||
port:
|
||||
type: integer
|
||||
protocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
required:
|
||||
- name
|
||||
- port
|
||||
- protocol
|
||||
type: object
|
||||
type: array
|
||||
profiles:
|
||||
description: A list of identifiers of security Profile objects that
|
||||
apply to this endpoint. Each profile is applied in the order that
|
||||
they appear in this list. Profile rules are applied after the selector-based
|
||||
security policy.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,79 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: ipamblocks.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: IPAMBlock
|
||||
listKind: IPAMBlockList
|
||||
plural: ipamblocks
|
||||
singular: ipamblock
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: IPAMBlockSpec contains the specification for an IPAMBlock
|
||||
resource.
|
||||
properties:
|
||||
affinity:
|
||||
type: string
|
||||
allocations:
|
||||
items:
|
||||
type: integer
|
||||
# TODO: This nullable is manually added in. We should update controller-gen
|
||||
# to handle []*int properly itself.
|
||||
nullable: true
|
||||
type: array
|
||||
attributes:
|
||||
items:
|
||||
properties:
|
||||
handle_id:
|
||||
type: string
|
||||
secondary:
|
||||
additionalProperties:
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
type: array
|
||||
cidr:
|
||||
type: string
|
||||
deleted:
|
||||
type: boolean
|
||||
strictAffinity:
|
||||
type: boolean
|
||||
unallocated:
|
||||
items:
|
||||
type: integer
|
||||
type: array
|
||||
required:
|
||||
- allocations
|
||||
- attributes
|
||||
- cidr
|
||||
- strictAffinity
|
||||
- unallocated
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,54 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: ipamconfigs.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: IPAMConfig
|
||||
listKind: IPAMConfigList
|
||||
plural: ipamconfigs
|
||||
singular: ipamconfig
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: IPAMConfigSpec contains the specification for an IPAMConfig
|
||||
resource.
|
||||
properties:
|
||||
autoAllocateBlocks:
|
||||
type: boolean
|
||||
maxBlocksPerHost:
|
||||
description: MaxBlocksPerHost, if non-zero, is the max number of blocks
|
||||
that can be affine to each host.
|
||||
type: integer
|
||||
strictAffinity:
|
||||
type: boolean
|
||||
required:
|
||||
- autoAllocateBlocks
|
||||
- strictAffinity
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,54 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: ipamhandles.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: IPAMHandle
|
||||
listKind: IPAMHandleList
|
||||
plural: ipamhandles
|
||||
singular: ipamhandle
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: IPAMHandleSpec contains the specification for an IPAMHandle
|
||||
resource.
|
||||
properties:
|
||||
block:
|
||||
additionalProperties:
|
||||
type: integer
|
||||
type: object
|
||||
deleted:
|
||||
type: boolean
|
||||
handleID:
|
||||
type: string
|
||||
required:
|
||||
- block
|
||||
- handleID
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,97 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: ippools.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: IPPool
|
||||
listKind: IPPoolList
|
||||
plural: ippools
|
||||
singular: ippool
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: IPPoolSpec contains the specification for an IPPool resource.
|
||||
properties:
|
||||
blockSize:
|
||||
description: The block size to use for IP address assignments from
|
||||
this pool. Defaults to 26 for IPv4 and 112 for IPv6.
|
||||
type: integer
|
||||
cidr:
|
||||
description: The pool CIDR.
|
||||
type: string
|
||||
disabled:
|
||||
description: When disabled is true, Calico IPAM will not assign addresses
|
||||
from this pool.
|
||||
type: boolean
|
||||
ipip:
|
||||
description: 'Deprecated: this field is only used for APIv1 backwards
|
||||
compatibility. Setting this field is not allowed, this field is
|
||||
for internal use only.'
|
||||
properties:
|
||||
enabled:
|
||||
description: When enabled is true, ipip tunneling will be used
|
||||
to deliver packets to destinations within this pool.
|
||||
type: boolean
|
||||
mode:
|
||||
description: The IPIP mode. This can be one of "always" or "cross-subnet". A
|
||||
mode of "always" will also use IPIP tunneling for routing to
|
||||
destination IP addresses within this pool. A mode of "cross-subnet"
|
||||
will only use IPIP tunneling when the destination node is on
|
||||
a different subnet to the originating node. The default value
|
||||
(if not specified) is "always".
|
||||
type: string
|
||||
type: object
|
||||
ipipMode:
|
||||
description: Contains configuration for IPIP tunneling for this pool.
|
||||
If not specified, then this is defaulted to "Never" (i.e. IPIP tunneling
|
||||
is disabled).
|
||||
type: string
|
||||
nat-outgoing:
|
||||
description: 'Deprecated: this field is only used for APIv1 backwards
|
||||
compatibility. Setting this field is not allowed, this field is
|
||||
for internal use only.'
|
||||
type: boolean
|
||||
natOutgoing:
|
||||
description: When nat-outgoing is true, packets sent from Calico networked
|
||||
containers in this pool to destinations outside of this pool will
|
||||
be masqueraded.
|
||||
type: boolean
|
||||
nodeSelector:
|
||||
description: Allows IPPool to allocate for a specific node by label
|
||||
selector.
|
||||
type: string
|
||||
vxlanMode:
|
||||
description: Contains configuration for VXLAN tunneling for this pool.
|
||||
If not specified, then this is defaulted to "Never" (i.e. VXLAN
|
||||
tunneling is disabled).
|
||||
type: string
|
||||
required:
|
||||
- cidr
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,230 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: kubecontrollersconfigurations.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: KubeControllersConfiguration
|
||||
listKind: KubeControllersConfigurationList
|
||||
plural: kubecontrollersconfigurations
|
||||
singular: kubecontrollersconfiguration
|
||||
scope: Cluster
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: KubeControllersConfigurationSpec contains the values of the
|
||||
Kubernetes controllers configuration.
|
||||
properties:
|
||||
controllers:
|
||||
description: Controllers enables and configures individual Kubernetes
|
||||
controllers
|
||||
properties:
|
||||
namespace:
|
||||
description: Namespace enables and configures the namespace controller.
|
||||
Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform reconciliation
|
||||
with the Calico datastore. [Default: 5m]'
|
||||
type: string
|
||||
type: object
|
||||
node:
|
||||
description: Node enables and configures the node controller.
|
||||
Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
hostEndpoint:
|
||||
description: HostEndpoint controls syncing nodes to host endpoints.
|
||||
Disabled by default, set to nil to disable.
|
||||
properties:
|
||||
autoCreate:
|
||||
description: 'AutoCreate enables automatic creation of
|
||||
host endpoints for every node. [Default: Disabled]'
|
||||
type: string
|
||||
type: object
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform reconciliation
|
||||
with the Calico datastore. [Default: 5m]'
|
||||
type: string
|
||||
syncLabels:
|
||||
description: 'SyncLabels controls whether to copy Kubernetes
|
||||
node labels to Calico nodes. [Default: Enabled]'
|
||||
type: string
|
||||
type: object
|
||||
policy:
|
||||
description: Policy enables and configures the policy controller.
|
||||
Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform reconciliation
|
||||
with the Calico datastore. [Default: 5m]'
|
||||
type: string
|
||||
type: object
|
||||
serviceAccount:
|
||||
description: ServiceAccount enables and configures the service
|
||||
account controller. Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform reconciliation
|
||||
with the Calico datastore. [Default: 5m]'
|
||||
type: string
|
||||
type: object
|
||||
workloadEndpoint:
|
||||
description: WorkloadEndpoint enables and configures the workload
|
||||
endpoint controller. Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform reconciliation
|
||||
with the Calico datastore. [Default: 5m]'
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
etcdV3CompactionPeriod:
|
||||
description: 'EtcdV3CompactionPeriod is the period between etcdv3
|
||||
compaction requests. Set to 0 to disable. [Default: 10m]'
|
||||
type: string
|
||||
healthChecks:
|
||||
description: 'HealthChecks enables or disables support for health
|
||||
checks [Default: Enabled]'
|
||||
type: string
|
||||
logSeverityScreen:
|
||||
description: 'LogSeverityScreen is the log severity above which logs
|
||||
are sent to the stdout. [Default: Info]'
|
||||
type: string
|
||||
prometheusMetricsPort:
|
||||
description: 'PrometheusMetricsPort is the TCP port that the Prometheus
|
||||
metrics server should bind to. Set to 0 to disable. [Default: 9094]'
|
||||
type: integer
|
||||
required:
|
||||
- controllers
|
||||
type: object
|
||||
status:
|
||||
description: KubeControllersConfigurationStatus represents the status
|
||||
of the configuration. It's useful for admins to be able to see the actual
|
||||
config that was applied, which can be modified by environment variables
|
||||
on the kube-controllers process.
|
||||
properties:
|
||||
environmentVars:
|
||||
additionalProperties:
|
||||
type: string
|
||||
description: EnvironmentVars contains the environment variables on
|
||||
the kube-controllers that influenced the RunningConfig.
|
||||
type: object
|
||||
runningConfig:
|
||||
description: RunningConfig contains the effective config that is running
|
||||
in the kube-controllers pod, after merging the API resource with
|
||||
any environment variables.
|
||||
properties:
|
||||
controllers:
|
||||
description: Controllers enables and configures individual Kubernetes
|
||||
controllers
|
||||
properties:
|
||||
namespace:
|
||||
description: Namespace enables and configures the namespace
|
||||
controller. Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform
|
||||
reconciliation with the Calico datastore. [Default:
|
||||
5m]'
|
||||
type: string
|
||||
type: object
|
||||
node:
|
||||
description: Node enables and configures the node controller.
|
||||
Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
hostEndpoint:
|
||||
description: HostEndpoint controls syncing nodes to host
|
||||
endpoints. Disabled by default, set to nil to disable.
|
||||
properties:
|
||||
autoCreate:
|
||||
description: 'AutoCreate enables automatic creation
|
||||
of host endpoints for every node. [Default: Disabled]'
|
||||
type: string
|
||||
type: object
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform
|
||||
reconciliation with the Calico datastore. [Default:
|
||||
5m]'
|
||||
type: string
|
||||
syncLabels:
|
||||
description: 'SyncLabels controls whether to copy Kubernetes
|
||||
node labels to Calico nodes. [Default: Enabled]'
|
||||
type: string
|
||||
type: object
|
||||
policy:
|
||||
description: Policy enables and configures the policy controller.
|
||||
Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform
|
||||
reconciliation with the Calico datastore. [Default:
|
||||
5m]'
|
||||
type: string
|
||||
type: object
|
||||
serviceAccount:
|
||||
description: ServiceAccount enables and configures the service
|
||||
account controller. Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform
|
||||
reconciliation with the Calico datastore. [Default:
|
||||
5m]'
|
||||
type: string
|
||||
type: object
|
||||
workloadEndpoint:
|
||||
description: WorkloadEndpoint enables and configures the workload
|
||||
endpoint controller. Enabled by default, set to nil to disable.
|
||||
properties:
|
||||
reconcilerPeriod:
|
||||
description: 'ReconcilerPeriod is the period to perform
|
||||
reconciliation with the Calico datastore. [Default:
|
||||
5m]'
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
etcdV3CompactionPeriod:
|
||||
description: 'EtcdV3CompactionPeriod is the period between etcdv3
|
||||
compaction requests. Set to 0 to disable. [Default: 10m]'
|
||||
type: string
|
||||
healthChecks:
|
||||
description: 'HealthChecks enables or disables support for health
|
||||
checks [Default: Enabled]'
|
||||
type: string
|
||||
logSeverityScreen:
|
||||
description: 'LogSeverityScreen is the log severity above which
|
||||
logs are sent to the stdout. [Default: Info]'
|
||||
type: string
|
||||
prometheusMetricsPort:
|
||||
description: 'PrometheusMetricsPort is the TCP port that the Prometheus
|
||||
metrics server should bind to. Set to 0 to disable. [Default:
|
||||
9094]'
|
||||
type: integer
|
||||
required:
|
||||
- controllers
|
||||
type: object
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,750 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: networkpolicies.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: NetworkPolicy
|
||||
listKind: NetworkPolicyList
|
||||
plural: networkpolicies
|
||||
singular: networkpolicy
|
||||
scope: Namespaced
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
properties:
|
||||
egress:
|
||||
description: The ordered set of egress rules. Each rule contains
|
||||
a set of packet match criteria and a corresponding action to apply.
|
||||
items:
|
||||
description: "A Rule encapsulates a set of match criteria and an
|
||||
action. Both selector-based security Policy and security Profiles
|
||||
reference rules - separated out as a list of rules for both ingress
|
||||
and egress packet matching. \n Each positive match criteria has
|
||||
a negated version, prefixed with \"Not\". All the match criteria
|
||||
within a rule must be satisfied for a packet to match. A single
|
||||
rule can contain the positive and negative version of a match
|
||||
and both must be satisfied for the rule to match."
|
||||
properties:
|
||||
action:
|
||||
type: string
|
||||
destination:
|
||||
description: Destination contains the match criteria that apply
|
||||
to destination entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
http:
|
||||
description: HTTP contains match criteria that apply to HTTP
|
||||
requests.
|
||||
properties:
|
||||
methods:
|
||||
description: Methods is an optional field that restricts
|
||||
the rule to apply only to HTTP requests that use one of
|
||||
the listed HTTP Methods (e.g. GET, PUT, etc.) Multiple
|
||||
methods are OR'd together.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
paths:
|
||||
description: 'Paths is an optional field that restricts
|
||||
the rule to apply to HTTP requests that use one of the
|
||||
listed HTTP Paths. Multiple paths are OR''d together.
|
||||
e.g: - exact: /foo - prefix: /bar NOTE: Each entry may
|
||||
ONLY specify either a `exact` or a `prefix` match. The
|
||||
validator will check for it.'
|
||||
items:
|
||||
description: 'HTTPPath specifies an HTTP path to match.
|
||||
It may be either of the form: exact: <path>: which matches
|
||||
the path exactly or prefix: <path-prefix>: which matches
|
||||
the path prefix'
|
||||
properties:
|
||||
exact:
|
||||
type: string
|
||||
prefix:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
icmp:
|
||||
description: ICMP is an optional field that restricts the rule
|
||||
to apply to a specific type and code of ICMP traffic. This
|
||||
should only be specified if the Protocol field is set to "ICMP"
|
||||
or "ICMPv6".
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
ipVersion:
|
||||
description: IPVersion is an optional field that restricts the
|
||||
rule to only match a specific IP version.
|
||||
type: integer
|
||||
metadata:
|
||||
description: Metadata contains additional information for this
|
||||
rule
|
||||
properties:
|
||||
annotations:
|
||||
additionalProperties:
|
||||
type: string
|
||||
description: Annotations is a set of key value pairs that
|
||||
give extra information about the rule
|
||||
type: object
|
||||
type: object
|
||||
notICMP:
|
||||
description: NotICMP is the negated version of the ICMP field.
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
notProtocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: NotProtocol is the negated version of the Protocol
|
||||
field.
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
protocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: "Protocol is an optional field that restricts the
|
||||
rule to only apply to traffic of a specific IP protocol. Required
|
||||
if any of the EntityRules contain Ports (because ports only
|
||||
apply to certain protocols). \n Must be one of these string
|
||||
values: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",
|
||||
\"UDPLite\" or an integer in the range 1-255."
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
source:
|
||||
description: Source contains the match criteria that apply to
|
||||
source entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
required:
|
||||
- action
|
||||
type: object
|
||||
type: array
|
||||
ingress:
|
||||
description: The ordered set of ingress rules. Each rule contains
|
||||
a set of packet match criteria and a corresponding action to apply.
|
||||
items:
|
||||
description: "A Rule encapsulates a set of match criteria and an
|
||||
action. Both selector-based security Policy and security Profiles
|
||||
reference rules - separated out as a list of rules for both ingress
|
||||
and egress packet matching. \n Each positive match criteria has
|
||||
a negated version, prefixed with \"Not\". All the match criteria
|
||||
within a rule must be satisfied for a packet to match. A single
|
||||
rule can contain the positive and negative version of a match
|
||||
and both must be satisfied for the rule to match."
|
||||
properties:
|
||||
action:
|
||||
type: string
|
||||
destination:
|
||||
description: Destination contains the match criteria that apply
|
||||
to destination entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
http:
|
||||
description: HTTP contains match criteria that apply to HTTP
|
||||
requests.
|
||||
properties:
|
||||
methods:
|
||||
description: Methods is an optional field that restricts
|
||||
the rule to apply only to HTTP requests that use one of
|
||||
the listed HTTP Methods (e.g. GET, PUT, etc.) Multiple
|
||||
methods are OR'd together.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
paths:
|
||||
description: 'Paths is an optional field that restricts
|
||||
the rule to apply to HTTP requests that use one of the
|
||||
listed HTTP Paths. Multiple paths are OR''d together.
|
||||
e.g: - exact: /foo - prefix: /bar NOTE: Each entry may
|
||||
ONLY specify either a `exact` or a `prefix` match. The
|
||||
validator will check for it.'
|
||||
items:
|
||||
description: 'HTTPPath specifies an HTTP path to match.
|
||||
It may be either of the form: exact: <path>: which matches
|
||||
the path exactly or prefix: <path-prefix>: which matches
|
||||
the path prefix'
|
||||
properties:
|
||||
exact:
|
||||
type: string
|
||||
prefix:
|
||||
type: string
|
||||
type: object
|
||||
type: array
|
||||
type: object
|
||||
icmp:
|
||||
description: ICMP is an optional field that restricts the rule
|
||||
to apply to a specific type and code of ICMP traffic. This
|
||||
should only be specified if the Protocol field is set to "ICMP"
|
||||
or "ICMPv6".
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
ipVersion:
|
||||
description: IPVersion is an optional field that restricts the
|
||||
rule to only match a specific IP version.
|
||||
type: integer
|
||||
metadata:
|
||||
description: Metadata contains additional information for this
|
||||
rule
|
||||
properties:
|
||||
annotations:
|
||||
additionalProperties:
|
||||
type: string
|
||||
description: Annotations is a set of key value pairs that
|
||||
give extra information about the rule
|
||||
type: object
|
||||
type: object
|
||||
notICMP:
|
||||
description: NotICMP is the negated version of the ICMP field.
|
||||
properties:
|
||||
code:
|
||||
description: Match on a specific ICMP code. If specified,
|
||||
the Type value must also be specified. This is a technical
|
||||
limitation imposed by the kernel's iptables firewall,
|
||||
which Calico uses to enforce the rule.
|
||||
type: integer
|
||||
type:
|
||||
description: Match on a specific ICMP type. For example
|
||||
a value of 8 refers to ICMP Echo Request (i.e. pings).
|
||||
type: integer
|
||||
type: object
|
||||
notProtocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: NotProtocol is the negated version of the Protocol
|
||||
field.
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
protocol:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
description: "Protocol is an optional field that restricts the
|
||||
rule to only apply to traffic of a specific IP protocol. Required
|
||||
if any of the EntityRules contain Ports (because ports only
|
||||
apply to certain protocols). \n Must be one of these string
|
||||
values: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",
|
||||
\"UDPLite\" or an integer in the range 1-255."
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
source:
|
||||
description: Source contains the match criteria that apply to
|
||||
source entity.
|
||||
properties:
|
||||
namespaceSelector:
|
||||
description: "NamespaceSelector is an optional field that
|
||||
contains a selector expression. Only traffic that originates
|
||||
from (or terminates at) endpoints within the selected
|
||||
namespaces will be matched. When both NamespaceSelector
|
||||
and Selector are defined on the same rule, then only workload
|
||||
endpoints that are matched by both selectors will be selected
|
||||
by the rule. \n For NetworkPolicy, an empty NamespaceSelector
|
||||
implies that the Selector is limited to selecting only
|
||||
workload endpoints in the same namespace as the NetworkPolicy.
|
||||
\n For NetworkPolicy, `global()` NamespaceSelector implies
|
||||
that the Selector is limited to selecting only GlobalNetworkSet
|
||||
or HostEndpoint. \n For GlobalNetworkPolicy, an empty
|
||||
NamespaceSelector implies the Selector applies to workload
|
||||
endpoints across all namespaces."
|
||||
type: string
|
||||
nets:
|
||||
description: Nets is an optional field that restricts the
|
||||
rule to only apply to traffic that originates from (or
|
||||
terminates at) IP addresses in any of the given subnets.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notNets:
|
||||
description: NotNets is the negated version of the Nets
|
||||
field.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
notPorts:
|
||||
description: NotPorts is the negated version of the Ports
|
||||
field. Since only some protocols have ports, if any ports
|
||||
are specified it requires the Protocol match in the Rule
|
||||
to be set to "TCP" or "UDP".
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
notSelector:
|
||||
description: NotSelector is the negated version of the Selector
|
||||
field. See Selector field for subtleties with negated
|
||||
selectors.
|
||||
type: string
|
||||
ports:
|
||||
description: "Ports is an optional field that restricts
|
||||
the rule to only apply to traffic that has a source (destination)
|
||||
port that matches one of these ranges/values. This value
|
||||
is a list of integers or strings that represent ranges
|
||||
of ports. \n Since only some protocols have ports, if
|
||||
any ports are specified it requires the Protocol match
|
||||
in the Rule to be set to \"TCP\" or \"UDP\"."
|
||||
items:
|
||||
anyOf:
|
||||
- type: integer
|
||||
- type: string
|
||||
pattern: ^.*
|
||||
x-kubernetes-int-or-string: true
|
||||
type: array
|
||||
selector:
|
||||
description: "Selector is an optional field that contains
|
||||
a selector expression (see Policy for sample syntax).
|
||||
\ Only traffic that originates from (terminates at) endpoints
|
||||
matching the selector will be matched. \n Note that: in
|
||||
addition to the negated version of the Selector (see NotSelector
|
||||
below), the selector expression syntax itself supports
|
||||
negation. The two types of negation are subtly different.
|
||||
One negates the set of matched endpoints, the other negates
|
||||
the whole match: \n \tSelector = \"!has(my_label)\" matches
|
||||
packets that are from other Calico-controlled \tendpoints
|
||||
that do not have the label \"my_label\". \n \tNotSelector
|
||||
= \"has(my_label)\" matches packets that are not from
|
||||
Calico-controlled \tendpoints that do have the label \"my_label\".
|
||||
\n The effect is that the latter will accept packets from
|
||||
non-Calico sources whereas the former is limited to packets
|
||||
from Calico-controlled endpoints."
|
||||
type: string
|
||||
serviceAccounts:
|
||||
description: ServiceAccounts is an optional field that restricts
|
||||
the rule to only apply to traffic that originates from
|
||||
(or terminates at) a pod running as a matching service
|
||||
account.
|
||||
properties:
|
||||
names:
|
||||
description: Names is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account whose name is in the list.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
selector:
|
||||
description: Selector is an optional field that restricts
|
||||
the rule to only apply to traffic that originates
|
||||
from (or terminates at) a pod running as a service
|
||||
account that matches the given label selector. If
|
||||
both Names and Selector are specified then they are
|
||||
AND'ed.
|
||||
type: string
|
||||
type: object
|
||||
type: object
|
||||
required:
|
||||
- action
|
||||
type: object
|
||||
type: array
|
||||
order:
|
||||
description: Order is an optional field that specifies the order in
|
||||
which the policy is applied. Policies with higher "order" are applied
|
||||
after those with lower order. If the order is omitted, it may be
|
||||
considered to be "infinite" - i.e. the policy will be applied last. Policies
|
||||
with identical order will be applied in alphanumerical order based
|
||||
on the Policy "Name".
|
||||
type: number
|
||||
selector:
|
||||
description: "The selector is an expression used to pick pick out
|
||||
the endpoints that the policy should be applied to. \n Selector
|
||||
expressions follow this syntax: \n \tlabel == \"string_literal\"
|
||||
\ -> comparison, e.g. my_label == \"foo bar\" \tlabel != \"string_literal\"
|
||||
\ -> not equal; also matches if label is not present \tlabel in
|
||||
{ \"a\", \"b\", \"c\", ... } -> true if the value of label X is
|
||||
one of \"a\", \"b\", \"c\" \tlabel not in { \"a\", \"b\", \"c\",
|
||||
... } -> true if the value of label X is not one of \"a\", \"b\",
|
||||
\"c\" \thas(label_name) -> True if that label is present \t! expr
|
||||
-> negation of expr \texpr && expr -> Short-circuit and \texpr
|
||||
|| expr -> Short-circuit or \t( expr ) -> parens for grouping \tall()
|
||||
or the empty selector -> matches all endpoints. \n Label names are
|
||||
allowed to contain alphanumerics, -, _ and /. String literals are
|
||||
more permissive but they do not support escape characters. \n Examples
|
||||
(with made-up labels): \n \ttype == \"webserver\" && deployment
|
||||
== \"prod\" \ttype in {\"frontend\", \"backend\"} \tdeployment !=
|
||||
\"dev\" \t! has(label_name)"
|
||||
type: string
|
||||
serviceAccountSelector:
|
||||
description: ServiceAccountSelector is an optional field for an expression
|
||||
used to select a pod based on service accounts.
|
||||
type: string
|
||||
types:
|
||||
description: "Types indicates whether this policy applies to ingress,
|
||||
or to egress, or to both. When not explicitly specified (and so
|
||||
the value on creation is empty or nil), Calico defaults Types according
|
||||
to what Ingress and Egress are present in the policy. The default
|
||||
is: \n - [ PolicyTypeIngress ], if there are no Egress rules (including
|
||||
the case where there are also no Ingress rules) \n - [ PolicyTypeEgress
|
||||
], if there are Egress rules but no Ingress rules \n - [ PolicyTypeIngress,
|
||||
PolicyTypeEgress ], if there are both Ingress and Egress rules.
|
||||
\n When the policy is read back again, Types will always be one
|
||||
of these values, never empty or nil."
|
||||
items:
|
||||
description: PolicyType enumerates the possible values of the PolicySpec
|
||||
Types field.
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,49 @@
|
|||
apiVersion: apiextensions.k8s.io/v1
|
||||
kind: CustomResourceDefinition
|
||||
metadata:
|
||||
name: networksets.crd.projectcalico.org
|
||||
spec:
|
||||
group: crd.projectcalico.org
|
||||
names:
|
||||
kind: NetworkSet
|
||||
listKind: NetworkSetList
|
||||
plural: networksets
|
||||
singular: networkset
|
||||
scope: Namespaced
|
||||
versions:
|
||||
- name: v1
|
||||
schema:
|
||||
openAPIV3Schema:
|
||||
description: NetworkSet is the Namespaced-equivalent of the GlobalNetworkSet.
|
||||
properties:
|
||||
apiVersion:
|
||||
description: 'APIVersion defines the versioned schema of this representation
|
||||
of an object. Servers should convert recognized schemas to the latest
|
||||
internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'
|
||||
type: string
|
||||
kind:
|
||||
description: 'Kind is a string value representing the REST resource this
|
||||
object represents. Servers may infer this from the endpoint the client
|
||||
submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'
|
||||
type: string
|
||||
metadata:
|
||||
type: object
|
||||
spec:
|
||||
description: NetworkSetSpec contains the specification for a NetworkSet
|
||||
resource.
|
||||
properties:
|
||||
nets:
|
||||
description: The list of IP networks that belong to this set.
|
||||
items:
|
||||
type: string
|
||||
type: array
|
||||
type: object
|
||||
type: object
|
||||
served: true
|
||||
storage: true
|
||||
status:
|
||||
acceptedNames:
|
||||
kind: ""
|
||||
plural: ""
|
||||
conditions: []
|
||||
storedVersions: []
|
||||
|
|
@ -0,0 +1,21 @@
|
|||
{{ if .Values.installation.enabled }}
|
||||
{{ $installSpec := omit .Values.installation "enabled" }}
|
||||
{{ $secrets := list }}
|
||||
{{ range $name := keys .Values.imagePullSecrets -}}
|
||||
{{ $item := dict "name" $name }}
|
||||
{{ $secrets = append $secrets $item }}
|
||||
{{ end }}
|
||||
{{ $_ := set $installSpec "imagePullSecrets" $secrets }}
|
||||
{{ $defaultipPools := get .Values.installation.calicoNetwork "ipPools" | first }}
|
||||
{{ $defaultCIDR := get $defaultipPools "cidr" }}
|
||||
{{ $finalCIDR := coalesce .Values.global.clusterCIDR $defaultCIDR }}
|
||||
{{ $_ := set $defaultipPools "cidr" $finalCIDR }}
|
||||
|
||||
apiVersion: operator.tigera.io/v1
|
||||
kind: Installation
|
||||
metadata:
|
||||
name: default
|
||||
spec:
|
||||
{{ $installSpec | toYaml | indent 2 }}
|
||||
|
||||
{{ end }}
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
apiVersion: v1
|
||||
kind: Namespace
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
annotations:
|
||||
{{- if eq .Values.installation.kubernetesProvider "openshift" }}
|
||||
openshift.io/node-selector: ""
|
||||
{{- end }}
|
||||
labels:
|
||||
name: tigera-operator
|
||||
{{- if eq .Values.installation.kubernetesProvider "openshift" }}
|
||||
openshift.io/run-level: "0"
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,15 @@
|
|||
{{- $envAll := . }}
|
||||
{{- if .Values.imagePullSecrets -}}
|
||||
|
||||
{{range $key, $value := .Values.imagePullSecrets -}}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: {{ $key }}
|
||||
namespace: tigera-operator
|
||||
data:
|
||||
.dockerconfigjson: {{ $value | b64enc }}
|
||||
type: kubernetes.io/dockerconfigjson
|
||||
{{- end -}}
|
||||
|
||||
{{- end -}}
|
||||
|
|
@ -0,0 +1,27 @@
|
|||
{{- if eq .Values.installation.kubernetesProvider "openshift" }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: calico-resources
|
||||
namespace: tigera-operator
|
||||
data:
|
||||
# To create Calico resources before Calico components are started add
|
||||
# an entry here and the contents of the resource under the entry.
|
||||
# The resources here should all be projectcalico.org/v3.
|
||||
# Multiple resources/entries can be added to this ConfigMap.
|
||||
#
|
||||
# If you need to remove a resource that was added to this ConfigMap
|
||||
# you should remove it from here or else it will be re-created.
|
||||
#
|
||||
# example-global-network-set.yaml: |
|
||||
# apiVersion: projectcalico.org/v3
|
||||
# kind: GlobalNetworkSet
|
||||
# metadata:
|
||||
# name: a-name-for-the-set
|
||||
# labels:
|
||||
# role: external-database
|
||||
# spec:
|
||||
# nets:
|
||||
# - 198.51.100.0/28
|
||||
# - 203.0.113.0/24
|
||||
{{- end}}
|
||||
|
|
@ -0,0 +1,47 @@
|
|||
{{ if ne .Values.installation.kubernetesProvider "openshift" }}
|
||||
# This should not be rendered for an OpenShift install.
|
||||
# OpenShift uses SecurityContextConstraints instead.
|
||||
apiVersion: policy/v1beta1
|
||||
kind: PodSecurityPolicy
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
annotations:
|
||||
seccomp.security.alpha.kubernetes.io/allowedProfileNames: '*'
|
||||
spec:
|
||||
privileged: false
|
||||
allowPrivilegeEscalation: false
|
||||
requiredDropCapabilities:
|
||||
- ALL
|
||||
volumes:
|
||||
- 'hostPath'
|
||||
- 'configMap'
|
||||
- 'emptyDir'
|
||||
- 'projected'
|
||||
- 'secret'
|
||||
- 'downwardAPI'
|
||||
# Assume that persistentVolumes set up by the cluster admin are safe to use.
|
||||
- 'persistentVolumeClaim'
|
||||
hostNetwork: true
|
||||
hostPorts:
|
||||
- min: 0
|
||||
max: 65535
|
||||
hostIPC: false
|
||||
hostPID: false
|
||||
runAsUser:
|
||||
rule: 'MustRunAsNonRoot'
|
||||
seLinux:
|
||||
rule: 'RunAsAny'
|
||||
supplementalGroups:
|
||||
rule: 'MustRunAs'
|
||||
ranges:
|
||||
# Forbid adding the root group.
|
||||
- min: 1
|
||||
max: 65535
|
||||
fsGroup:
|
||||
rule: 'MustRunAs'
|
||||
ranges:
|
||||
# Forbid adding the root group.
|
||||
- min: 1
|
||||
max: 65535
|
||||
readOnlyRootFilesystem: false
|
||||
{{ end }}
|
||||
|
|
@ -0,0 +1,250 @@
|
|||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- namespaces
|
||||
- pods
|
||||
- podtemplates
|
||||
- services
|
||||
- endpoints
|
||||
- events
|
||||
- configmaps
|
||||
- secrets
|
||||
- serviceaccounts
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
verbs:
|
||||
# Need to update node labels when migrating nodes.
|
||||
- 'get'
|
||||
- 'patch'
|
||||
- 'list'
|
||||
# We need this for Typha autoscaling
|
||||
- 'watch'
|
||||
- apiGroups:
|
||||
- rbac.authorization.k8s.io
|
||||
resources:
|
||||
- clusterroles
|
||||
- clusterrolebindings
|
||||
- rolebindings
|
||||
- roles
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
- bind
|
||||
- escalate
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- deployments
|
||||
- daemonsets
|
||||
- statefulsets
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apps
|
||||
resourceNames:
|
||||
- tigera-operator
|
||||
resources:
|
||||
- deployments/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- operator.tigera.io
|
||||
resources:
|
||||
- '*'
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- patch
|
||||
- delete
|
||||
- watch
|
||||
- apiGroups:
|
||||
- crd.projectcalico.org
|
||||
resources:
|
||||
- felixconfigurations
|
||||
verbs:
|
||||
- patch
|
||||
- apiGroups:
|
||||
- crd.projectcalico.org
|
||||
resources:
|
||||
- ippools
|
||||
- kubecontrollersconfigurations
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- scheduling.k8s.io
|
||||
resources:
|
||||
- priorityclasses
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
- apiGroups:
|
||||
- monitoring.coreos.com
|
||||
resources:
|
||||
- servicemonitors
|
||||
verbs:
|
||||
- get
|
||||
- create
|
||||
- apiGroups:
|
||||
- policy
|
||||
resources:
|
||||
- poddisruptionbudgets
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apiregistration.k8s.io
|
||||
resources:
|
||||
- apiservices
|
||||
verbs:
|
||||
- list
|
||||
- watch
|
||||
# Needed for operator lock
|
||||
- apiGroups:
|
||||
- coordination.k8s.io
|
||||
resources:
|
||||
- leases
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
{{- if eq .Values.installation.kubernetesProvider "openshift" }}
|
||||
# When running in OpenShift, we need to update networking config.
|
||||
- apiGroups:
|
||||
- config.openshift.io
|
||||
resources:
|
||||
- networks/status
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- apiGroups:
|
||||
- config.openshift.io
|
||||
resources:
|
||||
- networks
|
||||
- infrastructures
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
# On OpenShift, we need to modify SCCs.
|
||||
- apiGroups:
|
||||
- security.openshift.io
|
||||
resources:
|
||||
- securitycontextconstraints
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- delete
|
||||
- watch
|
||||
# For host network access.
|
||||
- apiGroups:
|
||||
- security.openshift.io
|
||||
resources:
|
||||
- securitycontextconstraints
|
||||
resourceNames:
|
||||
- hostnetwork
|
||||
verbs:
|
||||
- use
|
||||
# Need these permissions for the calicoctl init container.
|
||||
- apiGroups:
|
||||
- crd.projectcalico.org
|
||||
resources:
|
||||
- bgpconfigurations
|
||||
- bgppeers
|
||||
- felixconfigurations
|
||||
- kubecontrollersconfigurations
|
||||
- globalnetworkpolicies
|
||||
- globalnetworksets
|
||||
- hostendpoints
|
||||
- ippools
|
||||
- networkpolicies
|
||||
- networksets
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- crd.projectcalico.org
|
||||
resources:
|
||||
- ipamblocks
|
||||
verbs:
|
||||
- list
|
||||
# For AWS security group setup.
|
||||
- apiGroups:
|
||||
- batch
|
||||
resources:
|
||||
- jobs
|
||||
- cronjobs
|
||||
verbs:
|
||||
- create
|
||||
- update
|
||||
- list
|
||||
- watch
|
||||
{{- else }}
|
||||
# Add the appropriate pod security policy permissions
|
||||
- apiGroups:
|
||||
- policy
|
||||
resources:
|
||||
- podsecuritypolicies
|
||||
resourceNames:
|
||||
- tigera-operator
|
||||
verbs:
|
||||
- use
|
||||
- apiGroups:
|
||||
- policy
|
||||
resources:
|
||||
- podsecuritypolicies
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- create
|
||||
- update
|
||||
# Add the permissions to monitor the status of certificatesigningrequests when certificate management is enabled.
|
||||
- apiGroups:
|
||||
- certificates.k8s.io
|
||||
resources:
|
||||
- certificatesigningrequests
|
||||
verbs:
|
||||
- list
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,12 @@
|
|||
kind: ClusterRoleBinding
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: tigera-operator
|
||||
namespace: tigera-operator
|
||||
roleRef:
|
||||
kind: ClusterRole
|
||||
name: tigera-operator
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
|
|
@ -0,0 +1,5 @@
|
|||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
namespace: tigera-operator
|
||||
|
|
@ -0,0 +1,85 @@
|
|||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: tigera-operator
|
||||
namespace: tigera-operator
|
||||
labels:
|
||||
k8s-app: tigera-operator
|
||||
spec:
|
||||
replicas: 1
|
||||
selector:
|
||||
matchLabels:
|
||||
name: tigera-operator
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
name: tigera-operator
|
||||
k8s-app: tigera-operator
|
||||
spec:
|
||||
nodeSelector:
|
||||
kubernetes.io/os: linux
|
||||
tolerations:
|
||||
- effect: NoExecute
|
||||
operator: Exists
|
||||
- effect: NoSchedule
|
||||
operator: Exists
|
||||
serviceAccountName: tigera-operator
|
||||
hostNetwork: true
|
||||
# This must be set when hostNetwork is true or else the cluster services won't resolve
|
||||
dnsPolicy: ClusterFirstWithHostNet
|
||||
containers:
|
||||
- name: tigera-operator
|
||||
image: {{ template "tigera-operator.image" . }}
|
||||
imagePullPolicy: IfNotPresent
|
||||
command:
|
||||
- operator
|
||||
volumeMounts:
|
||||
- name: var-lib-calico
|
||||
readOnly: true
|
||||
mountPath: /var/lib/calico
|
||||
env:
|
||||
- name: WATCH_NAMESPACE
|
||||
value: ""
|
||||
- name: POD_NAME
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: metadata.name
|
||||
- name: OPERATOR_NAME
|
||||
value: "tigera-operator"
|
||||
- name: TIGERA_OPERATOR_INIT_IMAGE_VERSION
|
||||
value: {{.Values.tigeraOperator.version}}
|
||||
envFrom:
|
||||
- configMapRef:
|
||||
name: kubernetes-services-endpoint
|
||||
optional: true
|
||||
volumes:
|
||||
- name: var-lib-calico
|
||||
hostPath:
|
||||
path: /var/lib/calico
|
||||
{{- if eq .Values.installation.kubernetesProvider "openshift" }}
|
||||
- name: calico-resources
|
||||
configMap:
|
||||
defaultMode: 0400
|
||||
name: calico-resources
|
||||
- name: install-resources-script
|
||||
configMap:
|
||||
defaultMode: 0777
|
||||
name: install-resources-script
|
||||
initContainers:
|
||||
- name: create-initial-resources
|
||||
image: {{.Values.calicoctl.image}}:{{.Values.calicoctl.tag}}
|
||||
env:
|
||||
- name: DATASTORE_TYPE
|
||||
value: kubernetes
|
||||
command:
|
||||
- calicoctl
|
||||
args:
|
||||
- create
|
||||
- --skip-exists
|
||||
- --skip-empty
|
||||
- -f
|
||||
- /calico-resources
|
||||
volumeMounts:
|
||||
- name: calico-resources
|
||||
mountPath: /calico-resources
|
||||
{{- end}}
|
||||
|
|
@ -0,0 +1,16 @@
|
|||
#{{- if gt (len (lookup "rbac.authorization.k8s.io/v1" "ClusterRole" "" "")) 0 -}}
|
||||
# {{- $found := dict -}}
|
||||
# {{- set $found "operator.tigera.io/v1/ImageSet" false -}}
|
||||
# {{- set $found "operator.tigera.io/v1/Installation" false -}}
|
||||
# {{- set $found "operator.tigera.io/v1/TigeraStatus" false -}}
|
||||
# {{- range .Capabilities.APIVersions -}}
|
||||
# {{- if hasKey $found (toString .) -}}
|
||||
# {{- set $found (toString .) true -}}
|
||||
# {{- end -}}
|
||||
# {{- end -}}
|
||||
# {{- range $_, $exists := $found -}}
|
||||
# {{- if (eq $exists false) -}}
|
||||
# {{- required "Required CRDs are missing. Please install the corresponding CRD chart before installing this chart." "" -}}
|
||||
# {{- end -}}
|
||||
# {{- end -}}
|
||||
#{{- end -}}
|
||||
|
|
@ -0,0 +1,41 @@
|
|||
imagePullSecrets: {}
|
||||
|
||||
installation:
|
||||
controlPlaneTolerations:
|
||||
- key: "node-role.kubernetes.io/control-plane"
|
||||
operator: "Exists"
|
||||
effect: "NoSchedule"
|
||||
- key: "node-role.kubernetes.io/etcd"
|
||||
operator: "Exists"
|
||||
effect: "NoExecute"
|
||||
enabled: true
|
||||
kubernetesProvider: ""
|
||||
calicoNetwork:
|
||||
bgp: Disabled
|
||||
ipPools:
|
||||
- natOutgoing: Enabled
|
||||
encapsulation: VXLAN
|
||||
cidr: 10.42.0.0/16
|
||||
|
||||
certs:
|
||||
node:
|
||||
key:
|
||||
cert:
|
||||
commonName:
|
||||
typha:
|
||||
key:
|
||||
cert:
|
||||
commonName:
|
||||
caBundle:
|
||||
|
||||
# Configuration for the tigera operator
|
||||
tigeraOperator:
|
||||
image: rancher/mirrored-calico-operator
|
||||
version: v1.17.2
|
||||
registry: docker.io
|
||||
calicoctl:
|
||||
image: rancher/mirrored-calico-ctl
|
||||
tag: v3.19.1
|
||||
|
||||
global:
|
||||
systemDefaultRegistry: ""
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
apiVersion: v1
|
||||
description: eBPF-based Networking, Security, and Observability
|
||||
home: https://cilium.io/
|
||||
keywords:
|
||||
- cilium
|
||||
kubeVersion: '>= 1.12.0-0'
|
||||
maintainers:
|
||||
- email: charts@rancher.com
|
||||
name: Rancher Labs
|
||||
name: rke2-cilium
|
||||
sources:
|
||||
- https://github.com/rancher/rke2-charts
|
||||
version: 1.9.607
|
||||
|
|
@ -0,0 +1,23 @@
|
|||
# Patterns to ignore when building packages.
|
||||
# This supports shell glob matching, relative path matching, and
|
||||
# negation (prefixed with !). Only one pattern per line.
|
||||
.DS_Store
|
||||
# Common VCS dirs
|
||||
.git/
|
||||
.gitignore
|
||||
.bzr/
|
||||
.bzrignore
|
||||
.hg/
|
||||
.hgignore
|
||||
.svn/
|
||||
# Common backup files
|
||||
*.swp
|
||||
*.bak
|
||||
*.tmp
|
||||
*.orig
|
||||
*~
|
||||
# Various IDEs
|
||||
.project
|
||||
.idea/
|
||||
*.tmproj
|
||||
.vscode/
|
||||
|
|
@ -0,0 +1,73 @@
|
|||
annotations:
|
||||
artifacthub.io/crds: |
|
||||
- kind: CiliumNetworkPolicy
|
||||
version: v2
|
||||
name: ciliumnetworkpolicy
|
||||
displayName: Cilium Network Policy
|
||||
description: |
|
||||
Cilium Network Policies provide additional functionality beyond what
|
||||
is provided by standard Kubernetes NetworkPolicy such as the ability
|
||||
to allow traffic based on FQDNs, or to filter at Layer 7.
|
||||
- kind: CiliumClusterwideNetworkPolicy
|
||||
version: v2
|
||||
name: ciliumclusterwidenetworkpolicy
|
||||
displayName: Cilium Clusterwide Network Policy
|
||||
description: |
|
||||
Cilium Clusterwide Network Policies support configuring network traffic
|
||||
policiies across the entire cluster, including applying node firewalls.
|
||||
- kind: CiliumExternalWorkload
|
||||
version: v2
|
||||
name: ciliumnetworkpolicy
|
||||
displayName: Cilium External Workload
|
||||
description: |
|
||||
Cilium External Workload supports configuring the ability for external
|
||||
non-Kubernetes workloads to join the cluster.
|
||||
- kind: CiliumLocalRedirectPolicy
|
||||
version: v2
|
||||
name: ciliumlocalredirectpolicy
|
||||
displayName: Cilium Local Redirect Policy
|
||||
description: |
|
||||
Cilium Local Redirect Policy allows local redirects to be configured
|
||||
within a node to support use cases like Node-Local DNS or KIAM.
|
||||
- kind: CiliumNode
|
||||
version: v2
|
||||
name: ciliumnode
|
||||
displayName: Cilium Node
|
||||
description: |
|
||||
Cilium Node represents a node managed by Cilium. It contains a
|
||||
specification to control various node specific configuration aspects
|
||||
and a status section to represent the status of the node.
|
||||
- kind: CiliumIdentity
|
||||
version: v2
|
||||
name: ciliumidentity
|
||||
displayName: Cilium Identity
|
||||
description: |
|
||||
Cilium Identity allows introspection into security identities that
|
||||
Cilium allocates which identify sets of labels that are assigned to
|
||||
individual endpoints in the cluster.
|
||||
- kind: CiliumEndpoint
|
||||
version: v2
|
||||
name: ciliumendpoint
|
||||
displayName: Cilium Endpoint
|
||||
description: |
|
||||
Cilium Endpoint represents the status of individual pods or nodes in
|
||||
the cluster which are managed by Cilium, including enforcement status,
|
||||
IP addressing and whether the networking is succesfully operational.
|
||||
apiVersion: v2
|
||||
appVersion: 1.9.6
|
||||
description: eBPF-based Networking, Security, and Observability
|
||||
home: https://cilium.io/
|
||||
icon: https://cdn.jsdelivr.net/gh/cilium/cilium@v1.9.6/Documentation/images/logo-solo.svg
|
||||
keywords:
|
||||
- BPF
|
||||
- eBPF
|
||||
- Kubernetes
|
||||
- Networking
|
||||
- Security
|
||||
- Observability
|
||||
- Troubleshooting
|
||||
kubeVersion: '>= 1.12.0-0'
|
||||
name: cilium
|
||||
sources:
|
||||
- https://github.com/cilium/cilium
|
||||
version: 1.9.6
|
||||
|
|
@ -0,0 +1,202 @@
|
|||
Apache License
|
||||
Version 2.0, January 2004
|
||||
http://www.apache.org/licenses/
|
||||
|
||||
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
|
||||
|
||||
1. Definitions.
|
||||
|
||||
"License" shall mean the terms and conditions for use, reproduction,
|
||||
and distribution as defined by Sections 1 through 9 of this document.
|
||||
|
||||
"Licensor" shall mean the copyright owner or entity authorized by
|
||||
the copyright owner that is granting the License.
|
||||
|
||||
"Legal Entity" shall mean the union of the acting entity and all
|
||||
other entities that control, are controlled by, or are under common
|
||||
control with that entity. For the purposes of this definition,
|
||||
"control" means (i) the power, direct or indirect, to cause the
|
||||
direction or management of such entity, whether by contract or
|
||||
otherwise, or (ii) ownership of fifty percent (50%) or more of the
|
||||
outstanding shares, or (iii) beneficial ownership of such entity.
|
||||
|
||||
"You" (or "Your") shall mean an individual or Legal Entity
|
||||
exercising permissions granted by this License.
|
||||
|
||||
"Source" form shall mean the preferred form for making modifications,
|
||||
including but not limited to software source code, documentation
|
||||
source, and configuration files.
|
||||
|
||||
"Object" form shall mean any form resulting from mechanical
|
||||
transformation or translation of a Source form, including but
|
||||
not limited to compiled object code, generated documentation,
|
||||
and conversions to other media types.
|
||||
|
||||
"Work" shall mean the work of authorship, whether in Source or
|
||||
Object form, made available under the License, as indicated by a
|
||||
copyright notice that is included in or attached to the work
|
||||
(an example is provided in the Appendix below).
|
||||
|
||||
"Derivative Works" shall mean any work, whether in Source or Object
|
||||
form, that is based on (or derived from) the Work and for which the
|
||||
editorial revisions, annotations, elaborations, or other modifications
|
||||
represent, as a whole, an original work of authorship. For the purposes
|
||||
of this License, Derivative Works shall not include works that remain
|
||||
separable from, or merely link (or bind by name) to the interfaces of,
|
||||
the Work and Derivative Works thereof.
|
||||
|
||||
"Contribution" shall mean any work of authorship, including
|
||||
the original version of the Work and any modifications or additions
|
||||
to that Work or Derivative Works thereof, that is intentionally
|
||||
submitted to Licensor for inclusion in the Work by the copyright owner
|
||||
or by an individual or Legal Entity authorized to submit on behalf of
|
||||
the copyright owner. For the purposes of this definition, "submitted"
|
||||
means any form of electronic, verbal, or written communication sent
|
||||
to the Licensor or its representatives, including but not limited to
|
||||
communication on electronic mailing lists, source code control systems,
|
||||
and issue tracking systems that are managed by, or on behalf of, the
|
||||
Licensor for the purpose of discussing and improving the Work, but
|
||||
excluding communication that is conspicuously marked or otherwise
|
||||
designated in writing by the copyright owner as "Not a Contribution."
|
||||
|
||||
"Contributor" shall mean Licensor and any individual or Legal Entity
|
||||
on behalf of whom a Contribution has been received by Licensor and
|
||||
subsequently incorporated within the Work.
|
||||
|
||||
2. Grant of Copyright License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
copyright license to reproduce, prepare Derivative Works of,
|
||||
publicly display, publicly perform, sublicense, and distribute the
|
||||
Work and such Derivative Works in Source or Object form.
|
||||
|
||||
3. Grant of Patent License. Subject to the terms and conditions of
|
||||
this License, each Contributor hereby grants to You a perpetual,
|
||||
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
|
||||
(except as stated in this section) patent license to make, have made,
|
||||
use, offer to sell, sell, import, and otherwise transfer the Work,
|
||||
where such license applies only to those patent claims licensable
|
||||
by such Contributor that are necessarily infringed by their
|
||||
Contribution(s) alone or by combination of their Contribution(s)
|
||||
with the Work to which such Contribution(s) was submitted. If You
|
||||
institute patent litigation against any entity (including a
|
||||
cross-claim or counterclaim in a lawsuit) alleging that the Work
|
||||
or a Contribution incorporated within the Work constitutes direct
|
||||
or contributory patent infringement, then any patent licenses
|
||||
granted to You under this License for that Work shall terminate
|
||||
as of the date such litigation is filed.
|
||||
|
||||
4. Redistribution. You may reproduce and distribute copies of the
|
||||
Work or Derivative Works thereof in any medium, with or without
|
||||
modifications, and in Source or Object form, provided that You
|
||||
meet the following conditions:
|
||||
|
||||
(a) You must give any other recipients of the Work or
|
||||
Derivative Works a copy of this License; and
|
||||
|
||||
(b) You must cause any modified files to carry prominent notices
|
||||
stating that You changed the files; and
|
||||
|
||||
(c) You must retain, in the Source form of any Derivative Works
|
||||
that You distribute, all copyright, patent, trademark, and
|
||||
attribution notices from the Source form of the Work,
|
||||
excluding those notices that do not pertain to any part of
|
||||
the Derivative Works; and
|
||||
|
||||
(d) If the Work includes a "NOTICE" text file as part of its
|
||||
distribution, then any Derivative Works that You distribute must
|
||||
include a readable copy of the attribution notices contained
|
||||
within such NOTICE file, excluding those notices that do not
|
||||
pertain to any part of the Derivative Works, in at least one
|
||||
of the following places: within a NOTICE text file distributed
|
||||
as part of the Derivative Works; within the Source form or
|
||||
documentation, if provided along with the Derivative Works; or,
|
||||
within a display generated by the Derivative Works, if and
|
||||
wherever such third-party notices normally appear. The contents
|
||||
of the NOTICE file are for informational purposes only and
|
||||
do not modify the License. You may add Your own attribution
|
||||
notices within Derivative Works that You distribute, alongside
|
||||
or as an addendum to the NOTICE text from the Work, provided
|
||||
that such additional attribution notices cannot be construed
|
||||
as modifying the License.
|
||||
|
||||
You may add Your own copyright statement to Your modifications and
|
||||
may provide additional or different license terms and conditions
|
||||
for use, reproduction, or distribution of Your modifications, or
|
||||
for any such Derivative Works as a whole, provided Your use,
|
||||
reproduction, and distribution of the Work otherwise complies with
|
||||
the conditions stated in this License.
|
||||
|
||||
5. Submission of Contributions. Unless You explicitly state otherwise,
|
||||
any Contribution intentionally submitted for inclusion in the Work
|
||||
by You to the Licensor shall be under the terms and conditions of
|
||||
this License, without any additional terms or conditions.
|
||||
Notwithstanding the above, nothing herein shall supersede or modify
|
||||
the terms of any separate license agreement you may have executed
|
||||
with Licensor regarding such Contributions.
|
||||
|
||||
6. Trademarks. This License does not grant permission to use the trade
|
||||
names, trademarks, service marks, or product names of the Licensor,
|
||||
except as required for reasonable and customary use in describing the
|
||||
origin of the Work and reproducing the content of the NOTICE file.
|
||||
|
||||
7. Disclaimer of Warranty. Unless required by applicable law or
|
||||
agreed to in writing, Licensor provides the Work (and each
|
||||
Contributor provides its Contributions) on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
|
||||
implied, including, without limitation, any warranties or conditions
|
||||
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
|
||||
PARTICULAR PURPOSE. You are solely responsible for determining the
|
||||
appropriateness of using or redistributing the Work and assume any
|
||||
risks associated with Your exercise of permissions under this License.
|
||||
|
||||
8. Limitation of Liability. In no event and under no legal theory,
|
||||
whether in tort (including negligence), contract, or otherwise,
|
||||
unless required by applicable law (such as deliberate and grossly
|
||||
negligent acts) or agreed to in writing, shall any Contributor be
|
||||
liable to You for damages, including any direct, indirect, special,
|
||||
incidental, or consequential damages of any character arising as a
|
||||
result of this License or out of the use or inability to use the
|
||||
Work (including but not limited to damages for loss of goodwill,
|
||||
work stoppage, computer failure or malfunction, or any and all
|
||||
other commercial damages or losses), even if such Contributor
|
||||
has been advised of the possibility of such damages.
|
||||
|
||||
9. Accepting Warranty or Additional Liability. While redistributing
|
||||
the Work or Derivative Works thereof, You may choose to offer,
|
||||
and charge a fee for, acceptance of support, warranty, indemnity,
|
||||
or other liability obligations and/or rights consistent with this
|
||||
License. However, in accepting such obligations, You may act only
|
||||
on Your own behalf and on Your sole responsibility, not on behalf
|
||||
of any other Contributor, and only if You agree to indemnify,
|
||||
defend, and hold each Contributor harmless for any liability
|
||||
incurred by, or claims asserted against, such Contributor by reason
|
||||
of your accepting any such warranty or additional liability.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
APPENDIX: How to apply the Apache License to your work.
|
||||
|
||||
To apply the Apache License to your work, attach the following
|
||||
boilerplate notice, with the fields enclosed by brackets "{}"
|
||||
replaced with your own identifying information. (Don't include
|
||||
the brackets!) The text should be enclosed in the appropriate
|
||||
comment syntax for the file format. We also recommend that a
|
||||
file or class name and description of purpose be included on the
|
||||
same "printed page" as the copyright notice for easier
|
||||
identification within third-party archives.
|
||||
|
||||
Copyright {yyyy} Authors of Cilium
|
||||
|
||||
Licensed under the Apache License, Version 2.0 (the "License");
|
||||
you may not use this file except in compliance with the License.
|
||||
You may obtain a copy of the License at
|
||||
|
||||
http://www.apache.org/licenses/LICENSE-2.0
|
||||
|
||||
Unless required by applicable law or agreed to in writing, software
|
||||
distributed under the License is distributed on an "AS IS" BASIS,
|
||||
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||
See the License for the specific language governing permissions and
|
||||
limitations under the License.
|
||||
|
||||
|
|
@ -0,0 +1,330 @@
|
|||
# cilium
|
||||
|
||||
 
|
||||
|
||||
Cilium is open source software for providing and transparently securing
|
||||
network connectivity and loadbalancing between application workloads such as
|
||||
application containers or processes. Cilium operates at Layer 3/4 to provide
|
||||
traditional networking and security services as well as Layer 7 to protect and
|
||||
secure use of modern application protocols such as HTTP, gRPC and Kafka.
|
||||
|
||||
A new Linux kernel technology called eBPF is at the foundation of Cilium.
|
||||
It supports dynamic insertion of eBPF bytecode into the Linux kernel at various
|
||||
integration points such as: network IO, application sockets, and tracepoints
|
||||
to implement security, networking and visibility logic. eBPF is highly
|
||||
efficient and flexible.
|
||||
|
||||
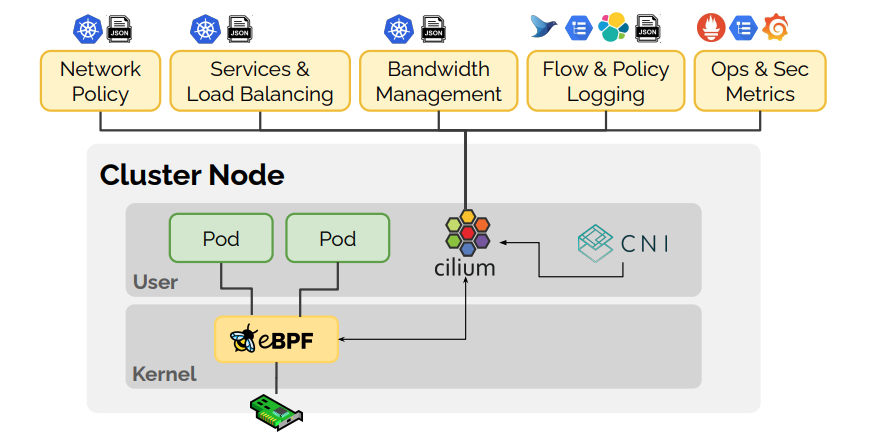
|
||||
|
||||
## Prerequisites
|
||||
|
||||
* Kubernetes: `>= 1.12.0-0`
|
||||
* Helm: `>= 3.0`
|
||||
|
||||
## Getting Started
|
||||
|
||||
Try Cilium on any Kubernetes distribution in under 15 minutes:
|
||||
|
||||
| Minikube | Self-Managed K8s | Amazon EKS | Google GKE | Microsoft AKS |
|
||||
|:-:|:-:|:-:|:-:|:-:|
|
||||
| [](https://cilium.readthedocs.io/en/stable/gettingstarted/minikube/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-self-managed/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-eks/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-gke/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-aks/) |
|
||||
|
||||
Or, for a quick install with the default configuration:
|
||||
|
||||
```
|
||||
$ helm repo add cilium https://helm.cilium.io/
|
||||
$ helm install cilium cilium/cilium --namespace=kube-system
|
||||
```
|
||||
|
||||
After Cilium is installed, you can explore the features that Cilium has to
|
||||
offer from the [Getting Started Guides page](https://docs.cilium.io/en/latest/gettingstarted/).
|
||||
|
||||
## Source Code
|
||||
|
||||
* <https://github.com/cilium/cilium>
|
||||
|
||||
## Getting Help
|
||||
|
||||
The best way to get help if you get stuck is to ask a question on the
|
||||
[Cilium Slack channel](https://cilium.herokuapp.com/). With Cilium
|
||||
contributors across the globe, there is almost always someone available to help.
|
||||
|
||||
## Values
|
||||
|
||||
| Key | Type | Default | Description |
|
||||
|-----|------|---------|-------------|
|
||||
| affinity | object | `{"podAntiAffinity":{"requiredDuringSchedulingIgnoredDuringExecution":[{"labelSelector":{"matchExpressions":[{"key":"k8s-app","operator":"In","values":["cilium"]}]},"topologyKey":"kubernetes.io/hostname"}]}}` | Pod affinity for cilium-agent. |
|
||||
| agent | bool | `true` | Install the cilium agent resources. |
|
||||
| autoDirectNodeRoutes | bool | `false` | |
|
||||
| azure.enabled | bool | `false` | Enable Azure integration |
|
||||
| bandwidthManager | bool | `false` | Optimize TCP and UDP workloads and enable rate-limiting traffic from individual Pods with EDT (Earliest Departure Time) through the "kubernetes.io/egress-bandwidth" Pod annotation. |
|
||||
| bpf.clockProbe | bool | `false` | |
|
||||
| bpf.lbMapMax | int | `65536` | Configure the maximum number of entries in the TCP connection tracking table. ctTcpMax: '524288' -- Configure the maximum number of entries for the non-TCP connection tracking table. ctAnyMax: '262144' -- Configure the maximum number of service entries in the load balancer maps. |
|
||||
| bpf.monitorAggregation | string | `"medium"` | Configure auto-sizing for all BPF maps based on available memory. ref: https://docs.cilium.io/en/v1.9/concepts/ebpf/maps/#ebpf-maps -- Configure the level of aggregation for monitor notifications. Valid options are none, low, medium, maximum |
|
||||
| bpf.monitorFlags | string | `"all"` | Configure which TCP flags trigger notifications when seen for the first time in a connection. |
|
||||
| bpf.monitorInterval | string | `"5s"` | Configure the typical time between monitor notifications for active connections. |
|
||||
| bpf.policyMapMax | int | `16384` | Configure the maximum number of entries for the NAT table. natMax: 524288 -- Configure the maximum number of entries for the neighbor table. neighMax: 524288 -- Configure the maximum number of entries in endpoint policy map. (per endpoint) |
|
||||
| bpf.preallocateMaps | bool | `false` | Enables pre-allocation of eBPF map values. This increases memory usage but can reduce latency. |
|
||||
| bpf.waitForMount | bool | `false` | Force the cilium-agent DaemonSet to wait in an initContainer until the eBPF filesystem has been mounted. |
|
||||
| certgen | object | `{"image":{"pullPolicy":"IfNotPresent","repository":"quay.io/cilium/certgen","tag":"v0.1.3"},"podLabels":{},"ttlSecondsAfterFinished":1800}` | Configure certificate generation for Hubble integration. If hubble.tls.auto.method=cronJob, these values are used for the Kubernetes CronJob which will be scheduled regularly to (re)generate any certificates not provided manually. |
|
||||
| certgen.podLabels | object | `{}` | Labels to be added to hubble-certgen pods |
|
||||
| certgen.ttlSecondsAfterFinished | int | `1800` | Seconds after which the completed job pod will be deleted |
|
||||
| cleanBpfState | bool | `false` | Clean all eBPF datapath state from the initContainer of the cilium-agent DaemonSet. WARNING: Use with care! |
|
||||
| cleanState | bool | `false` | Clean all local Cilium state from the initContainer of the cilium-agent DaemonSet. Implies cleanBpfState: true. WARNING: Use with care! |
|
||||
| cluster.id | int | `nil` | Unique ID of the cluster. Must be unique across all connected clusters and in the range of 1 to 255. Only required for Cluster Mesh. |
|
||||
| cluster.name | string | `"default"` | Name of the cluster. Only required for Cluster Mesh. |
|
||||
| clustermesh.apiserver.etcd.image | object | `{"pullPolicy":"IfNotPresent","repository":"quay.io/coreos/etcd","tag":"v3.4.13"}` | Clustermesh API server etcd image. |
|
||||
| clustermesh.apiserver.image | object | `{"digest":"sha256:e4a6d47d0d8e4ef52c44e99a906076e29e8513a35a972e60100df2168b381318","pullPolicy":"IfNotPresent","repository":"quay.io/cilium/clustermesh-apiserver","tag":"v1.9.6","useDigest":false}` | Clustermesh API server image. |
|
||||
| clustermesh.apiserver.nodeSelector | object | `{}` | Node labels for pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| clustermesh.apiserver.podAnnotations | object | `{}` | Annotations to be added to clustermesh-apiserver pods |
|
||||
| clustermesh.apiserver.podLabels | object | `{}` | Labels to be added to clustermesh-apiserver pods |
|
||||
| clustermesh.apiserver.replicas | int | `1` | Number of replicas run for the clustermesh-apiserver deployment. |
|
||||
| clustermesh.apiserver.resources | object | `{}` | Resource requests and limits for the clustermesh-apiserver container of the clustermesh-apiserver deployment, such as resources: limits: cpu: 1000m memory: 1024M requests: cpu: 100m memory: 64Mi |
|
||||
| clustermesh.apiserver.service.annotations | object | `{}` | Annotations for the clustermesh-apiserver For GKE LoadBalancer, use annotation cloud.google.com/load-balancer-type: "Internal" For EKS LoadBalancer, use annotation service.beta.kubernetes.io/aws-load-balancer-internal: 0.0.0.0/0 |
|
||||
| clustermesh.apiserver.service.nodePort | int | `32379` | Optional port to use as the node port for apiserver access. |
|
||||
| clustermesh.apiserver.service.type | string | `"NodePort"` | |
|
||||
| clustermesh.apiserver.tls.admin | object | `{"cert":"","key":""}` | base64 encoded PEM values for the clustermesh-apiserver admin certificate and private key Used if 'auto' is not enabled. |
|
||||
| clustermesh.apiserver.tls.auto | object | `{"certValidityDuration":1095,"enabled":true,"method":"helm"}` | Configure automatic TLS certificates generation. A Kubernetes CronJob is used the generate any certificates not provided by the user at installation time. |
|
||||
| clustermesh.apiserver.tls.auto.certValidityDuration | int | `1095` | Generated certificates validity duration in days. |
|
||||
| clustermesh.apiserver.tls.auto.enabled | bool | `true` | When set to true, automatically generate a CA and certificates to enable mTLS between clustermesh-apiserver and external workload instances. If set to false, the certs to be provided by setting appropriate values below. |
|
||||
| clustermesh.apiserver.tls.ca | object | `{"cert":"","key":""}` | base64 encoded PEM values for the ExternalWorkload CA certificate and private key. |
|
||||
| clustermesh.apiserver.tls.ca.cert | string | `""` | Optional CA cert. If it is provided, it will be used by the 'cronJob' method to generate all other certificates. Otherwise, an ephemeral CA is generated. |
|
||||
| clustermesh.apiserver.tls.ca.key | string | `""` | Optional CA private key. If it is provided, it will be used by the 'cronJob' method to generate all other certificates. Otherwise, an ephemeral CA is generated. |
|
||||
| clustermesh.apiserver.tls.client | object | `{"cert":"","key":""}` | base64 encoded PEM values for the clustermesh-apiserver client certificate and private key Used if 'auto' is not enabled. |
|
||||
| clustermesh.apiserver.tls.remote | object | `{"cert":"","key":""}` | base64 encoded PEM values for the clustermesh-apiserver remote cluster certificate and private key Used if 'auto' is not enabled. |
|
||||
| clustermesh.apiserver.tls.server | object | `{"cert":"","key":""}` | base64 encoded PEM values for the clustermesh-apiserver server certificate and private key Used if 'auto' is not enabled. |
|
||||
| clustermesh.apiserver.tolerations | list | `[]` | Node tolerations for pod assignment on nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| clustermesh.apiserver.updateStrategy | object | `{"rollingUpdate":{"maxUnavailable":1},"type":"RollingUpdate"}` | clustermesh-apiserver update strategy |
|
||||
| clustermesh.useAPIServer | bool | `false` | Deploy clustermesh-apiserver for clustermesh |
|
||||
| cni.binPath | string | `"/opt/cni/bin"` | Configure the path to the CNI binary directory on the host. |
|
||||
| cni.chainingMode | string | `"none"` | Configure chaining on top of other CNI plugins. Possible values: - none - generic-veth - aws-cni - portmap |
|
||||
| cni.confFileMountPath | string | `"/tmp/cni-configuration"` | Configure the path to where to mount the ConfigMap inside the agent pod. |
|
||||
| cni.confPath | string | `"/etc/cni/net.d"` | Configure the path to the CNI configuration directory on the host. |
|
||||
| cni.configMapKey | string | `"cni-config"` | Specify the path to a CNI config to read from on agent start. This can be useful if you want to manage your CNI configuration outside of a Kubernetes environment. This parameter is mutually exclusive with the 'cni.configMap' parameter. readCniConf: /host/etc/cni/net.d/05-cilium.conf -- When defined, configMap will mount the provided value as ConfigMap and interpret the cniConf variable as CNI configuration file and write it when the agent starts up configMap: cni-configuration -- Configure the key in the CNI ConfigMap to read the contents of the CNI configuration from. |
|
||||
| cni.customConf | bool | `false` | Skip writing of the CNI configuration. This can be used if writing of the CNI configuration is performed by external automation. |
|
||||
| cni.hostConfDirMountPath | string | `"/host/etc/cni/net.d"` | Configure the path to where the CNI configuration directory is mounted inside the agent pod. |
|
||||
| cni.install | bool | `true` | Install the CNI configuration and binary files into the filesystem. |
|
||||
| containerRuntime | object | `{"integration":"none"}` | Configure how frequently garbage collection should occur for the datapath connection tracking table. conntrackGCInterval: "0s" -- Configure container runtime specific integration. |
|
||||
| containerRuntime.integration | string | `"none"` | Enables specific integrations for container runtimes. Supported values: - containerd - crio - docker - none - auto (automatically detect the container runtime) |
|
||||
| daemon.runPath | string | `"/var/run/cilium"` | Configure where Cilium runtime state should be stored. |
|
||||
| datapathMode | string | `"veth"` | |
|
||||
| debug.enabled | bool | `false` | Enable debug logging |
|
||||
| enableCnpStatusUpdates | bool | `false` | Specify which network interfaces can run the eBPF datapath. This means that a packet sent from a pod to a destination outside the cluster will be masqueraded (to an output device IPv4 address), if the output device runs the program. When not specified, probing will automatically detect devices. devices: "" TODO: Add documentation disableIptablesFeederRules: "" TODO: Add documentation egressMasqueradeInterfaces: "" |
|
||||
| enableCriticalPriorityClass | bool | `true` | Explicitly enable or disable priority class. .Capabilities.KubeVersion is unsettable in `helm template` calls, it depends on k8s libriaries version that Helm was compiled against. This option allows to explicitly disable setting the priority class, which is useful for rendering charts for gke clusters in advance. |
|
||||
| enableXTSocketFallback | bool | `true` | |
|
||||
| encryption.enabled | bool | `false` | Enable transparent network encryption. |
|
||||
| encryption.keyFile | string | `"keys"` | Name of the key file inside the Kubernetes secret configured via secretName. |
|
||||
| encryption.mountPath | string | `"/etc/ipsec"` | Path to mount the secret inside the Cilium pod. |
|
||||
| encryption.nodeEncryption | bool | `false` | Enable encryption for pure node to node traffic. |
|
||||
| encryption.secretName | string | `"cilium-ipsec-keys"` | Name of the Kubernetes secret containing the encryption keys. |
|
||||
| endpointHealthChecking.enabled | bool | `true` | |
|
||||
| endpointRoutes.enabled | bool | `false` | Enable use of per endpoint routes instead of routing via the cilium_host interface. |
|
||||
| eni | bool | `false` | Enable Elastic Network Interface (ENI) integration. |
|
||||
| etcd.clusterDomain | string | `"cluster.local"` | Cluster domain for cilium-etcd-operator. |
|
||||
| etcd.clusterSize | int | `3` | Size of the managed etcd cluster. |
|
||||
| etcd.enabled | bool | `false` | Enable etcd mode for the agent. |
|
||||
| etcd.endpoints | list | `["https://CHANGE-ME:2379"]` | List of etcd endpoints (not needed when using managed=true). |
|
||||
| etcd.extraArgs | object | `{}` | Additional cilium-etcd-operator container arguments |
|
||||
| etcd.extraConfigmapMounts | list | `[]` | Additional cilium-etcd-operator ConfigMap mounts |
|
||||
| etcd.extraHostPathMounts | list | `[]` | Additional cilium-etcd-operator hostPath mounts |
|
||||
| etcd.extraInitContainers | list | `[]` | Additional InitContainers to initialize the pod |
|
||||
| etcd.image | object | `{"pullPolicy":"IfNotPresent","repository":"quay.io/cilium/cilium-etcd-operator","tag":"v2.0.7"}` | cilium-etcd-operator image. |
|
||||
| etcd.k8sService | bool | `false` | If etcd is behind a k8s service set this option to true so that Cilium does the service translation automatically without requiring a DNS to be running. |
|
||||
| etcd.managed | bool | `false` | Enable managed etcd mode based on the cilium-etcd-operator. |
|
||||
| etcd.nodeSelector | object | `{}` | Node labels for cilium-etcd-operator pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| etcd.podAnnotations | object | `{}` | Annotations to be added to cilium-etcd-operator pods |
|
||||
| etcd.podDisruptionBudget | object | `{"enabled":true,"maxUnavailable":2}` | PodDisruptionBudget settings ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/ |
|
||||
| etcd.podLabels | object | `{}` | Labels to be added to cilium-etcd-operator pods |
|
||||
| etcd.priorityClassName | string | `""` | cilium-etcd-operator priorityClassName |
|
||||
| etcd.resources | object | `{}` | cilium-etcd-operator resource limits & requests ref: https://kubernetes.io/docs/user-guide/compute-resources/ |
|
||||
| etcd.securityContext | object | `{}` | Security context to be added to cilium-etcd-operator pods |
|
||||
| etcd.ssl | bool | `false` | Enable use of TLS/SSL for connectivity to etcd. (auto-enabled if managed=true) |
|
||||
| etcd.tolerations | list | `[{"operator":"Exists"}]` | Node tolerations for cilium-etcd-operator scheduling to nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| etcd.updateStrategy | object | `{"rollingUpdate":{"maxSurge":1,"maxUnavailable":1},"type":"RollingUpdate"}` | cilium-etcd-operator update strategy |
|
||||
| externalIPs.enabled | bool | `false` | Enable ExternalIPs service support. |
|
||||
| externalWorkloads | object | `{"enabled":false}` | Configure external workloads support |
|
||||
| externalWorkloads.enabled | bool | `false` | Enable support for external workloads, such as VMs (false by default). |
|
||||
| extraArgs | object | `{}` | Additional agent container arguments |
|
||||
| extraConfig | object | `{}` | extraConfig allows you to specify additional configuration parameters to be included in the cilium-config configmap. |
|
||||
| extraConfigmapMounts | list | `[]` | Additional agent ConfigMap mounts |
|
||||
| extraEnv | object | `{}` | Additional agent container environment variables |
|
||||
| extraHostPathMounts | list | `[]` | Additional agent hostPath mounts |
|
||||
| extraInitContainers | list | `[]` | Additional InitContainers to initialize the pod |
|
||||
| flannel.enabled | bool | `false` | |
|
||||
| flannel.masterDevice | string | `"cni0"` | |
|
||||
| flannel.uninstallOnExit | bool | `false` | |
|
||||
| gke.enabled | bool | `false` | Enable Google Kubernetes Engine integration |
|
||||
| healthChecking | bool | `true` | |
|
||||
| healthPort | int | `9876` | TCP port for the agent health API. This is not the port for cilium-health. |
|
||||
| hostFirewall | bool | `false` | Enables the enforcement of host policies in the eBPF datapath. |
|
||||
| hostPort.enabled | bool | `false` | Enable hostPort service support. |
|
||||
| hostServices | object | `{"enabled":false,"protocols":"tcp,udp"}` | Configure ClusterIP service handling in the host namespace (the node). |
|
||||
| hostServices.enabled | bool | `false` | Enable host reachable services. |
|
||||
| hostServices.protocols | string | `"tcp,udp"` | Supported list of protocols to apply ClusterIP translation to. |
|
||||
| hubble.enabled | bool | `true` | Enable Hubble (true by default). |
|
||||
| hubble.listenAddress | string | `":4244"` | An additional address for Hubble to listen to. Set this field ":4244" if you are enabling Hubble Relay, as it assumes that Hubble is listening on port 4244. |
|
||||
| hubble.metrics | object | `{"enabled":null,"port":9091,"serviceMonitor":{"enabled":false}}` | Buffer size of the channel Hubble uses to receive monitor events. If this value is not set, the queue size is set to the default monitor queue size. eventQueueSize: "" -- Number of recent flows for Hubble to cache. Defaults to 4095. Possible values are: 1, 3, 7, 15, 31, 63, 127, 255, 511, 1023, 2047, 4095, 8191, 16383, 32767, 65535 eventBufferCapacity: "4095" -- Hubble metrics configuration. See https://docs.cilium.io/en/stable/configuration/metrics/#hubble-metrics for more comprehensive documentation about Hubble metrics. |
|
||||
| hubble.metrics.enabled | string | `nil` | Configures the list of metrics to collect. If empty or null, metrics are disabled. Example: enabled: - dns:query;ignoreAAAA - drop - tcp - flow - icmp - http You can specify the list of metrics from the helm CLI: --set metrics.enabled="{dns:query;ignoreAAAA,drop,tcp,flow,icmp,http}" |
|
||||
| hubble.metrics.port | int | `9091` | Configure the port the hubble metric server listens on. |
|
||||
| hubble.metrics.serviceMonitor.enabled | bool | `false` | Create ServiceMonitor resources for Prometheus Operator. This requires the prometheus CRDs to be available. ref: https://github.com/prometheus-operator/prometheus-operator/blob/master/example/prometheus-operator-crd/monitoring.coreos.com_servicemonitors.yaml) |
|
||||
| hubble.metricsServer | string | `""` | |
|
||||
| hubble.relay.dialTimeout | string | `nil` | Dial timeout to connect to the local hubble instance to receive peer information (e.g. "30s"). |
|
||||
| hubble.relay.enabled | bool | `false` | Enable Hubble Relay (requires hubble.enabled=true) |
|
||||
| hubble.relay.image | object | `{"digest":"sha256:2ea804c454b660d474feae96c01da1b9193dfce6809b4d3825e7b6efc6ade8c7","pullPolicy":"IfNotPresent","repository":"quay.io/cilium/hubble-relay","tag":"v1.9.6","useDigest":false}` | Hubble-relay container image. |
|
||||
| hubble.relay.listenHost | string | `""` | Host to listen to. Specify an empty string to bind to all the interfaces. |
|
||||
| hubble.relay.listenPort | string | `"4245"` | Port to listen to. |
|
||||
| hubble.relay.nodeSelector | object | `{}` | Node labels for pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| hubble.relay.podAnnotations | object | `{}` | Annotations to be added to hubble-relay pods |
|
||||
| hubble.relay.podLabels | object | `{}` | Labels to be added to hubble-relay pods |
|
||||
| hubble.relay.replicas | int | `1` | Number of replicas run for the hubble-relay deployment. |
|
||||
| hubble.relay.resources | object | `{}` | Specifies the resources for the hubble-relay pods |
|
||||
| hubble.relay.retryTimeout | string | `nil` | Backoff duration to retry connecting to the local hubble instance in case of failure (e.g. "30s"). |
|
||||
| hubble.relay.rollOutPods | bool | `false` | Roll out Hubble Relay pods automatically when configmap is updated. |
|
||||
| hubble.relay.sortBufferDrainTimeout | string | `nil` | When the per-request flows sort buffer is not full, a flow is drained every time this timeout is reached (only affects requests in follow-mode) (e.g. "1s"). |
|
||||
| hubble.relay.sortBufferLenMax | string | `nil` | Max number of flows that can be buffered for sorting before being sent to the client (per request) (e.g. 100). |
|
||||
| hubble.relay.tls | object | `{"client":{"cert":"","key":""},"server":{"cert":"","enabled":false,"key":""}}` | TLS configuration for Hubble Relay |
|
||||
| hubble.relay.tls.client | object | `{"cert":"","key":""}` | base64 encoded PEM values for the hubble-relay client certificate and private key This keypair is presented to Hubble server instances for mTLS authentication and is required when hubble.tls.enabled is true. These values need to be set manually if hubble.tls.auto.enabled is false. |
|
||||
| hubble.relay.tls.server | object | `{"cert":"","enabled":false,"key":""}` | base64 encoded PEM values for the hubble-relay server certificate and private key |
|
||||
| hubble.relay.tolerations | list | `[]` | Node tolerations for pod assignment on nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| hubble.relay.updateStrategy | object | `{"rollingUpdate":{"maxUnavailable":1},"type":"RollingUpdate"}` | hubble-relay update strategy |
|
||||
| hubble.socketPath | string | `"/var/run/cilium/hubble.sock"` | Unix domain socket path to listen to when Hubble is enabled. |
|
||||
| hubble.tls | object | `{"auto":{"certValidityDuration":1095,"enabled":true,"method":"helm","schedule":"0 0 1 */4 *"},"ca":{"cert":"","key":""},"enabled":true,"server":{"cert":"","key":""}}` | TLS configuration for Hubble |
|
||||
| hubble.tls.auto | object | `{"certValidityDuration":1095,"enabled":true,"method":"helm","schedule":"0 0 1 */4 *"}` | Configure automatic TLS certificates generation. |
|
||||
| hubble.tls.auto.certValidityDuration | int | `1095` | Generated certificates validity duration in days. |
|
||||
| hubble.tls.auto.enabled | bool | `true` | Auto-generate certificates. When set to true, automatically generate a CA and certificates to enable mTLS between Hubble server and Hubble Relay instances. If set to false, the certs for Hubble server need to be provided by setting appropriate values below. |
|
||||
| hubble.tls.auto.method | string | `"helm"` | Set the method to auto-generate certificates. Supported values: - helm: This method uses Helm to generate all certificates. - cronJob: This method uses a Kubernetes CronJob the generate any certificates not provided by the user at installation time. |
|
||||
| hubble.tls.auto.schedule | string | `"0 0 1 */4 *"` | Schedule for certificates regeneration (regardless of their expiration date). Only used if method is "cronJob". If nil, then no recurring job will be created. Instead, only the one-shot job is deployed to generate the certificates at installation time. Defaults to midnight of the first day of every fourth month. For syntax, see https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#schedule |
|
||||
| hubble.tls.ca | object | `{"cert":"","key":""}` | base64 encoded PEM values for the Hubble CA certificate and private key. |
|
||||
| hubble.tls.ca.key | string | `""` | The CA private key (optional). If it is provided, then it will be used by hubble.tls.auto.method=cronJob to generate all other certificates. Otherwise, a ephemeral CA is generated if hubble.tls.auto.enabled=true. |
|
||||
| hubble.tls.enabled | bool | `true` | Enable mutual TLS for listenAddress. Setting this value to false is highly discouraged as the Hubble API provides access to potentially sensitive network flow metadata and is exposed on the host network. |
|
||||
| hubble.tls.server | object | `{"cert":"","key":""}` | base64 encoded PEM values for the Hubble server certificate and private key |
|
||||
| hubble.ui.backend.image | object | `{"pullPolicy":"IfNotPresent","repository":"quay.io/cilium/hubble-ui-backend","tag":"v0.7.3"}` | Hubble-ui backend image. |
|
||||
| hubble.ui.backend.resources | object | `{}` | |
|
||||
| hubble.ui.enabled | bool | `false` | |
|
||||
| hubble.ui.frontend.image | object | `{"pullPolicy":"IfNotPresent","repository":"quay.io/cilium/hubble-ui","tag":"v0.7.3"}` | Hubble-ui frontend image. |
|
||||
| hubble.ui.frontend.resources | object | `{}` | |
|
||||
| hubble.ui.ingress | object | `{"annotations":{},"enabled":false,"hosts":["chart-example.local"],"tls":[]}` | hubble-ui ingress configuration. |
|
||||
| hubble.ui.nodeSelector | object | `{}` | Node labels for pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| hubble.ui.podAnnotations | object | `{}` | Annotations to be added to hubble-ui pods |
|
||||
| hubble.ui.podLabels | object | `{}` | Labels to be added to hubble-ui pods |
|
||||
| hubble.ui.proxy.image | object | `{"pullPolicy":"IfNotPresent","repository":"docker.io/envoyproxy/envoy","tag":"v1.14.5"}` | Hubble-ui ingress proxy image. |
|
||||
| hubble.ui.proxy.resources | object | `{}` | |
|
||||
| hubble.ui.replicas | int | `1` | |
|
||||
| hubble.ui.rollOutPods | bool | `false` | Roll out Hubble-ui pods automatically when configmap is updated. |
|
||||
| hubble.ui.securityContext.enabled | bool | `true` | |
|
||||
| hubble.ui.tolerations | list | `[]` | Node tolerations for pod assignment on nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| hubble.ui.updateStrategy | object | `{"rollingUpdate":{"maxUnavailable":1},"type":"RollingUpdate"}` | hubble-ui update strategy. |
|
||||
| identityAllocationMode | string | `"crd"` | |
|
||||
| image | object | `{"digest":"sha256:6e2bc051dd5d942085591ea6150623790a8ffbaaab567007a2707fc7668d8055","pullPolicy":"IfNotPresent","repository":"quay.io/cilium/cilium","tag":"v1.9.6","useDigest":false}` | Agent container image. |
|
||||
| imagePullSecrets | string | `nil` | Configure image pull secrets for pulling container images |
|
||||
| installIptablesRules | bool | `true` | |
|
||||
| ipMasqAgent | object | `{"enabled":false}` | Configure the eBPF-based ip-masq-agent |
|
||||
| ipam.mode | string | `"cluster-pool"` | Configure IP Address Management mode. ref: https://docs.cilium.io/en/stable/concepts/networking/ipam/ |
|
||||
| ipam.operator.clusterPoolIPv4MaskSize | int | `24` | IPv4 CIDR mask size to delegate to individual nodes for IPAM. |
|
||||
| ipam.operator.clusterPoolIPv4PodCIDR | string | `"10.0.0.0/8"` | IPv4 CIDR range to delegate to individual nodes for IPAM. |
|
||||
| ipam.operator.clusterPoolIPv6MaskSize | int | `120` | IPv6 CIDR mask size to delegate to individual nodes for IPAM. |
|
||||
| ipam.operator.clusterPoolIPv6PodCIDR | string | `"fd00::/104"` | IPv6 CIDR range to delegate to individual nodes for IPAM. |
|
||||
| ipv4.enabled | bool | `true` | Enable IPv4 support. |
|
||||
| ipv6.enabled | bool | `false` | Enable IPv6 support. |
|
||||
| ipvlan.enabled | bool | `false` | Enable the IPVLAN datapath |
|
||||
| k8s | object | `{}` | Configure Kubernetes specific configuration |
|
||||
| keepDeprecatedLabels | bool | `false` | requireIPv6PodCIDR enables waiting for Kubernetes to provide the PodCIDR range via the Kubernetes node resource requireIPv6PodCIDR: false -- Keep the deprecated selector labels when deploying Cilium DaemonSet |
|
||||
| keepDeprecatedProbes | bool | `false` | Keep the deprecated probes when deploying Cilium DaemonSet |
|
||||
| kubeProxyReplacement | string | `"probe"` | Configure the kube-proxy replacement in Cilium BPF datapath Valid options are "disabled", "probe", "partial", "strict". ref: https://docs.cilium.io/en/stable/gettingstarted/kubeproxy-free/ |
|
||||
| kubeProxyReplacementHealthzBindAddr | string | `""` | healthz server bind address for the kube-proxy replacement. To enable set the value to '0.0.0.0:10256' for all ipv4 addresses and this '[::]:10256' for all ipv6 addresses. By default it is disabled. |
|
||||
| l7Proxy | bool | `true` | Enable Layer 7 network policy. |
|
||||
| localRedirectPolicy | bool | `false` | |
|
||||
| logSystemLoad | bool | `false` | |
|
||||
| maglev | object | `{}` | Configure maglev consistent hashing |
|
||||
| masquerade | bool | `true` | hashSeed is the cluster-wide base64 encoded seed for the hashing hashSeed: -- Enables masquerading of traffic leaving the node for destinations outside of the cluster. |
|
||||
| monitor | object | `{"enabled":false}` | Specify the CIDR for native routing (ie to avoid IP masquerade for). This value corresponds to the configured cluster-cidr. nativeRoutingCIDR: -- Configure cilium-monitor sidecar |
|
||||
| name | string | `"cilium"` | Agent container name. |
|
||||
| nodePort | object | `{"autoProtectPortRange":true,"bindProtection":true,"enableHealthCheck":true,"enabled":false}` | Configure service load balancing loadBalancer: algorithm is the name of the load balancing algorithm for backend selection e.g. random or maglev algorithm: "random" mode is the operation mode of load balancing for remote backends e.g. snat, dsr, hybrid mode: snat acceleration is the option to accelerate service handling via XDP e.g. native, disabled acceleration: disabled |
|
||||
| nodePort.autoProtectPortRange | bool | `true` | Append NodePort range to ip_local_reserved_ports if clash with ephemeral ports is detected. |
|
||||
| nodePort.bindProtection | bool | `true` | Port range to use for NodePort services. range: "30000,32767" -- Set to true to prevent applications binding to service ports. |
|
||||
| nodePort.enableHealthCheck | bool | `true` | Enable healthcheck nodePort server for NodePort services |
|
||||
| nodePort.enabled | bool | `false` | Enable the Cilium NodePort service implementation. |
|
||||
| nodeinit.bootstrapFile | string | `"/tmp/cilium-bootstrap-time"` | bootstrapFile is the location of the file where the bootstrap timestamp is written by the node-init DaemonSet |
|
||||
| nodeinit.enabled | bool | `false` | Enable the node initialization DaemonSet |
|
||||
| nodeinit.extraArgs | object | `{}` | |
|
||||
| nodeinit.extraConfigmapMounts | list | `[]` | |
|
||||
| nodeinit.extraEnv | object | `{}` | |
|
||||
| nodeinit.extraHostPathMounts | list | `[]` | |
|
||||
| nodeinit.extraInitContainers | list | `[]` | |
|
||||
| nodeinit.image | object | `{"pullPolicy":"IfNotPresent","repository":"quay.io/cilium/startup-script","tag":"62bfbe88c17778aad7bef9fa57ff9e2d4a9ba0d8"}` | node-init image. |
|
||||
| nodeinit.nodeSelector | object | `{}` | Node labels for nodeinit pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| nodeinit.podAnnotations | object | `{}` | Annotations to be added to node-init pods |
|
||||
| nodeinit.podDisruptionBudget | object | `{"enabled":true,"maxUnavailable":2}` | PodDisruptionBudget settings ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/ |
|
||||
| nodeinit.podLabels | object | `{}` | Labels to be added to node-init pods |
|
||||
| nodeinit.priorityClassName | string | `""` | |
|
||||
| nodeinit.resources | object | `{"requests":{"cpu":"100m","memory":"100Mi"}}` | nodeinit resource limits & requests ref: https://kubernetes.io/docs/user-guide/compute-resources/ |
|
||||
| nodeinit.securityContext | object | `{}` | Security context to be added to nodeinit pods |
|
||||
| nodeinit.tolerations | list | `[{"operator":"Exists"}]` | Node tolerations for nodeinit scheduling to nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| nodeinit.updateStrategy | object | `{"type":"RollingUpdate"}` | node-init update strategy |
|
||||
| operator.affinity | object | `{"podAntiAffinity":{"requiredDuringSchedulingIgnoredDuringExecution":[{"labelSelector":{"matchExpressions":[{"key":"io.cilium/app","operator":"In","values":["operator"]}]},"topologyKey":"kubernetes.io/hostname"}]}}` | cilium-operator affinity |
|
||||
| operator.enabled | bool | `true` | Enable the cilium-operator component (required). |
|
||||
| operator.endpointGCInterval | string | `"5m0s"` | |
|
||||
| operator.extraArgs | object | `{}` | Additional cilium-etcd-operator container arguments |
|
||||
| operator.extraConfigmapMounts | list | `[]` | |
|
||||
| operator.extraEnv | object | `{}` | |
|
||||
| operator.extraHostPathMounts | list | `[]` | Additional cilium-operator hostPath mounts |
|
||||
| operator.extraInitContainers | list | `[]` | Additional InitContainers to initialize the pod |
|
||||
| operator.identityGCInterval | string | `"15m0s"` | |
|
||||
| operator.identityHeartbeatTimeout | string | `"30m0s"` | |
|
||||
| operator.image | object | `{"awsDigest":"sha256:9cc271130849e109608478b5fa695d84ab9542900ceeb7128c1a0c7b29abad3c","azureDigest":"sha256:e70493e05af077501563db990db1165dfcc66b09bfb751065f3d72e504e46ca7","genericDigest":"sha256:29a315472ae0701dbfbfff1e9766f68c2915edd896a011f7e8e409cf4d687453","pullPolicy":"IfNotPresent","repository":"quay.io/cilium/operator","suffix":"","tag":"v1.9.6","useDigest":false}` | cilium-operator image. |
|
||||
| operator.nodeSelector | object | `{}` | Node labels for cilium-operator pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| operator.podAnnotations | object | `{}` | Annotations to be added to cilium-operator pods |
|
||||
| operator.podDisruptionBudget | object | `{"enabled":false,"maxUnavailable":1}` | PodDisruptionBudget settings ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/ |
|
||||
| operator.podLabels | object | `{}` | Labels to be added to cilium-operator pods |
|
||||
| operator.priorityClassName | string | `""` | cilium-operator priorityClassName |
|
||||
| operator.prometheus | object | `{"enabled":false,"port":6942,"serviceMonitor":{"enabled":false}}` | Enable prometheus metrics for cilium-operator on the configured port at /metrics |
|
||||
| operator.prometheus.serviceMonitor.enabled | bool | `false` | Enable service monitors. This requires the prometheus CRDs to be available (see https://github.com/prometheus-operator/prometheus-operator/blob/master/example/prometheus-operator-crd/monitoring.coreos.com_servicemonitors.yaml) |
|
||||
| operator.replicas | int | `2` | Number of replicas to run for the cilium-operator deployment |
|
||||
| operator.resources | object | `{}` | cilium-operator resource limits & requests ref: https://kubernetes.io/docs/user-guide/compute-resources/ |
|
||||
| operator.rollOutPods | bool | `false` | Roll out cilium-operator pods automatically when configmap is updated. |
|
||||
| operator.securityContext | object | `{}` | Security context to be added to cilium-operator pods |
|
||||
| operator.tolerations | list | `[{"operator":"Exists"}]` | Node tolerations for cilium-operator scheduling to nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| operator.updateStrategy | object | `{"rollingUpdate":{"maxSurge":1,"maxUnavailable":1},"type":"RollingUpdate"}` | cilium-operator update strategy |
|
||||
| podAnnotations | object | `{}` | Annotations to be added to agent pods |
|
||||
| podDisruptionBudget | object | `{"enabled":true,"maxUnavailable":2}` | PodDisruptionBudget settings ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/ |
|
||||
| podLabels | object | `{}` | Labels to be added to agent pods |
|
||||
| policyEnforcementMode | string | `"default"` | |
|
||||
| pprof.enabled | bool | `false` | Enable Go pprof debugging |
|
||||
| preflight.enabled | bool | `false` | Enable Cilium pre-flight resources (required for upgrade) |
|
||||
| preflight.extraArgs | object | `{}` | |
|
||||
| preflight.extraConfigmapMounts | list | `[]` | |
|
||||
| preflight.extraEnv | object | `{}` | |
|
||||
| preflight.extraHostPathMounts | list | `[]` | |
|
||||
| preflight.extraInitContainers | list | `[]` | |
|
||||
| preflight.image | object | `{"digest":"sha256:6e2bc051dd5d942085591ea6150623790a8ffbaaab567007a2707fc7668d8055","pullPolicy":"IfNotPresent","repository":"quay.io/cilium/cilium","tag":"v1.9.6","useDigest":false}` | Cilium pre-flight image. |
|
||||
| preflight.nodeSelector | object | `{}` | Node labels for preflight pod assignment ref: https://kubernetes.io/docs/user-guide/node-selection/ |
|
||||
| preflight.podAnnotations | object | `{}` | Annotations to be added to preflight pods |
|
||||
| preflight.podDisruptionBudget | object | `{"enabled":true,"maxUnavailable":2}` | PodDisruptionBudget settings ref: https://kubernetes.io/docs/concepts/workloads/pods/disruptions/ |
|
||||
| preflight.podLabels | object | `{}` | |
|
||||
| preflight.priorityClassName | string | `""` | |
|
||||
| preflight.resources | object | `{}` | preflight resource limits & requests ref: https://kubernetes.io/docs/user-guide/compute-resources/ |
|
||||
| preflight.securityContext | object | `{}` | Security context to be added to preflight pods |
|
||||
| preflight.tofqdnsPreCache | string | `""` | |
|
||||
| preflight.tolerations | list | `[{"effect":"NoSchedule","key":"node.kubernetes.io/not-ready"},{"effect":"NoSchedule","key":"node-role.kubernetes.io/master"},{"effect":"NoSchedule","key":"node.cloudprovider.kubernetes.io/uninitialized","value":"true"},{"key":"CriticalAddonsOnly","operator":"Exists"}]` | Node tolerations for preflight scheduling to nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| preflight.updateStrategy | object | `{"type":"RollingUpdate"}` | preflight update strategy |
|
||||
| preflight.validateCNPs | bool | `true` | By default we should always validate the installed CNPs before upgrading Cilium. This will make sure the user will have the policies deployed in the cluster with the right schema. |
|
||||
| priorityClassName | string | `""` | |
|
||||
| prometheus | object | `{"enabled":false,"port":9090,"serviceMonitor":{"enabled":false}}` | Configure prometheus metrics on the configured port at /metrics |
|
||||
| prometheus.serviceMonitor.enabled | bool | `false` | Enable service monitors. This requires the prometheus CRDs to be available (see https://github.com/prometheus-operator/prometheus-operator/blob/master/example/prometheus-operator-crd/monitoring.coreos.com_servicemonitors.yaml) |
|
||||
| proxy | object | `{"prometheus":{"port":"9095"},"sidecarImageRegex":"cilium/istio_proxy"}` | Configure Istio proxy options. |
|
||||
| proxy.sidecarImageRegex | string | `"cilium/istio_proxy"` | Regular expression matching compatible Istio sidecar istio-proxy container image names |
|
||||
| rbac.create | bool | `true` | Enable creation of Resource-Based Access Control configuration. |
|
||||
| remoteNodeIdentity | bool | `true` | Enable use of the remote node identity. ref: https://docs.cilium.io/en/v1.7/install/upgrade/#configmap-remote-node-identity |
|
||||
| resourceQuotas | object | `{"cilium":{"hard":{"pods":"10k"}},"enabled":false,"operator":{"hard":{"pods":"15"}}}` | Enable resource quotas for priority classes used in the cluster. |
|
||||
| resources | object | `{}` | Agent resource limits & requests ref: https://kubernetes.io/docs/user-guide/compute-resources/ |
|
||||
| rollOutCiliumPods | bool | `false` | Roll out cilium agent pods automatically when configmap is updated. |
|
||||
| securityContext | object | `{}` | Security context to be added to agent pods |
|
||||
| serviceAccounts | object | Component's fully qualified name. | Define serviceAccount names for components. |
|
||||
| serviceAccounts.certgen | object | `{"annotations":{},"create":true}` | Certgen is used if hubble.tls.auto.method=cronJob |
|
||||
| sleepAfterInit | bool | `false` | |
|
||||
| sockops | object | `{"enabled":false}` | Configure BPF socket operations configuration |
|
||||
| tls.enabled | bool | `true` | |
|
||||
| tls.secretsBackend | string | `"local"` | |
|
||||
| tolerations | list | `[{"operator":"Exists"}]` | Node tolerations for agent scheduling to nodes with taints ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ |
|
||||
| tunnel | string | `"vxlan"` | Configure the encapsulation configuration for communication between nodes. Possible values: - disabled - vxlan (default) - geneve |
|
||||
| updateStrategy | object | `{"rollingUpdate":{"maxUnavailable":2},"type":"RollingUpdate"}` | Cilium agent update strategy |
|
||||
|
|
@ -0,0 +1,54 @@
|
|||
{{ template "chart.header" . }}
|
||||
|
||||
{{ template "chart.deprecationWarning" . }}
|
||||
|
||||
{{ template "chart.versionBadge" . }}{{ template "chart.typeBadge" . }}{{ template "chart.appVersionBadge" . }}
|
||||
|
||||
Cilium is open source software for providing and transparently securing
|
||||
network connectivity and loadbalancing between application workloads such as
|
||||
application containers or processes. Cilium operates at Layer 3/4 to provide
|
||||
traditional networking and security services as well as Layer 7 to protect and
|
||||
secure use of modern application protocols such as HTTP, gRPC and Kafka.
|
||||
|
||||
A new Linux kernel technology called eBPF is at the foundation of Cilium.
|
||||
It supports dynamic insertion of eBPF bytecode into the Linux kernel at various
|
||||
integration points such as: network IO, application sockets, and tracepoints
|
||||
to implement security, networking and visibility logic. eBPF is highly
|
||||
efficient and flexible.
|
||||
|
||||

|
||||
|
||||
## Prerequisites
|
||||
|
||||
* Kubernetes: `{{ template "chart.kubeVersion" . }}`
|
||||
* Helm: `>= 3.0`
|
||||
|
||||
## Getting Started
|
||||
|
||||
Try Cilium on any Kubernetes distribution in under 15 minutes:
|
||||
|
||||
| Minikube | Self-Managed K8s | Amazon EKS | Google GKE | Microsoft AKS |
|
||||
|:-:|:-:|:-:|:-:|:-:|
|
||||
| [](https://cilium.readthedocs.io/en/stable/gettingstarted/minikube/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-self-managed/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-eks/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-gke/) | [](https://cilium.readthedocs.io/en/stable/gettingstarted/k8s-install-aks/) |
|
||||
|
||||
Or, for a quick install with the default configuration:
|
||||
|
||||
```
|
||||
$ helm repo add cilium https://helm.cilium.io/
|
||||
$ helm install cilium cilium/cilium --namespace=kube-system
|
||||
```
|
||||
|
||||
After Cilium is installed, you can explore the features that Cilium has to
|
||||
offer from the [Getting Started Guides page](https://docs.cilium.io/en/latest/gettingstarted/).
|
||||
|
||||
{{ template "chart.maintainersSection" . }}
|
||||
|
||||
{{ template "chart.sourcesSection" . }}
|
||||
|
||||
## Getting Help
|
||||
|
||||
The best way to get help if you get stuck is to ask a question on the
|
||||
[Cilium Slack channel](https://cilium.herokuapp.com/). With Cilium
|
||||
contributors across the globe, there is almost always someone available to help.
|
||||
|
||||
{{ template "chart.valuesSection" . }}
|
||||
|
|
@ -0,0 +1,58 @@
|
|||
static_resources:
|
||||
listeners:
|
||||
- name: listener_hubble_ui
|
||||
address:
|
||||
socket_address:
|
||||
address: 0.0.0.0
|
||||
port_value: 8081
|
||||
filter_chains:
|
||||
- filters:
|
||||
- name: envoy.filters.network.http_connection_manager
|
||||
config:
|
||||
codec_type: auto
|
||||
stat_prefix: ingress_http
|
||||
route_config:
|
||||
name: local_route
|
||||
virtual_hosts:
|
||||
- name: local_service
|
||||
domains: ['*']
|
||||
routes:
|
||||
- match:
|
||||
prefix: '/api/'
|
||||
route:
|
||||
cluster: backend
|
||||
max_grpc_timeout: 0s
|
||||
prefix_rewrite: '/'
|
||||
- match:
|
||||
prefix: '/'
|
||||
route:
|
||||
cluster: frontend
|
||||
cors:
|
||||
allow_origin_string_match:
|
||||
- prefix: '*'
|
||||
allow_methods: GET, PUT, DELETE, POST, OPTIONS
|
||||
allow_headers: keep-alive,user-agent,cache-control,content-type,content-transfer-encoding,x-accept-content-transfer-encoding,x-accept-response-streaming,x-user-agent,x-grpc-web,grpc-timeout
|
||||
max_age: '1728000'
|
||||
expose_headers: grpc-status,grpc-message
|
||||
http_filters:
|
||||
- name: envoy.filters.http.grpc_web
|
||||
- name: envoy.filters.http.cors
|
||||
- name: envoy.filters.http.router
|
||||
clusters:
|
||||
- name: frontend
|
||||
connect_timeout: 0.25s
|
||||
type: strict_dns
|
||||
lb_policy: round_robin
|
||||
hosts:
|
||||
- socket_address:
|
||||
address: 127.0.0.1
|
||||
port_value: 8080
|
||||
- name: backend
|
||||
connect_timeout: 0.25s
|
||||
type: logical_dns
|
||||
lb_policy: round_robin
|
||||
http2_protocol_options: {}
|
||||
hosts:
|
||||
- socket_address:
|
||||
address: 127.0.0.1
|
||||
port_value: 8090
|
||||
|
|
@ -0,0 +1,20 @@
|
|||
{{- if (and (.Values.preflight.enabled) (not (.Values.agent)) (not (.Values.operator.enabled))) }}
|
||||
You have successfully ran the preflight check.
|
||||
Now make sure to check the number of READY pods is the same as the number of running cilium pods.
|
||||
Then make sure the cilium preflight deployment is also marked READY 1/1.
|
||||
If you have an issues please refer to the CNP Validation section in the upgrade guide.
|
||||
{{- else if (and (.Values.hubble.enabled) (.Values.hubble.relay.enabled)) }}
|
||||
{{- if (.Values.hubble.ui.enabled) }}
|
||||
You have successfully installed {{ title .Chart.Name }} with Hubble Relay and Hubble UI.
|
||||
{{- else }}
|
||||
You have successfully installed {{ title .Chart.Name }} with Hubble Relay.
|
||||
{{- end }}
|
||||
{{- else if .Values.hubble.enabled }}
|
||||
You have successfully installed {{ title .Chart.Name }} with Hubble.
|
||||
{{- else }}
|
||||
You have successfully installed {{ title .Chart.Name }}.
|
||||
{{- end }}
|
||||
|
||||
Your release version is {{ .Chart.Version }}.
|
||||
|
||||
For any further help, visit https://docs.cilium.io/en/v{{ (semver .Chart.Version).Major }}.{{ (semver .Chart.Version).Minor }}/gettinghelp
|
||||
|
|
@ -0,0 +1,45 @@
|
|||
{{- define "clustermesh-apiserver-generate-certs.job.spec" }}
|
||||
{{- $certValiditySecondsStr := printf "%ds" (mul .Values.clustermesh.apiserver.tls.auto.certValidityDuration 24 60 60) -}}
|
||||
spec:
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver-generate-certs
|
||||
spec:
|
||||
serviceAccount: clustermesh-apiserver-generate-certs
|
||||
serviceAccountName: clustermesh-apiserver-generate-certs
|
||||
containers:
|
||||
- name: certgen
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.certgen.image.repository }}:{{ .Values.certgen.image.tag }}
|
||||
imagePullPolicy: {{ .Values.certgen.image.pullPolicy }}
|
||||
command:
|
||||
- "/usr/bin/cilium-certgen"
|
||||
args:
|
||||
- "--cilium-namespace={{ .Release.Namespace }}"
|
||||
- "--clustermesh-apiserver-ca-cert-reuse-secret"
|
||||
{{- if .Values.debug.enabled }}
|
||||
- "--debug"
|
||||
{{- end }}
|
||||
{{- if not (and .Values.clustermesh.apiserver.tls.ca.cert .Values.clustermesh.apiserver.tls.ca.key) }}
|
||||
- "--clustermesh-apiserver-ca-cert-generate"
|
||||
{{- end }}
|
||||
{{- if not (and .Values.clustermesh.apiserver.tls.server.cert .Values.clustermesh.apiserver.tls.server.key) }}
|
||||
- "--clustermesh-apiserver-server-cert-generate"
|
||||
{{- end }}
|
||||
{{- if not (and .Values.clustermesh.apiserver.tls.admin.cert .Values.clustermesh.apiserver.tls.admin.key) }}
|
||||
- "--clustermesh-apiserver-admin-cert-generate"
|
||||
{{- end }}
|
||||
{{- if not (and .Values.clustermesh.apiserver.tls.client.cert .Values.clustermesh.apiserver.tls.client.key) }}
|
||||
- "--clustermesh-apiserver-client-cert-generate"
|
||||
{{- end }}
|
||||
{{- if not (and .Values.clustermesh.apiserver.tls.remote.cert .Values.clustermesh.apiserver.tls.remote.key) }}
|
||||
- "--clustermesh-apiserver-remote-cert-generate"
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
restartPolicy: OnFailure
|
||||
ttlSecondsAfterFinished: {{ .Values.certgen.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,132 @@
|
|||
{{/*
|
||||
Create chart name and version as used by the chart label.
|
||||
*/}}
|
||||
{{- define "cilium.chart" -}}
|
||||
{{- printf "%s-%s" .Chart.Name .Chart.Version | replace "+" "_" | trunc 63 | trimSuffix "-" }}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Return the appropriate apiVersion for ingress.
|
||||
*/}}
|
||||
{{- define "ingress.apiVersion" -}}
|
||||
{{- if semverCompare ">=1.4-0, <1.14-0" .Capabilities.KubeVersion.Version -}}
|
||||
{{- print "extensions/v1beta1" -}}
|
||||
{{- else if semverCompare ">=1.14-0, <1.19-0" .Capabilities.KubeVersion.Version -}}
|
||||
{{- print "networking.k8s.io/v1beta1" -}}
|
||||
{{- else if semverCompare "^1.19-0" .Capabilities.KubeVersion.Version -}}
|
||||
{{- print "networking.k8s.io/v1" -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Return the appropriate backend for Hubble UI ingress.
|
||||
*/}}
|
||||
{{- define "ingress.paths" -}}
|
||||
{{ if semverCompare ">=1.4-0, <1.19-0" .Capabilities.KubeVersion.Version -}}
|
||||
backend:
|
||||
serviceName: hubble-ui
|
||||
servicePort: http
|
||||
{{- else if semverCompare "^1.19-0" .Capabilities.KubeVersion.Version -}}
|
||||
pathType: Prefix
|
||||
backend:
|
||||
service:
|
||||
name: hubble-ui
|
||||
port:
|
||||
name: http
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
{{/*
|
||||
Generate TLS certificates for Hubble Server and Hubble Relay.
|
||||
|
||||
Note: these 2 lines, that are repeated several times below, are a trick to
|
||||
ensure the CA certs are generated only once:
|
||||
|
||||
$ca := .ca | default (genCA "hubble-ca.cilium.io" (.Values.hubble.tls.auto.certValidityDuration | int))
|
||||
$_ := set . "ca" $ca
|
||||
|
||||
Please, don't try to "simplify" them as without this trick, every generated
|
||||
certificate would be signed by a different CA.
|
||||
*/}}
|
||||
{{- define "hubble.ca.gen-cert-only" }}
|
||||
{{- $ca := .ca | default (genCA "hubble-ca.cilium.io" (.Values.hubble.tls.auto.certValidityDuration | int)) -}}
|
||||
{{- $_ := set . "ca" $ca -}}
|
||||
ca.crt: |-
|
||||
{{ $ca.Cert | indent 2 -}}
|
||||
{{- end }}
|
||||
{{- define "hubble.server.gen-certs" }}
|
||||
{{- $ca := .ca | default (genCA "hubble-ca.cilium.io" (.Values.hubble.tls.auto.certValidityDuration | int)) -}}
|
||||
{{- $_ := set . "ca" $ca -}}
|
||||
{{- $cn := list "*" (.Values.cluster.name | replace "." "-") "hubble-grpc.cilium.io" | join "." }}
|
||||
{{- $cert := genSignedCert $cn nil (list $cn) (.Values.hubble.tls.auto.certValidityDuration | int) $ca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
{{- define "hubble.relay.gen-certs" }}
|
||||
{{- $ca := .ca | default (genCA "hubble-ca.cilium.io" (.Values.hubble.tls.auto.certValidityDuration | int)) -}}
|
||||
{{- $_ := set . "ca" $ca -}}
|
||||
{{- $cert := genSignedCert "*.hubble-relay.cilium.io" nil (list "*.hubble-relay.cilium.io") (.Values.hubble.tls.auto.certValidityDuration | int) $ca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate CA "vmca" for clustermesh-apiserver in the global dict. */}}
|
||||
{{- define "clustermesh.apiserver.generate.ca" }}
|
||||
{{- $ca := .cmca | default (genCA "clustermesh-apiserver-ca.cilium.io" (.Values.clustermesh.apiserver.tls.auto.certValidityDuration | int)) -}}
|
||||
{{- $_ := set . "cmca" $ca -}}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate CA certificate clustermesh-apiserver. */}}
|
||||
{{- define "clustermesh.apiserver.ca.gen-cert" }}
|
||||
{{- template "clustermesh.apiserver.generate.ca" . -}}
|
||||
ca.crt: {{ .cmca.Cert | b64enc }}
|
||||
ca.key: {{ .cmca.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate server certificate clustermesh-apiserver. */}}
|
||||
{{- define "clustermesh.apiserver.server.gen-cert" }}
|
||||
{{- template "clustermesh.apiserver.generate.ca" . }}
|
||||
{{- $CN := "clustermesh-apiserver.cilium.io" }}
|
||||
{{- $IPs := (list "127.0.0.1") }}
|
||||
{{- $SANs := (list $CN) }}
|
||||
{{- $cert := genSignedCert $CN $IPs $SANs (.Values.clustermesh.apiserver.tls.auto.certValidityDuration | int) .cmca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate admin certificate clustermesh-apiserver. */}}
|
||||
{{- define "clustermesh.apiserver.admin.gen-cert" }}
|
||||
{{- template "clustermesh.apiserver.generate.ca" . }}
|
||||
{{- $CN := "root" }}
|
||||
{{- $SANs := (list "localhost") }}
|
||||
{{- $cert := genSignedCert $CN nil $SANs (.Values.clustermesh.apiserver.tls.auto.certValidityDuration | int) .cmca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate client certificate clustermesh-apiserver. */}}
|
||||
{{- define "clustermesh.apiserver.client.gen-cert" }}
|
||||
{{- template "clustermesh.apiserver.generate.ca" . }}
|
||||
{{- $CN := "externalworkload" }}
|
||||
{{- $cert := genSignedCert $CN nil nil (.Values.clustermesh.apiserver.tls.auto.certValidityDuration | int) .cmca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{/* Generate remote certificate clustermesh-apiserver. */}}
|
||||
{{- define "clustermesh.apiserver.remote.gen-cert" }}
|
||||
{{- template "clustermesh.apiserver.generate.ca" . }}
|
||||
{{- $CN := "remote" }}
|
||||
{{- $cert := genSignedCert $CN nil nil (.Values.clustermesh.apiserver.tls.auto.certValidityDuration | int) .cmca -}}
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{- end }}
|
||||
|
||||
{{- define "system_default_registry" -}}
|
||||
{{- if .Values.global.systemDefaultRegistry -}}
|
||||
{{- printf "%s/" .Values.global.systemDefaultRegistry -}}
|
||||
{{- else -}}
|
||||
{{- "" -}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,65 @@
|
|||
{{- define "hubble-generate-certs.job.spec" }}
|
||||
{{- $certValiditySecondsStr := printf "%ds" (mul .Values.hubble.tls.auto.certValidityDuration 24 60 60) -}}
|
||||
spec:
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
k8s-app: hubble-generate-certs
|
||||
spec:
|
||||
serviceAccount: hubble-generate-certs
|
||||
serviceAccountName: hubble-generate-certs
|
||||
containers:
|
||||
- name: certgen
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.certgen.image.repository }}:{{ .Values.certgen.image.tag }}
|
||||
imagePullPolicy: {{ .Values.certgen.image.pullPolicy }}
|
||||
command:
|
||||
- "/usr/bin/cilium-certgen"
|
||||
# Because this is executed as a job, we pass the values as command
|
||||
# line args instead of via config map. This allows users to inspect
|
||||
# the values used in past runs by inspecting the completed pod.
|
||||
args:
|
||||
- "--cilium-namespace={{ .Release.Namespace }}"
|
||||
- "--hubble-ca-reuse-secret=true"
|
||||
- "--hubble-ca-secret-name=hubble-ca-secret"
|
||||
{{- if .Values.debug.enabled }}
|
||||
- "--debug"
|
||||
{{- end }}
|
||||
{{- $hubbleCAProvided := and .Values.hubble.tls.ca.cert .Values.hubble.tls.ca.key -}}
|
||||
{{- if $hubbleCAProvided }}
|
||||
- "--hubble-ca-generate=false"
|
||||
{{- else }}
|
||||
- "--hubble-ca-generate=true"
|
||||
- "--hubble-ca-validity-duration={{ $certValiditySecondsStr }}"
|
||||
- "--hubble-ca-config-map-create=true"
|
||||
- "--hubble-ca-config-map-name=hubble-ca-cert"
|
||||
{{- end }}
|
||||
{{- if and .Values.hubble.tls.server.cert .Values.hubble.tls.server.key $hubbleCAProvided }}
|
||||
- "--hubble-server-cert-generate=false"
|
||||
{{- else }}
|
||||
- "--hubble-server-cert-generate=true"
|
||||
- "--hubble-server-cert-common-name={{ list "*" (.Values.cluster.name | replace "." "-") "hubble-grpc.cilium.io" | join "." }}"
|
||||
- "--hubble-server-cert-validity-duration={{ $certValiditySecondsStr }}"
|
||||
- "--hubble-server-cert-secret-name=hubble-server-certs"
|
||||
{{- end }}
|
||||
{{- if and .Values.hubble.relay.tls.client.cert .Values.hubble.relay.tls.client.key $hubbleCAProvided }}
|
||||
- "--hubble-relay-client-cert-generate=false"
|
||||
{{- else }}
|
||||
- "--hubble-relay-client-cert-generate=true"
|
||||
- "--hubble-relay-client-cert-validity-duration={{ $certValiditySecondsStr }}"
|
||||
- "--hubble-relay-client-cert-secret-name=hubble-relay-client-certs"
|
||||
{{- end }}
|
||||
{{- if or (and .Values.hubble.relay.tls.server.cert .Values.hubble.relay.tls.server.key) (not .Values.hubble.relay.tls.server.enabled) }}
|
||||
- "--hubble-relay-server-cert-generate=false"
|
||||
{{- else if .Values.hubble.relay.tls.server.enabled }}
|
||||
- "--hubble-relay-server-cert-generate=true"
|
||||
- "--hubble-relay-server-cert-validity-duration={{ $certValiditySecondsStr }}"
|
||||
- "--hubble-relay-server-cert-secret-name=hubble-relay-server-certs"
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
restartPolicy: OnFailure
|
||||
ttlSecondsAfterFinished: {{ .Values.certgen.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,109 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) }}
|
||||
{{- /*
|
||||
Keep file in synced with cilium-preflight-clusterrole.yaml
|
||||
*/ -}}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: cilium
|
||||
rules:
|
||||
- apiGroups:
|
||||
- networking.k8s.io
|
||||
resources:
|
||||
- networkpolicies
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- discovery.k8s.io
|
||||
resources:
|
||||
- endpointslices
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- namespaces
|
||||
- services
|
||||
- nodes
|
||||
- endpoints
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pods
|
||||
- pods/finalizers
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
- delete
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
- nodes/status
|
||||
verbs:
|
||||
- patch
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
# Deprecated for removal in v1.10
|
||||
- create
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
|
||||
# This is used when validating policies in preflight. This will need to stay
|
||||
# until we figure out how to avoid "get" inside the preflight, and then
|
||||
# should be removed ideally.
|
||||
- get
|
||||
{{- if eq "k8s" .Values.tls.secretsBackend }}
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- get
|
||||
{{- end }}
|
||||
- apiGroups:
|
||||
- cilium.io
|
||||
resources:
|
||||
- ciliumnetworkpolicies
|
||||
- ciliumnetworkpolicies/status
|
||||
- ciliumnetworkpolicies/finalizers
|
||||
- ciliumclusterwidenetworkpolicies
|
||||
- ciliumclusterwidenetworkpolicies/status
|
||||
- ciliumclusterwidenetworkpolicies/finalizers
|
||||
- ciliumendpoints
|
||||
- ciliumendpoints/status
|
||||
- ciliumendpoints/finalizers
|
||||
- ciliumnodes
|
||||
- ciliumnodes/status
|
||||
- ciliumnodes/finalizers
|
||||
- ciliumidentities
|
||||
- ciliumidentities/finalizers
|
||||
- ciliumlocalredirectpolicies
|
||||
- ciliumlocalredirectpolicies/status
|
||||
- ciliumlocalredirectpolicies/finalizers
|
||||
verbs:
|
||||
- '*'
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: cilium
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: cilium
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: cilium
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,526 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) }}
|
||||
|
||||
{{- /* Default values with backwards compatibility */ -}}
|
||||
{{- $defaultKeepDeprecatedProbes := "true" -}}
|
||||
|
||||
{{- /* Default values when 1.8 was initially deployed */ -}}
|
||||
{{- if semverCompare ">=1.8" (default "1.8" .Values.upgradeCompatibility) -}}
|
||||
{{- $defaultKeepDeprecatedProbes = "false" -}}
|
||||
{{- end -}}
|
||||
|
||||
apiVersion: apps/v1
|
||||
kind: DaemonSet
|
||||
metadata:
|
||||
labels:
|
||||
k8s-app: cilium
|
||||
{{- if .Values.keepDeprecatedLabels }}
|
||||
kubernetes.io/cluster-service: "true"
|
||||
{{- if and (eq .Release.Namespace "kube-system" ) .Values.gke.enabled }}
|
||||
{{- fail "Invalid configuration: Installing Cilium on GKE with 'kubernetes.io/cluster-service' labels on 'kube-system' namespace causes Cilium DaemonSet to be removed by GKE. Either install Cilium on a different Namespace or install with '--set keepDeprecatedLabels=false'"}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
name: cilium
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: cilium
|
||||
{{- if .Values.keepDeprecatedLabels }}
|
||||
kubernetes.io/cluster-service: "true"
|
||||
{{- end }}
|
||||
{{- with .Values.updateStrategy }}
|
||||
updateStrategy:
|
||||
{{- toYaml . | trim | nindent 4 }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
{{- if and .Values.prometheus.enabled (not .Values.prometheus.serviceMonitor.enabled) }}
|
||||
prometheus.io/port: "{{ .Values.prometheus.port }}"
|
||||
prometheus.io/scrape: "true"
|
||||
{{- end }}
|
||||
{{- if .Values.rollOutCiliumPods }}
|
||||
# ensure pods roll when configmap updates
|
||||
cilium.io/cilium-configmap-checksum: {{ include (print $.Template.BasePath "/cilium-configmap.yaml") . | sha256sum | quote }}
|
||||
{{- end }}
|
||||
# This annotation plus the CriticalAddonsOnly toleration makes
|
||||
# cilium to be a critical pod in the cluster, which ensures cilium
|
||||
# gets priority scheduling.
|
||||
# https://kubernetes.io/docs/tasks/administer-cluster/guaranteed-scheduling-critical-addon-pods/
|
||||
scheduler.alpha.kubernetes.io/critical-pod: ""
|
||||
{{- with .Values.podAnnotations }}
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
k8s-app: cilium
|
||||
{{- if .Values.keepDeprecatedLabels }}
|
||||
kubernetes.io/cluster-service: "true"
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.affinity }}
|
||||
affinity:
|
||||
{{ toYaml .Values.affinity | indent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
{{- if .Values.sleepAfterInit }}
|
||||
- command: [ "/bin/bash", "-c", "--" ]
|
||||
args: [ "while true; do sleep 30; done;" ]
|
||||
livenessProbe:
|
||||
exec:
|
||||
command:
|
||||
- "true"
|
||||
readinessProbe:
|
||||
exec:
|
||||
command:
|
||||
- "true"
|
||||
{{- else }}
|
||||
- args:
|
||||
- --config-dir=/tmp/cilium/config-map
|
||||
{{- range $key, $value := .Values.extraArgs }}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
command:
|
||||
- cilium-agent
|
||||
livenessProbe:
|
||||
{{- if or .Values.keepDeprecatedProbes (eq $defaultKeepDeprecatedProbes "true") }}
|
||||
exec:
|
||||
command:
|
||||
- cilium
|
||||
- status
|
||||
- --brief
|
||||
{{- else }}
|
||||
httpGet:
|
||||
{{- if .Values.ipv4.enabled }}
|
||||
host: '127.0.0.1'
|
||||
{{- else }}
|
||||
host: '::1'
|
||||
{{- end }}
|
||||
path: /healthz
|
||||
port: {{ .Values.healthPort }}
|
||||
scheme: HTTP
|
||||
httpHeaders:
|
||||
- name: "brief"
|
||||
value: "true"
|
||||
{{- end }}
|
||||
failureThreshold: 10
|
||||
# The initial delay for the liveness probe is intentionally large to
|
||||
# avoid an endless kill & restart cycle if in the event that the initial
|
||||
# bootstrapping takes longer than expected.
|
||||
initialDelaySeconds: 120
|
||||
periodSeconds: 30
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 5
|
||||
readinessProbe:
|
||||
{{- if or .Values.keepDeprecatedProbes (eq $defaultKeepDeprecatedProbes "true") }}
|
||||
exec:
|
||||
command:
|
||||
- cilium
|
||||
- status
|
||||
- --brief
|
||||
{{- else }}
|
||||
httpGet:
|
||||
{{- if .Values.ipv4.enabled }}
|
||||
host: '127.0.0.1'
|
||||
{{- else }}
|
||||
host: '::1'
|
||||
{{- end }}
|
||||
path: /healthz
|
||||
port: {{ .Values.healthPort }}
|
||||
scheme: HTTP
|
||||
httpHeaders:
|
||||
- name: "brief"
|
||||
value: "true"
|
||||
{{- end }}
|
||||
failureThreshold: 3
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 30
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 5
|
||||
{{- end }}
|
||||
env:
|
||||
- name: K8S_NODE_NAME
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: spec.nodeName
|
||||
- name: CILIUM_K8S_NAMESPACE
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
- name: CILIUM_FLANNEL_MASTER_DEVICE
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: flannel-master-device
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: CILIUM_FLANNEL_UNINSTALL_ON_EXIT
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: flannel-uninstall-on-exit
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: CILIUM_CLUSTERMESH_CONFIG
|
||||
value: /var/lib/cilium/clustermesh/
|
||||
- name: CILIUM_CNI_CHAINING_MODE
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: cni-chaining-mode
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: CILIUM_CUSTOM_CNI_CONF
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: custom-cni-conf
|
||||
name: cilium-config
|
||||
optional: true
|
||||
{{- if .Values.k8sServiceHost }}
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: {{ .Values.k8sServiceHost | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServicePort }}
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: {{ .Values.k8sServicePort | quote }}
|
||||
{{- end }}
|
||||
{{- with .Values.extraEnv }}
|
||||
{{ toYaml . | trim | indent 8 }}
|
||||
{{- end }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.image.repository }}:{{ .Values.image.tag }}
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
{{- if .Values.cni.install }}
|
||||
lifecycle:
|
||||
postStart:
|
||||
exec:
|
||||
command:
|
||||
- "/cni-install.sh"
|
||||
-{{- if .Values.debug.enabled }} "--enable-debug=true"{{- else }} "--enable-debug=false"{{- end }}
|
||||
preStop:
|
||||
exec:
|
||||
command:
|
||||
- /cni-uninstall.sh
|
||||
{{- end }}
|
||||
{{- if .Values.resources }}
|
||||
resources:
|
||||
{{- toYaml .Values.resources | trim | nindent 10 }}
|
||||
{{- end }}
|
||||
name: cilium-agent
|
||||
{{- if or .Values.prometheus.enabled .Values.hubble.metrics.enabled }}
|
||||
ports:
|
||||
{{- if .Values.prometheus.enabled }}
|
||||
- containerPort: {{ .Values.prometheus.port }}
|
||||
hostPort: {{ .Values.prometheus.port }}
|
||||
name: prometheus
|
||||
protocol: TCP
|
||||
- containerPort: {{ .Values.proxy.prometheus.port }}
|
||||
hostPort: {{ .Values.proxy.prometheus.port }}
|
||||
name: envoy-metrics
|
||||
protocol: TCP
|
||||
{{- end }}
|
||||
{{- if .Values.hubble.metrics.enabled }}
|
||||
- containerPort: {{ .Values.hubble.metrics.port }}
|
||||
hostPort: {{ .Values.hubble.metrics.port }}
|
||||
name: hubble-metrics
|
||||
protocol: TCP
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
capabilities:
|
||||
add:
|
||||
- NET_ADMIN
|
||||
- SYS_MODULE
|
||||
privileged: true
|
||||
volumeMounts:
|
||||
{{- /* CRI-O already mounts the BPF filesystem */ -}}
|
||||
{{- if not (eq .Values.containerRuntime.integration "crio") }}
|
||||
- mountPath: /sys/fs/bpf
|
||||
name: bpf-maps
|
||||
{{- end }}
|
||||
- mountPath: /var/run/cilium
|
||||
name: cilium-run
|
||||
- mountPath: /host/opt/cni/bin
|
||||
name: cni-path
|
||||
- mountPath: {{ .Values.cni.hostConfDirMountPath }}
|
||||
name: etc-cni-netd
|
||||
{{- if .Values.etcd.enabled }}
|
||||
- mountPath: /var/lib/etcd-config
|
||||
name: etcd-config-path
|
||||
readOnly: true
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- mountPath: /var/lib/etcd-secrets
|
||||
name: etcd-secrets
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
- mountPath: /var/lib/cilium/clustermesh
|
||||
name: clustermesh-secrets
|
||||
readOnly: true
|
||||
- mountPath: /tmp/cilium/config-map
|
||||
name: cilium-config-path
|
||||
readOnly: true
|
||||
{{- if .Values.ipMasqAgent.enabled }}
|
||||
- mountPath: /etc/config
|
||||
name: ip-masq-agent
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if .Values.cni.configMap }}
|
||||
- mountPath: {{ .Values.cni.confFileMountPath }}
|
||||
name: cni-configuration
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
# Needed to be able to load kernel modules
|
||||
- mountPath: /lib/modules
|
||||
name: lib-modules
|
||||
readOnly: true
|
||||
- mountPath: /run/xtables.lock
|
||||
name: xtables-lock
|
||||
{{- if .Values.encryption.enabled }}
|
||||
- mountPath: {{ .Values.encryption.mountPath }}
|
||||
name: cilium-ipsec-secrets
|
||||
{{- end }}
|
||||
{{- if .Values.kubeConfigPath }}
|
||||
- mountPath: {{ .Values.kubeConfigPath }}
|
||||
name: kube-config
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if and (.Values.hubble.enabled) (hasKey .Values.hubble "listenAddress") (.Values.hubble.tls.enabled) }}
|
||||
- mountPath: /var/lib/cilium/tls/hubble
|
||||
name: hubble-tls
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- range .Values.extraHostPathMounts }}
|
||||
- mountPath: {{ .mountPath }}
|
||||
name: {{ .name }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- if .mountPropagation }}
|
||||
mountPropagation: {{ .mountPropagation }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.monitor.enabled }}
|
||||
- name: cilium-monitor
|
||||
command: ["cilium"]
|
||||
args:
|
||||
- monitor
|
||||
{{- range $type := .Values.monitor.eventTypes }}
|
||||
- --type={{ $type }}
|
||||
{{- end }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.image.repository }}:{{ .Values.image.tag }}
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
volumeMounts:
|
||||
- mountPath: /var/run/cilium
|
||||
name: cilium-run
|
||||
{{- if .Values.monitor.resources }}
|
||||
resources:
|
||||
{{- toYaml .Values.monitor.resources | trim | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if (and .Values.etcd.managed (not .Values.etcd.k8sService)) }}
|
||||
# In managed etcd mode, Cilium must be able to resolve the DNS name of
|
||||
# the etcd service
|
||||
dnsPolicy: ClusterFirstWithHostNet
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
initContainers:
|
||||
{{- if and .Values.nodeinit.enabled (not (eq .Values.nodeinit.bootstrapFile "")) }}
|
||||
- name: wait-for-node-init
|
||||
command: ['sh', '-c', 'until stat {{ .Values.nodeinit.bootstrapFile }} > /dev/null 2>&1; do echo "Waiting on node-init to run..."; sleep 1; done']
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.image.repository }}:{{ .Values.image.tag }}
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
securityContext:
|
||||
privileged: true
|
||||
volumeMounts:
|
||||
- mountPath: {{ .Values.nodeinit.bootstrapFile }}
|
||||
name: cilium-bootstrap-file
|
||||
{{- end }}
|
||||
- command:
|
||||
- /init-container.sh
|
||||
env:
|
||||
- name: CILIUM_ALL_STATE
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: clean-cilium-state
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: CILIUM_BPF_STATE
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: clean-cilium-bpf-state
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: CILIUM_WAIT_BPF_MOUNT
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: wait-bpf-mount
|
||||
name: cilium-config
|
||||
optional: true
|
||||
{{- if .Values.k8sServiceHost }}
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: {{ .Values.k8sServiceHost | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServicePort }}
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: {{ .Values.k8sServicePort | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.extraEnv }}
|
||||
{{ toYaml .Values.extraEnv | indent 8 }}
|
||||
{{- end }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.image.repository }}:{{ .Values.image.tag }}
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
name: clean-cilium-state
|
||||
securityContext:
|
||||
capabilities:
|
||||
add:
|
||||
- NET_ADMIN
|
||||
privileged: true
|
||||
volumeMounts:
|
||||
{{- /* CRI-O already mounts the BPF filesystem */ -}}
|
||||
{{- if not (eq .Values.containerRuntime.integration "crio") }}
|
||||
- mountPath: /sys/fs/bpf
|
||||
name: bpf-maps
|
||||
{{- /* Required for wait-bpf-mount to work */}}
|
||||
mountPropagation: HostToContainer
|
||||
{{- end }}
|
||||
- mountPath: /var/run/cilium
|
||||
name: cilium-run
|
||||
{{- if .Values.nodeinit.resources }}
|
||||
resources:
|
||||
{{- toYaml .Values.nodeinit.resources | trim | nindent 10 }}
|
||||
{{- end }}
|
||||
restartPolicy: Always
|
||||
{{- if and (or (and (eq .Release.Namespace "kube-system") (gt .Capabilities.KubeVersion.Minor "10")) (ge .Capabilities.KubeVersion.Minor "17") (gt .Capabilities.KubeVersion.Major "1")) .Values.enableCriticalPriorityClass }}
|
||||
priorityClassName: system-node-critical
|
||||
{{- end }}
|
||||
serviceAccount: cilium
|
||||
serviceAccountName: cilium
|
||||
terminationGracePeriodSeconds: 1
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
volumes:
|
||||
# To keep state between restarts / upgrades
|
||||
- hostPath:
|
||||
path: {{ .Values.daemon.runPath }}
|
||||
type: DirectoryOrCreate
|
||||
name: cilium-run
|
||||
{{- /* CRI-O already mounts the BPF filesystem */ -}}
|
||||
{{- if not (eq .Values.containerRuntime.integration "crio") }}
|
||||
# To keep state between restarts / upgrades for bpf maps
|
||||
- hostPath:
|
||||
path: /sys/fs/bpf
|
||||
type: DirectoryOrCreate
|
||||
name: bpf-maps
|
||||
{{- end }}
|
||||
# To install cilium cni plugin in the host
|
||||
- hostPath:
|
||||
path: {{ .Values.cni.binPath }}
|
||||
type: DirectoryOrCreate
|
||||
name: cni-path
|
||||
# To install cilium cni configuration in the host
|
||||
- hostPath:
|
||||
path: {{ .Values.cni.confPath }}
|
||||
type: DirectoryOrCreate
|
||||
name: etc-cni-netd
|
||||
# To be able to load kernel modules
|
||||
- hostPath:
|
||||
path: /lib/modules
|
||||
name: lib-modules
|
||||
# To access iptables concurrently with other processes (e.g. kube-proxy)
|
||||
- hostPath:
|
||||
path: /run/xtables.lock
|
||||
type: FileOrCreate
|
||||
name: xtables-lock
|
||||
{{- if .Values.kubeConfigPath }}
|
||||
- hostPath:
|
||||
path: {{ .Values.kubeConfigPath }}
|
||||
type: FileOrCreate
|
||||
name: kube-config
|
||||
{{- end }}
|
||||
{{- if and .Values.nodeinit.enabled (not (eq .Values.nodeinit.bootstrapFile "")) }}
|
||||
- hostPath:
|
||||
path: {{ .Values.nodeinit.bootstrapFile }}
|
||||
type: FileOrCreate
|
||||
name: cilium-bootstrap-file
|
||||
{{- end }}
|
||||
{{- range .Values.extraHostPathMounts }}
|
||||
- name: {{ .name }}
|
||||
hostPath:
|
||||
path: {{ .hostPath }}
|
||||
{{- if .hostPathType }}
|
||||
type: {{ .hostPathType }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.etcd.enabled }}
|
||||
# To read the etcd config stored in config maps
|
||||
- configMap:
|
||||
defaultMode: 420
|
||||
items:
|
||||
- key: etcd-config
|
||||
path: etcd.config
|
||||
name: cilium-config
|
||||
name: etcd-config-path
|
||||
# To read the k8s etcd secrets in case the user might want to use TLS
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- name: etcd-secrets
|
||||
secret:
|
||||
defaultMode: 420
|
||||
optional: true
|
||||
secretName: cilium-etcd-secrets
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
# To read the clustermesh configuration
|
||||
- name: clustermesh-secrets
|
||||
secret:
|
||||
defaultMode: 420
|
||||
optional: true
|
||||
secretName: cilium-clustermesh
|
||||
# To read the configuration from the config map
|
||||
- configMap:
|
||||
name: cilium-config
|
||||
name: cilium-config-path
|
||||
{{- if and .Values.ipMasqAgent .Values.ipMasqAgent.enabled }}
|
||||
- configMap:
|
||||
name: ip-masq-agent
|
||||
optional: true
|
||||
items:
|
||||
- key: config
|
||||
path: ip-masq-agent
|
||||
name: ip-masq-agent
|
||||
{{- end }}
|
||||
{{- if .Values.encryption.enabled }}
|
||||
- name: cilium-ipsec-secrets
|
||||
secret:
|
||||
secretName: {{ .Values.encryption.secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.cni.configMap }}
|
||||
- name: cni-configuration
|
||||
configMap:
|
||||
name: {{ .Values.cni.configMap }}
|
||||
{{- end }}
|
||||
{{- if and .Values.hubble.enabled .Values.hubble.tls.enabled (hasKey .Values.hubble "listenAddress") }}
|
||||
- name: hubble-tls
|
||||
projected:
|
||||
sources:
|
||||
- secret:
|
||||
name: hubble-server-certs
|
||||
items:
|
||||
- key: tls.crt
|
||||
path: server.crt
|
||||
- key: tls.key
|
||||
path: server.key
|
||||
optional: true
|
||||
- configMap:
|
||||
name: hubble-ca-cert
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: client-ca.crt
|
||||
optional: true
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,67 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) (.Values.prometheus.enabled) (.Values.prometheus.serviceMonitor.enabled) }}
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: cilium-agent
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: cilium
|
||||
spec:
|
||||
clusterIP: None
|
||||
type: ClusterIP
|
||||
ports:
|
||||
- name: metrics
|
||||
port: {{ .Values.prometheus.port }}
|
||||
protocol: TCP
|
||||
targetPort: prometheus
|
||||
- name: envoy-metrics
|
||||
port: {{ .Values.proxy.prometheus.port }}
|
||||
protocol: TCP
|
||||
targetPort: envoy-metrics
|
||||
selector:
|
||||
k8s-app: cilium
|
||||
{{- else if .Values.prometheus.enabled }}
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: cilium-agent
|
||||
namespace: {{ .Release.Namespace }}
|
||||
annotations:
|
||||
prometheus.io/scrape: 'true'
|
||||
prometheus.io/port: {{ .Values.proxy.prometheus.port | quote }}
|
||||
labels:
|
||||
k8s-app: cilium
|
||||
spec:
|
||||
clusterIP: None
|
||||
type: ClusterIP
|
||||
ports:
|
||||
- name: envoy-metrics
|
||||
port: {{ .Values.proxy.prometheus.port }}
|
||||
protocol: TCP
|
||||
targetPort: envoy-metrics
|
||||
selector:
|
||||
k8s-app: cilium
|
||||
{{- end }}
|
||||
{{- if and .Values.hubble.metrics.enabled }}
|
||||
---
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: hubble-metrics
|
||||
namespace: {{ .Release.Namespace }}
|
||||
annotations:
|
||||
prometheus.io/scrape: 'true'
|
||||
prometheus.io/port: {{ .Values.hubble.metrics.port | quote }}
|
||||
labels:
|
||||
k8s-app: hubble
|
||||
spec:
|
||||
clusterIP: None
|
||||
type: ClusterIP
|
||||
ports:
|
||||
- name: hubble-metrics
|
||||
port: {{ .Values.hubble.metrics.port }}
|
||||
protocol: TCP
|
||||
targetPort: hubble-metrics
|
||||
selector:
|
||||
k8s-app: cilium
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: cilium
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccounts.cilium.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccounts.cilium.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,55 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) (.Values.prometheus.enabled) (.Values.prometheus.serviceMonitor.enabled) }}
|
||||
---
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: cilium-agent
|
||||
{{- if .Values.prometheus.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.prometheus.serviceMonitor.namespace }}
|
||||
{{- else }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: cilium
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
endpoints:
|
||||
- port: metrics
|
||||
interval: 10s
|
||||
honorLabels: true
|
||||
path: /metrics
|
||||
targetLabels:
|
||||
- k8s-app
|
||||
{{- end }}
|
||||
{{- if and .Values.hubble.metrics.enabled (.Values.hubble.metrics.serviceMonitor.enabled) }}
|
||||
---
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: hubble
|
||||
{{- if .Values.prometheus.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.prometheus.serviceMonitor.namespace }}
|
||||
{{- else }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: hubble
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
endpoints:
|
||||
- port: hubble-metrics
|
||||
interval: 10s
|
||||
honorLabels: true
|
||||
path: /metrics
|
||||
relabelings:
|
||||
- replacement: ${1}
|
||||
sourceLabels:
|
||||
- __meta_kubernetes_pod_node_name
|
||||
targetLabel: node
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,649 @@
|
|||
{{- if and (.Values.agent) (not .Values.preflight.enabled) }}
|
||||
{{- /* Default values with backwards compatibility */ -}}
|
||||
{{- $defaultEnableCnpStatusUpdates := "true" -}}
|
||||
{{- $defaultBpfMapDynamicSizeRatio := 0.0 -}}
|
||||
{{- $defaultBpfMasquerade := "false" -}}
|
||||
{{- $defaultBpfClockProbe := "false" -}}
|
||||
{{- $defaultBpfTProxy := "false" -}}
|
||||
{{- $defaultIPAM := "cluster-pool" -}}
|
||||
{{- $defaultSessionAffinity := "false" -}}
|
||||
{{- $defaultOperatorApiServeAddr := "localhost:9234" -}}
|
||||
{{- $defaultBpfCtTcpMax := 524288 -}}
|
||||
{{- $defaultBpfCtAnyMax := 262144 -}}
|
||||
{{- $enableIdentityMark := "true" -}}
|
||||
{{- $fragmentTracking := "true" -}}
|
||||
{{- $crdWaitTimeout := "5m" -}}
|
||||
|
||||
{{- /* Default values when 1.8 was initially deployed */ -}}
|
||||
{{- if semverCompare ">=1.8" (default "1.8" .Values.upgradeCompatibility) -}}
|
||||
{{- $defaultEnableCnpStatusUpdates = "false" -}}
|
||||
{{- $defaultBpfMapDynamicSizeRatio = 0.0025 -}}
|
||||
{{- $defaultBpfMasquerade = "true" -}}
|
||||
{{- $defaultBpfClockProbe = "true" -}}
|
||||
{{- $defaultIPAM = "cluster-pool" -}}
|
||||
{{- $defaultSessionAffinity = "true" -}}
|
||||
{{- if .Values.ipv4.enabled }}
|
||||
{{- $defaultOperatorApiServeAddr = "127.0.0.1:9234" -}}
|
||||
{{- else -}}
|
||||
{{- $defaultOperatorApiServeAddr = "[::1]:9234" -}}
|
||||
{{- end }}
|
||||
{{- $defaultBpfCtTcpMax = 0 -}}
|
||||
{{- $defaultBpfCtAnyMax = 0 -}}
|
||||
{{- end -}}
|
||||
|
||||
{{- $ipam := (coalesce .Values.ipam.mode $defaultIPAM) -}}
|
||||
{{- $bpfCtTcpMax := (coalesce .Values.bpf.ctTcpMax $defaultBpfCtTcpMax) -}}
|
||||
{{- $bpfCtAnyMax := (coalesce .Values.bpf.ctAnyMax $defaultBpfCtAnyMax) -}}
|
||||
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: cilium-config
|
||||
namespace: {{ .Release.Namespace }}
|
||||
data:
|
||||
{{- if .Values.etcd.enabled }}
|
||||
# The kvstore configuration is used to enable use of a kvstore for state
|
||||
# storage. This can either be provided with an external kvstore or with the
|
||||
# help of cilium-etcd-operator which operates an etcd cluster automatically.
|
||||
kvstore: etcd
|
||||
{{- if .Values.etcd.k8sService }}
|
||||
kvstore-opt: '{"etcd.config": "/var/lib/etcd-config/etcd.config", "etcd.operator": "true"}'
|
||||
{{- else }}
|
||||
kvstore-opt: '{"etcd.config": "/var/lib/etcd-config/etcd.config"}'
|
||||
{{- end }}
|
||||
|
||||
# This etcd-config contains the etcd endpoints of your cluster. If you use
|
||||
# TLS please make sure you follow the tutorial in https://cilium.link/etcd-config
|
||||
etcd-config: |-
|
||||
---
|
||||
endpoints:
|
||||
{{- if .Values.etcd.managed }}
|
||||
- https://cilium-etcd-client.{{ .Release.Namespace }}.svc:2379
|
||||
{{- else }}
|
||||
{{- range .Values.etcd.endpoints }}
|
||||
- {{ . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
trusted-ca-file: '/var/lib/etcd-secrets/etcd-client-ca.crt'
|
||||
key-file: '/var/lib/etcd-secrets/etcd-client.key'
|
||||
cert-file: '/var/lib/etcd-secrets/etcd-client.crt'
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "conntrackGCInterval" }}
|
||||
conntrack-gc-interval: {{ .Values.conntrackGCInterval | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "disableEnvoyVersionCheck" }}
|
||||
disable-envoy-version-check: {{ .Values.disableEnvoyVersionCheck | quote }}
|
||||
{{- end }}
|
||||
|
||||
# Identity allocation mode selects how identities are shared between cilium
|
||||
# nodes by setting how they are stored. The options are "crd" or "kvstore".
|
||||
# - "crd" stores identities in kubernetes as CRDs (custom resource definition).
|
||||
# These can be queried with:
|
||||
# kubectl get ciliumid
|
||||
# - "kvstore" stores identities in a kvstore, etcd or consul, that is
|
||||
# configured below. Cilium versions before 1.6 supported only the kvstore
|
||||
# backend. Upgrades from these older cilium versions should continue using
|
||||
# the kvstore by commenting out the identity-allocation-mode below, or
|
||||
# setting it to "kvstore".
|
||||
identity-allocation-mode: {{ .Values.identityAllocationMode }}
|
||||
{{- if hasKey .Values "identityHeartbeatTimeout" }}
|
||||
identity-heartbeat-timeout: "{{ .Values.identityHeartbeatTimeout }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "identityGCInterval" }}
|
||||
identity-gc-interval: "{{ .Values.identityGCInterval }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.operator "endpointGCInterval" }}
|
||||
cilium-endpoint-gc-interval: "{{ .Values.operator.endpointGCInterval }}"
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "identityChangeGracePeriod" }}
|
||||
# identity-change-grace-period is the grace period that needs to pass
|
||||
# before an endpoint that has changed its identity will start using
|
||||
# that new identity. During the grace period, the new identity has
|
||||
# already been allocated and other nodes in the cluster have a chance
|
||||
# to whitelist the new upcoming identity of the endpoint.
|
||||
identity-change-grace-period: {{ default "5s" .Values.identityChangeGracePeriod | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "labels" }}
|
||||
# To include or exclude matched resources from cilium identity evaluation
|
||||
labels: {{ .Values.labels | quote }}
|
||||
{{- end }}
|
||||
|
||||
# If you want to run cilium in debug mode change this value to true
|
||||
debug: {{ .Values.debug.enabled | quote }}
|
||||
|
||||
{{- if hasKey .Values.debug "verbose" }}
|
||||
debug-verbose: "{{ .Values.debug.verbose }}"
|
||||
{{- end }}
|
||||
|
||||
{{- if ne (int .Values.healthPort) 9876 }}
|
||||
# Set the TCP port for the agent health status API. This is not the port used
|
||||
# for cilium-health.
|
||||
agent-health-port: "{{ .Values.healthPort }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "policyEnforcementMode" }}
|
||||
# The agent can be put into the following three policy enforcement modes
|
||||
# default, always and never.
|
||||
# https://docs.cilium.io/en/latest/policy/intro/#policy-enforcement-modes
|
||||
enable-policy: "{{ lower .Values.policyEnforcementMode }}"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.prometheus.enabled }}
|
||||
# If you want metrics enabled in all of your Cilium agents, set the port for
|
||||
# which the Cilium agents will have their metrics exposed.
|
||||
# This option deprecates the "prometheus-serve-addr" in the
|
||||
# "cilium-metrics-config" ConfigMap
|
||||
# NOTE that this will open the port on ALL nodes where Cilium pods are
|
||||
# scheduled.
|
||||
prometheus-serve-addr: ":{{ .Values.prometheus.port }}"
|
||||
# Port to expose Envoy metrics (e.g. "9095"). Envoy metrics listener will be disabled if this
|
||||
# field is not set.
|
||||
proxy-prometheus-port: "{{ .Values.proxy.prometheus.port }}"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.operator.prometheus.enabled }}
|
||||
# If you want metrics enabled in cilium-operator, set the port for
|
||||
# which the Cilium Operator will have their metrics exposed.
|
||||
# NOTE that this will open the port on the nodes where Cilium operator pod
|
||||
# is scheduled.
|
||||
operator-prometheus-serve-addr: ":{{ .Values.operator.prometheus.port }}"
|
||||
enable-metrics: "true"
|
||||
{{- end }}
|
||||
|
||||
# Enable IPv4 addressing. If enabled, all endpoints are allocated an IPv4
|
||||
# address.
|
||||
enable-ipv4: {{ .Values.ipv4.enabled | quote }}
|
||||
|
||||
# Enable IPv6 addressing. If enabled, all endpoints are allocated an IPv6
|
||||
# address.
|
||||
enable-ipv6: {{ .Values.ipv6.enabled | quote }}
|
||||
|
||||
{{- if .Values.cleanState }}
|
||||
# If a serious issue occurs during Cilium startup, this
|
||||
# invasive option may be set to true to remove all persistent
|
||||
# state. Endpoints will not be restored using knowledge from a
|
||||
# prior Cilium run, so they may receive new IP addresses upon
|
||||
# restart. This also triggers clean-cilium-bpf-state.
|
||||
clean-cilium-state: "true"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.cleanBpfState }}
|
||||
# If you want to clean cilium BPF state, set this to true;
|
||||
# Removes all BPF maps from the filesystem. Upon restart,
|
||||
# endpoints are restored with the same IP addresses, however
|
||||
# any ongoing connections may be disrupted briefly.
|
||||
# Loadbalancing decisions will be reset, so any ongoing
|
||||
# connections via a service may be loadbalanced to a different
|
||||
# backend after restart.
|
||||
clean-cilium-bpf-state: "true"
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values.cni "customConf" }}
|
||||
# Users who wish to specify their own custom CNI configuration file must set
|
||||
# custom-cni-conf to "true", otherwise Cilium may overwrite the configuration.
|
||||
custom-cni-conf: "{{ .Values.cni.customConf }}"
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "bpfClockProbe" }}
|
||||
enable-bpf-clock-probe: {{ .Values.bpfClockProbe | quote }}
|
||||
{{- else if eq $defaultBpfClockProbe "true" }}
|
||||
enable-bpf-clock-probe: {{ $defaultBpfClockProbe | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values.bpf "tproxy" }}
|
||||
enable-bpf-tproxy: {{ .Values.bpf.tproxy | quote }}
|
||||
{{- else if eq $defaultBpfTProxy "true" }}
|
||||
enable-bpf-tproxy: {{ $defaultBpfTProxy | quote }}
|
||||
{{- end }}
|
||||
# If you want cilium monitor to aggregate tracing for packets, set this level
|
||||
# to "low", "medium", or "maximum". The higher the level, the less packets
|
||||
# that will be seen in monitor output.
|
||||
monitor-aggregation: {{ .Values.bpf.monitorAggregation }}
|
||||
|
||||
# The monitor aggregation interval governs the typical time between monitor
|
||||
# notification events for each allowed connection.
|
||||
#
|
||||
# Only effective when monitor aggregation is set to "medium" or higher.
|
||||
monitor-aggregation-interval: {{ .Values.bpf.monitorInterval }}
|
||||
|
||||
# The monitor aggregation flags determine which TCP flags which, upon the
|
||||
# first observation, cause monitor notifications to be generated.
|
||||
#
|
||||
# Only effective when monitor aggregation is set to "medium" or higher.
|
||||
monitor-aggregation-flags: {{ .Values.bpf.monitorFlags }}
|
||||
|
||||
|
||||
|
||||
|
||||
{{- if hasKey .Values.bpf "mapDynamicSizeRatio" }}
|
||||
# Specifies the ratio (0.0-1.0) of total system memory to use for dynamic
|
||||
# sizing of the TCP CT, non-TCP CT, NAT and policy BPF maps.
|
||||
bpf-map-dynamic-size-ratio: {{ .Values.bpf.mapDynamicSizeRatio | quote }}
|
||||
{{- else if ne $defaultBpfMapDynamicSizeRatio 0.0 }}
|
||||
# Specifies the ratio (0.0-1.0) of total system memory to use for dynamic
|
||||
# sizing of the TCP CT, non-TCP CT, NAT and policy BPF maps.
|
||||
bpf-map-dynamic-size-ratio: {{ $defaultBpfMapDynamicSizeRatio | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values.bpf "hostRouting" }}
|
||||
enable-host-legacy-routing: {{ .Values.bpf.hostRouting | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if or $bpfCtTcpMax $bpfCtAnyMax }}
|
||||
# bpf-ct-global-*-max specifies the maximum number of connections
|
||||
# supported across all endpoints, split by protocol: tcp or other. One pair
|
||||
# of maps uses these values for IPv4 connections, and another pair of maps
|
||||
# use these values for IPv6 connections.
|
||||
#
|
||||
# If these values are modified, then during the next Cilium startup the
|
||||
# tracking of ongoing connections may be disrupted. As a result, reply
|
||||
# packets may be dropped and the load-balancing decisions for established
|
||||
# connections may change.
|
||||
#
|
||||
# For users upgrading from Cilium 1.2 or earlier, to minimize disruption
|
||||
# during the upgrade process, set bpf-ct-global-tcp-max to 1000000.
|
||||
{{- if $bpfCtTcpMax }}
|
||||
bpf-ct-global-tcp-max: {{ $bpfCtTcpMax | quote }}
|
||||
{{- end }}
|
||||
{{- if $bpfCtAnyMax }}
|
||||
bpf-ct-global-any-max: {{ $bpfCtAnyMax | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.bpf "natMax" }}
|
||||
# bpf-nat-global-max specified the maximum number of entries in the
|
||||
# BPF NAT table.
|
||||
bpf-nat-global-max: "{{ .Values.bpf.natMax }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.bpf "neighMax" }}
|
||||
# bpf-neigh-global-max specified the maximum number of entries in the
|
||||
# BPF neighbor table.
|
||||
bpf-neigh-global-max: "{{ .Values.bpf.neighMax }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.bpf "policyMapMax" }}
|
||||
# bpf-policy-map-max specifies the maximum number of entries in endpoint
|
||||
# policy map (per endpoint)
|
||||
bpf-policy-map-max: "{{ .Values.bpf.policyMapMax }}"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.bpf "lbMapMax" }}
|
||||
# bpf-lb-map-max specifies the maximum number of entries in bpf lb service,
|
||||
# backend and affinity maps.
|
||||
bpf-lb-map-max: "{{ .Values.bpf.lbMapMax }}"
|
||||
{{- end }}
|
||||
# Pre-allocation of map entries allows per-packet latency to be reduced, at
|
||||
# the expense of up-front memory allocation for the entries in the maps. The
|
||||
# default value below will minimize memory usage in the default installation;
|
||||
# users who are sensitive to latency may consider setting this to "true".
|
||||
#
|
||||
# This option was introduced in Cilium 1.4. Cilium 1.3 and earlier ignore
|
||||
# this option and behave as though it is set to "true".
|
||||
#
|
||||
# If this value is modified, then during the next Cilium startup the restore
|
||||
# of existing endpoints and tracking of ongoing connections may be disrupted.
|
||||
# As a result, reply packets may be dropped and the load-balancing decisions
|
||||
# for established connections may change.
|
||||
#
|
||||
# If this option is set to "false" during an upgrade from 1.3 or earlier to
|
||||
# 1.4 or later, then it may cause one-time disruptions during the upgrade.
|
||||
preallocate-bpf-maps: "{{ .Values.bpf.preallocateMaps }}"
|
||||
|
||||
# Regular expression matching compatible Istio sidecar istio-proxy
|
||||
# container image names
|
||||
sidecar-istio-proxy-image: "{{ .Values.proxy.sidecarImageRegex }}"
|
||||
|
||||
# Name of the cluster. Only relevant when building a mesh of clusters.
|
||||
cluster-name: {{ .Values.cluster.name }}
|
||||
|
||||
{{- if hasKey .Values.cluster "id" }}
|
||||
# Unique ID of the cluster. Must be unique across all conneted clusters and
|
||||
# in the range of 1 and 255. Only relevant when building a mesh of clusters.
|
||||
cluster-id: "{{ .Values.cluster.id }}"
|
||||
{{- end }}
|
||||
|
||||
# Encapsulation mode for communication between nodes
|
||||
# Possible values:
|
||||
# - disabled
|
||||
# - vxlan (default)
|
||||
# - geneve
|
||||
{{- if .Values.gke.enabled }}
|
||||
tunnel: "disabled"
|
||||
enable-endpoint-routes: "true"
|
||||
enable-local-node-route: "false"
|
||||
{{- else }}
|
||||
tunnel: {{ .Values.tunnel }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.eni }}
|
||||
enable-endpoint-routes: "true"
|
||||
auto-create-cilium-node-resource: "true"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.azure.enabled }}
|
||||
enable-endpoint-routes: "true"
|
||||
auto-create-cilium-node-resource: "true"
|
||||
enable-local-node-route: "false"
|
||||
{{- if .Values.azure.userAssignedIdentityID }}
|
||||
azure-user-assigned-identity-id: {{ .Values.azure.userAssignedIdentityID | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.flannel.enabled }}
|
||||
# Interface to be used when running Cilium on top of a CNI plugin.
|
||||
# For flannel, use "cni0"
|
||||
flannel-master-device: {{ .Values.flannel.masterDevice }}
|
||||
|
||||
# When running Cilium with policy enforcement enabled on top of a CNI plugin
|
||||
# the BPF programs will be installed on the network interface specified in
|
||||
# 'flannel-master-device' and on all network interfaces belonging to
|
||||
# a container. When the Cilium DaemonSet is removed, the BPF programs will
|
||||
# be kept in the interfaces unless this option is set to "true".
|
||||
flannel-uninstall-on-exit: "{{ .Values.flannel.uninstallOnExit}}"
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "l7Proxy" }}
|
||||
# Enables L7 proxy for L7 policy enforcement and visibility
|
||||
enable-l7-proxy: {{ .Values.l7Proxy | quote }}
|
||||
{{- end }}
|
||||
|
||||
# wait-bpf-mount makes init container wait until bpf filesystem is mounted
|
||||
wait-bpf-mount: "{{ .Values.bpf.waitForMount }}"
|
||||
|
||||
{{- if ne .Values.cni.chainingMode "none" }}
|
||||
# Enable chaining with another CNI plugin
|
||||
#
|
||||
# Supported modes:
|
||||
# - none
|
||||
# - aws-cni
|
||||
# - flannel
|
||||
# - portmap (Enables HostPort support for Cilium)
|
||||
cni-chaining-mode: {{ .Values.cni.chainingMode }}
|
||||
|
||||
{{- if hasKey .Values "enableIdentityMark" }}
|
||||
enable-identity-mark: {{ .Values.enableIdentityMark | quote }}
|
||||
{{- else if (ne $enableIdentityMark "true") }}
|
||||
enable-identity-mark: "false"
|
||||
{{- end }}
|
||||
{{- if ne .Values.cni.chainingMode "portmap" }}
|
||||
# Disable the PodCIDR route to the cilium_host interface as it is not
|
||||
# required. While chaining, it is the responsibility of the underlying plugin
|
||||
# to enable routing.
|
||||
enable-local-node-route: "false"
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
masquerade: {{ .Values.masquerade | quote }}
|
||||
{{- if hasKey .Values.bpf "masquerade" }}
|
||||
enable-bpf-masquerade: {{ .Values.bpf.masquerade | quote }}
|
||||
{{- else if eq $defaultBpfMasquerade "true" }}
|
||||
enable-bpf-masquerade: {{ $defaultBpfMasquerade | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "egressMasqueradeInterfaces" }}
|
||||
egress-masquerade-interfaces: {{ .Values.egressMasqueradeInterfaces }}
|
||||
{{- end }}
|
||||
{{- if and .Values.ipMasqAgent .Values.ipMasqAgent.enabled }}
|
||||
enable-ip-masq-agent: "true"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.encryption.enabled }}
|
||||
enable-ipsec: {{ .Values.encryption.enabled | quote }}
|
||||
ipsec-key-file: {{ .Values.encryption.mountPath }}/{{ .Values.encryption.keyFile }}
|
||||
{{- if hasKey .Values.encryption "interface" }}
|
||||
encrypt-interface: {{ .Values.encryption.interface }}
|
||||
{{- end }}
|
||||
{{- if .Values.encryption.nodeEncryption }}
|
||||
encrypt-node: {{ .Values.encryption.nodeEncryption | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "datapathMode" }}
|
||||
{{- if eq .Values.datapathMode "ipvlan" }}
|
||||
datapath-mode: ipvlan
|
||||
ipvlan-master-device: {{ .Values.ipvlan.masterDevice }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
enable-xt-socket-fallback: {{ .Values.enableXTSocketFallback | quote }}
|
||||
install-iptables-rules: {{ .Values.installIptablesRules | quote }}
|
||||
|
||||
{{- if hasKey .Values "iptablesRandomFully" }}
|
||||
iptables-random-fully: {{ .Values.iptablesRandomFully | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "iptablesLockTimeout" }}
|
||||
iptables-lock-timeout: {{ .Values.iptablesLockTimeout | quote }}
|
||||
{{- end }}
|
||||
|
||||
auto-direct-node-routes: {{ .Values.autoDirectNodeRoutes | quote }}
|
||||
enable-bandwidth-manager: {{ .Values.bandwidthManager | quote }}
|
||||
|
||||
{{- if hasKey .Values "localRedirectPolicy" }}
|
||||
enable-local-redirect-policy: {{ .Values.localRedirectPolicy | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "nativeRoutingCIDR" }}
|
||||
native-routing-cidr: {{ .Values.nativeRoutingCIDR }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "fragmentTracking" }}
|
||||
enable-ipv4-fragment-tracking: {{ .Values.fragmentTracking | quote }}
|
||||
{{- else if (ne $fragmentTracking "true") }}
|
||||
enable-ipv4-fragment-tracking: "false"
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.hostFirewall }}
|
||||
enable-host-firewall: {{ .Values.hostFirewall | quote }}
|
||||
{{- end}}
|
||||
|
||||
{{- if hasKey .Values "devices" }}
|
||||
# List of devices used to attach bpf_host.o (implements BPF NodePort,
|
||||
# host-firewall and BPF masquerading)
|
||||
devices: {{ join " " .Values.devices | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "kubeProxyReplacement" }}
|
||||
kube-proxy-replacement: {{ .Values.kubeProxyReplacement | quote }}
|
||||
{{- if ne .Values.kubeProxyReplacement "disabled" }}
|
||||
kube-proxy-replacement-healthz-bind-address: {{ default "" .Values.kubeProxyReplacementHealthzBindAddr | quote}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "hostServices" }}
|
||||
{{- if .Values.hostServices.enabled }}
|
||||
enable-host-reachable-services: {{ .Values.hostServices.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- if ne .Values.hostServices.protocols "tcp,udp" }}
|
||||
host-reachable-services-protos: {{ .Values.hostServices.protocols }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "hostPort" }}
|
||||
{{- if eq .Values.kubeProxyReplacement "partial" }}
|
||||
enable-host-port: {{ .Values.hostPort.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "externalIPs" }}
|
||||
{{- if eq .Values.kubeProxyReplacement "partial" }}
|
||||
enable-external-ips: {{ .Values.externalIPs.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "nodePort" }}
|
||||
{{- if eq .Values.kubeProxyReplacement "partial" }}
|
||||
enable-node-port: {{ .Values.nodePort.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.nodePort "range" }}
|
||||
node-port-range: {{ .Values.nodePort.range | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.nodePort "directRoutingDevice" }}
|
||||
direct-routing-device: {{ .Values.nodePort.directRoutingDevice | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.nodePort.enableHealthCheck }}
|
||||
enable-health-check-nodeport: {{ .Values.nodePort.enableHealthCheck | quote}}
|
||||
{{- end }}
|
||||
node-port-bind-protection: {{ .Values.nodePort.bindProtection | quote }}
|
||||
enable-auto-protect-node-port-range: {{ .Values.nodePort.autoProtectPortRange | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "loadBalancer" }}
|
||||
{{- if hasKey .Values.loadBalancer "mode" }}
|
||||
node-port-mode: {{ .Values.loadBalancer.mode | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.loadBalancer "algorithm" }}
|
||||
bpf-lb-algorithm: {{ .Values.loadBalancer.algorithm | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.loadBalancer "acceleration" }}
|
||||
node-port-acceleration: {{ .Values.loadBalancer.acceleration | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.maglev "tableSize" }}
|
||||
bpf-lb-maglev-table-size: {{ .Values.maglev.tableSize | quote}}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.maglev "hashSeed" }}
|
||||
bpf-lb-maglev-hash-seed: {{ .Values.maglev.hashSeed | quote}}
|
||||
{{- end }}
|
||||
{{- if .Values.sessionAffinity }}
|
||||
enable-session-affinity: {{ .Values.sessionAffinity | quote }}
|
||||
{{- else if eq $defaultSessionAffinity "true" }}
|
||||
enable-session-affinity: {{ $defaultSessionAffinity | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.svcSourceRangeCheck }}
|
||||
enable-svc-source-range-check: {{ .Values.svcSourceRangeCheck | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if and .Values.pprof .Values.pprof.enabled }}
|
||||
pprof: {{ .Values.pprof.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.logSystemLoad }}
|
||||
log-system-load: {{ .Values.logSystemLoad | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.logOptions }}
|
||||
log-opt: {{ .Values.logOptions | toJson | quote }}
|
||||
{{- end }}
|
||||
{{- if and .Values.sockops .Values.sockops.enabled }}
|
||||
sockops-enable: {{ .Values.sockops.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.k8s "requireIPv4PodCIDR" }}
|
||||
k8s-require-ipv4-pod-cidr: {{ .Values.k8s.requireIPv4PodCIDR | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.k8s "requireIPv6PodCIDR" }}
|
||||
k8s-require-ipv6-pod-cidr: {{ .Values.k8s.requireIPv6PodCIDR | quote }}
|
||||
{{- end }}
|
||||
{{- if and .Values.endpointRoutes .Values.endpointRoutes.enabled }}
|
||||
enable-endpoint-routes: {{ .Values.endpointRoutes.enabled | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.cni.configMap }}
|
||||
read-cni-conf: {{ .Values.cni.confFileMountPath }}/{{ .Values.cni.configMapKey }}
|
||||
write-cni-conf-when-ready: {{ .Values.cni.hostConfDirMountPath }}/05-cilium.conflist
|
||||
{{- else if .Values.cni.readCniConf }}
|
||||
read-cni-conf: {{ .Values.cni.readCniConf }}
|
||||
{{- end }}
|
||||
{{- if .Values.kubeConfigPath }}
|
||||
k8s-kubeconfig-path: {{ .Values.kubeConfigPath | quote }}
|
||||
{{- end }}
|
||||
{{- if and ( .Values.endpointHealthChecking.enabled ) (or (eq .Values.cni.chainingMode "portmap") (eq .Values.cni.chainingMode "none")) }}
|
||||
enable-endpoint-health-checking: "true"
|
||||
{{- else}}
|
||||
# Disable health checking, when chaining mode is not set to portmap or none
|
||||
enable-endpoint-health-checking: "false"
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "healthChecking" }}
|
||||
enable-health-checking: {{ .Values.healthChecking | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.etcd.managed }}
|
||||
enable-well-known-identities: "true"
|
||||
{{- else }}
|
||||
enable-well-known-identities: "false"
|
||||
{{- end }}
|
||||
enable-remote-node-identity: {{ .Values.remoteNodeIdentity | quote }}
|
||||
|
||||
{{- if hasKey .Values "synchronizeK8sNodes" }}
|
||||
synchronize-k8s-nodes: {{ .Values.synchronizeK8sNodes | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "policyAuditMode" }}
|
||||
policy-audit-mode: {{ .Values.policyAuditMode | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if ne $defaultOperatorApiServeAddr "localhost:9234" }}
|
||||
operator-api-serve-addr: {{ $defaultOperatorApiServeAddr | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.hubble.enabled }}
|
||||
# Enable Hubble gRPC service.
|
||||
enable-hubble: {{ .Values.hubble.enabled | quote }}
|
||||
# UNIX domain socket for Hubble server to listen to.
|
||||
hubble-socket-path: {{ .Values.hubble.socketPath | quote }}
|
||||
{{- if hasKey .Values.hubble "eventQueueSize" }}
|
||||
# Buffer size of the channel for Hubble to receive monitor events. If this field is not set,
|
||||
# the buffer size is set to the default monitor queue size.
|
||||
hubble-event-queue-size: {{ .Values.hubble.eventQueueSize | quote }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.hubble "flowBufferSize" }}
|
||||
# Size of the buffer to store recent flows.
|
||||
hubble-flow-buffer-size: {{ .Values.hubble.flowBufferSize | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.hubble.metrics.enabled }}
|
||||
# Address to expose Hubble metrics (e.g. ":7070"). Metrics server will be disabled if this
|
||||
# field is not set.
|
||||
hubble-metrics-server: ":{{ .Values.hubble.metrics.port }}"
|
||||
# A space separated list of metrics to enable. See [0] for available metrics.
|
||||
#
|
||||
# https://github.com/cilium/hubble/blob/master/Documentation/metrics.md
|
||||
hubble-metrics: {{- range .Values.hubble.metrics.enabled }}
|
||||
{{.}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values.hubble "listenAddress" }}
|
||||
# An additional address for Hubble server to listen to (e.g. ":4244").
|
||||
hubble-listen-address: {{ .Values.hubble.listenAddress | quote }}
|
||||
{{- if .Values.hubble.tls.enabled }}
|
||||
hubble-disable-tls: "false"
|
||||
hubble-tls-cert-file: /var/lib/cilium/tls/hubble/server.crt
|
||||
hubble-tls-key-file: /var/lib/cilium/tls/hubble/server.key
|
||||
hubble-tls-client-ca-files: /var/lib/cilium/tls/hubble/client-ca.crt
|
||||
{{- else }}
|
||||
hubble-disable-tls: "true"
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if hasKey .Values "disableIptablesFeederRules" }}
|
||||
# A space separated list of iptables chains to disable when installing feeder rules.
|
||||
disable-iptables-feeder-rules: {{ .Values.disableIptablesFeederRules | join " " | quote }}
|
||||
{{- end }}
|
||||
ipam: {{ $ipam | quote }}
|
||||
|
||||
{{- if eq $ipam "cluster-pool" }}
|
||||
{{- if .Values.ipv4.enabled }}
|
||||
cluster-pool-ipv4-cidr: {{ .Values.ipam.operator.clusterPoolIPv4PodCIDR | quote }}
|
||||
cluster-pool-ipv4-mask-size: {{ .Values.ipam.operator.clusterPoolIPv4MaskSize | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.ipv6.enabled }}
|
||||
cluster-pool-ipv6-cidr: {{ .Values.ipam.operator.clusterPoolIPv6PodCIDR | quote }}
|
||||
cluster-pool-ipv6-mask-size: {{ .Values.ipam.operator.clusterPoolIPv6MaskSize | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.enableCnpStatusUpdates }}
|
||||
disable-cnp-status-updates: {{ (not .Values.enableCnpStatusUpdates) | quote }}
|
||||
{{- else if (eq $defaultEnableCnpStatusUpdates "false") }}
|
||||
disable-cnp-status-updates: "true"
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values "crdWaitTimeout" }}
|
||||
crd-wait-timeout: {{ .Values.crdWaitTimeout | quote }}
|
||||
{{- else if ( ne $crdWaitTimeout "5m" ) }}
|
||||
crd-wait-timeout: {{ $crdWaitTimeout | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.enableK8sEndpointSlice }}
|
||||
enable-k8s-endpoint-slice: {{ .Values.enableK8sEndpointSlice | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if hasKey .Values.k8s "serviceProxyName" }}
|
||||
# Configure service proxy name for Cilium.
|
||||
k8s-service-proxy-name: {{ .Values.k8s.serviceProxyName | quote }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.extraConfig }}
|
||||
{{ toYaml .Values.extraConfig | indent 2 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,73 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: cilium-etcd-operator
|
||||
rules:
|
||||
- apiGroups:
|
||||
- etcd.database.coreos.com
|
||||
resources:
|
||||
- etcdclusters
|
||||
verbs:
|
||||
- get
|
||||
- delete
|
||||
- create
|
||||
- update
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
- delete
|
||||
- get
|
||||
- create
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- delete
|
||||
- create
|
||||
- get
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pods
|
||||
verbs:
|
||||
- list
|
||||
- get
|
||||
- delete
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- delete
|
||||
- create
|
||||
- get
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- componentstatuses
|
||||
verbs:
|
||||
- get
|
||||
- apiGroups:
|
||||
- extensions
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- delete
|
||||
- create
|
||||
- get
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- get
|
||||
- create
|
||||
- delete
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: cilium-etcd-operator
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: cilium-etcd-operator
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: cilium-etcd-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,86 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
labels:
|
||||
io.cilium/app: etcd-operator
|
||||
name: cilium-etcd-operator
|
||||
name: cilium-etcd-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
replicas: 1
|
||||
selector:
|
||||
matchLabels:
|
||||
io.cilium/app: etcd-operator
|
||||
name: cilium-etcd-operator
|
||||
{{- with .Values.etcd.updateStrategy }}
|
||||
strategy:
|
||||
{{- toYaml . | trim | nindent 4 }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- with .Values.etcd.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
io.cilium/app: etcd-operator
|
||||
name: cilium-etcd-operator
|
||||
spec:
|
||||
{{- if .Values.etcd.affinity }}
|
||||
affinity:
|
||||
{{ toYaml .Values.etcd.affinity | indent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 8 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- args:
|
||||
#- --etcd-node-selector=disktype=ssd,cputype=high
|
||||
command:
|
||||
- /usr/bin/cilium-etcd-operator
|
||||
env:
|
||||
- name: CILIUM_ETCD_OPERATOR_CLUSTER_DOMAIN
|
||||
value: "{{ .Values.etcd.clusterDomain }}"
|
||||
- name: CILIUM_ETCD_OPERATOR_ETCD_CLUSTER_SIZE
|
||||
value: "{{ .Values.etcd.clusterSize }}"
|
||||
- name: CILIUM_ETCD_OPERATOR_NAMESPACE
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
- name: CILIUM_ETCD_OPERATOR_POD_NAME
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.name
|
||||
- name: CILIUM_ETCD_OPERATOR_POD_UID
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.uid
|
||||
- name: CILIUM_ETCD_META_ETCD_AUTO_COMPACTION_MODE
|
||||
value: "revision"
|
||||
- name: CILIUM_ETCD_META_ETCD_AUTO_COMPACTION_RETENTION
|
||||
value: "25000"
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.etcd.image.repository }}:{{ .Values.etcd.image.tag }}
|
||||
imagePullPolicy: {{ .Values.etcd.image.pullPolicy }}
|
||||
name: cilium-etcd-operator
|
||||
dnsPolicy: ClusterFirst
|
||||
hostNetwork: true
|
||||
{{- if and (or (and (eq .Release.Namespace "kube-system") (gt .Capabilities.KubeVersion.Minor "10")) (ge .Capabilities.KubeVersion.Minor "17") (gt .Capabilities.KubeVersion.Major "1")) .Values.enableCriticalPriorityClass }}
|
||||
priorityClassName: system-cluster-critical
|
||||
{{- end }}
|
||||
restartPolicy: Always
|
||||
serviceAccount: cilium-etcd-operator
|
||||
serviceAccountName: cilium-etcd-operator
|
||||
{{- with .Values.etcd.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | trim | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
{{- if .Values.serviceAccounts.etcd.create }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: cilium-etcd-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccounts.etcd.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccounts.etcd.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,269 @@
|
|||
{{- if .Values.nodeinit.enabled }}
|
||||
kind: DaemonSet
|
||||
apiVersion: apps/v1
|
||||
metadata:
|
||||
name: cilium-node-init
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
app: cilium-node-init
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
app: cilium-node-init
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
{{- with .Values.nodeinit.podAnnotations }}
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
app: cilium-node-init
|
||||
spec:
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
hostPID: true
|
||||
hostNetwork: true
|
||||
{{- if and (or (and (eq .Release.Namespace "kube-system") (gt .Capabilities.KubeVersion.Minor "10")) (ge .Capabilities.KubeVersion.Minor "17") (gt .Capabilities.KubeVersion.Major "1")) .Values.enableCriticalPriorityClass }}
|
||||
priorityClassName: system-node-critical
|
||||
{{- end }}
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- name: node-init
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.nodeinit.image.repository }}:{{ .Values.nodeinit.image.tag }}
|
||||
imagePullPolicy: {{ .Values.nodeinit.image.pullPolicy }}
|
||||
securityContext:
|
||||
privileged: true
|
||||
{{- if .Values.nodeinit.revertReconfigureKubelet }}
|
||||
lifecycle:
|
||||
preStop:
|
||||
exec:
|
||||
command:
|
||||
- "nsenter"
|
||||
- "-t"
|
||||
- "1"
|
||||
- "-m"
|
||||
- "--"
|
||||
- "/bin/sh"
|
||||
- "-c"
|
||||
- |
|
||||
#!/bin/bash
|
||||
|
||||
set -o errexit
|
||||
set -o pipefail
|
||||
set -o nounset
|
||||
|
||||
if stat /tmp/node-deinit.cilium.io > /dev/null 2>&1; then
|
||||
exit 0
|
||||
fi
|
||||
|
||||
echo "Waiting on pods to stop..."
|
||||
if [ ! -f /etc/crictl.yaml ] || grep -q 'docker' /etc/crictl.yaml; then
|
||||
# Works for COS, ubuntu
|
||||
while docker ps | grep -v "node-init" | grep -q "POD_cilium"; do sleep 1; done
|
||||
else
|
||||
# COS-beta (with containerd)
|
||||
while crictl ps | grep -v "node-init" | grep -q "POD_cilium"; do sleep 1; done
|
||||
fi
|
||||
|
||||
systemctl disable sys-fs-bpf.mount || true
|
||||
systemctl stop sys-fs-bpf.mount || true
|
||||
|
||||
if ip link show cilium_host; then
|
||||
echo "Deleting cilium_host interface..."
|
||||
ip link del cilium_host
|
||||
fi
|
||||
|
||||
{{- if not (eq .Values.nodeinit.bootstrapFile "") }}
|
||||
rm -f {{ .Values.nodeinit.bootstrapFile }}
|
||||
{{- end }}
|
||||
|
||||
rm -f /tmp/node-init.cilium.io
|
||||
touch /tmp/node-deinit.cilium.io
|
||||
|
||||
{{- if .Values.nodeinit.reconfigureKubelet }}
|
||||
echo "Changing kubelet configuration to --network-plugin=kubenet"
|
||||
sed -i "s:--network-plugin=cni\ --cni-bin-dir={{ .Values.cni.binPath }}:--network-plugin=kubenet:g" /etc/default/kubelet
|
||||
echo "Restarting kubelet..."
|
||||
systemctl restart kubelet
|
||||
{{- end }}
|
||||
|
||||
{{- if (and .Values.gke.enabled (or .Values.masquerade .Values.gke.disableDefaultSnat))}}
|
||||
# If the IP-MASQ chain exists, add back default jump rule from the GKE instance configure script
|
||||
if iptables -w -t nat -L IP-MASQ > /dev/null; then
|
||||
iptables -w -t nat -A POSTROUTING -m comment --comment "ip-masq: ensure nat POSTROUTING directs all non-LOCAL destination traffic to our custom IP-MASQ chain" -m addrtype ! --dst-type LOCAL -j IP-MASQ
|
||||
fi
|
||||
{{- end }}
|
||||
|
||||
echo "Node de-initialization complete"
|
||||
{{- end }}
|
||||
env:
|
||||
- name: CHECKPOINT_PATH
|
||||
value: /tmp/node-init.cilium.io
|
||||
# STARTUP_SCRIPT is the script run on node bootstrap. Node
|
||||
# bootstrapping can be customized in this script. This script is invoked
|
||||
# using nsenter, so it runs in the host's network and mount namespace using
|
||||
# the host's userland tools!
|
||||
- name: STARTUP_SCRIPT
|
||||
value: |
|
||||
#!/bin/bash
|
||||
|
||||
set -o errexit
|
||||
set -o pipefail
|
||||
set -o nounset
|
||||
|
||||
mount | grep "/sys/fs/bpf type bpf" || {
|
||||
# Mount the filesystem until next reboot
|
||||
echo "Mounting BPF filesystem..."
|
||||
mount bpffs /sys/fs/bpf -t bpf
|
||||
|
||||
# Configure systemd to mount after next boot
|
||||
echo "Installing BPF filesystem mount"
|
||||
cat >/tmp/sys-fs-bpf.mount <<EOF
|
||||
[Unit]
|
||||
Description=Mount BPF filesystem (Cilium)
|
||||
Documentation=http://docs.cilium.io/
|
||||
DefaultDependencies=no
|
||||
Before=local-fs.target umount.target
|
||||
After=swap.target
|
||||
|
||||
[Mount]
|
||||
What=bpffs
|
||||
Where=/sys/fs/bpf
|
||||
Type=bpf
|
||||
Options=rw,nosuid,nodev,noexec,relatime,mode=700
|
||||
|
||||
[Install]
|
||||
WantedBy=multi-user.target
|
||||
EOF
|
||||
|
||||
if [ -d "/etc/systemd/system/" ]; then
|
||||
mv /tmp/sys-fs-bpf.mount /etc/systemd/system/
|
||||
echo "Installed sys-fs-bpf.mount to /etc/systemd/system/"
|
||||
elif [ -d "/lib/systemd/system/" ]; then
|
||||
mv /tmp/sys-fs-bpf.mount /lib/systemd/system/
|
||||
echo "Installed sys-fs-bpf.mount to /lib/systemd/system/"
|
||||
fi
|
||||
|
||||
# Ensure that filesystem gets mounted on next reboot
|
||||
systemctl enable sys-fs-bpf.mount
|
||||
systemctl start sys-fs-bpf.mount
|
||||
}
|
||||
|
||||
echo "Link information:"
|
||||
ip link
|
||||
|
||||
echo "Routing table:"
|
||||
ip route
|
||||
|
||||
echo "Addressing:"
|
||||
ip -4 a
|
||||
ip -6 a
|
||||
|
||||
{{- if .Values.nodeinit.removeCbrBridge }}
|
||||
if ip link show cbr0; then
|
||||
echo "Detected cbr0 bridge. Deleting interface..."
|
||||
ip link del cbr0
|
||||
fi
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.nodeinit.reconfigureKubelet }}
|
||||
# GKE: Alter the kubelet configuration to run in CNI mode
|
||||
echo "Changing kubelet configuration to --network-plugin=cni --cni-bin-dir={{ .Values.cni.binPath }}"
|
||||
mkdir -p {{ .Values.cni.binPath }}
|
||||
sed -i "s:--network-plugin=kubenet:--network-plugin=cni\ --cni-bin-dir={{ .Values.cni.binPath }}:g" /etc/default/kubelet
|
||||
echo "Restarting kubelet..."
|
||||
systemctl restart kubelet
|
||||
{{- end }}
|
||||
|
||||
{{- if (and .Values.gke.enabled (or .Values.masquerade .Values.gke.disableDefaultSnat))}}
|
||||
# If Cilium is configured to manage masquerading of traffic leaving the node,
|
||||
# we need to disable the IP-MASQ chain because even if ip-masq-agent
|
||||
# is not installed, the node init script installs some default rules into
|
||||
# the IP-MASQ chain.
|
||||
# If we remove the jump to that ip-masq chain, then we ensure the ip masquerade
|
||||
# configuration is solely managed by Cilium.
|
||||
# Also, if Cilium is installed, it may be expected that it would be solely responsible
|
||||
# for the networking configuration on that node. So provide the same functionality
|
||||
# as the --disable-snat-flag for existing GKE clusters.
|
||||
iptables -w -t nat -D POSTROUTING -m comment --comment "ip-masq: ensure nat POSTROUTING directs all non-LOCAL destination traffic to our custom IP-MASQ chain" -m addrtype ! --dst-type LOCAL -j IP-MASQ || true
|
||||
{{- end }}
|
||||
|
||||
{{- if not (eq .Values.nodeinit.bootstrapFile "") }}
|
||||
date > {{ .Values.nodeinit.bootstrapFile }}
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.nodeinit.restartPods }}
|
||||
echo "Restarting kubenet managed pods"
|
||||
if [ ! -f /etc/crictl.yaml ] || grep -q 'docker' /etc/crictl.yaml; then
|
||||
# Works for COS, ubuntu
|
||||
# Note the first line is the containerID with a trailing \r
|
||||
for f in `find /var/lib/cni/networks/ -type f ! -name lock ! -name last_reserved_ip.0`; do docker rm -f "$(sed 's/\r//;1q' $f)" || true; done
|
||||
elif [ -n "$(docker ps --format '{{ "{{" }}.Image{{ "}}" }}' | grep ^[0-9]*\.dkr\.ecr\.[a-z]*-[a-z]*-[0-9]*\.amazonaws\.com/amazon-k8s-cni)" ]; then
|
||||
timeout=1
|
||||
for i in $(seq 1 7); do
|
||||
echo "Checking introspection API"
|
||||
curl localhost:61679 && retry=false || retry=true
|
||||
if [ $retry == false ]; then break ; fi
|
||||
sleep "$timeout"
|
||||
timeout=$(($timeout * 2))
|
||||
done
|
||||
|
||||
for pod in $(curl "localhost:61679/v1/pods" 2> /dev/null | jq -r '. | keys[]'); do
|
||||
container_id=$(echo "$pod" | awk -F_ ' { print $3 } ' | cut -c1-12)
|
||||
echo "Restarting ${container_id}"
|
||||
docker kill "${container_id}" || true
|
||||
done
|
||||
else
|
||||
# COS-beta (with containerd)
|
||||
for f in `find /var/lib/cni/networks/ -type f ! -name lock ! -name last_reserved_ip.0`; do crictl stopp $(cat $f) || true; done
|
||||
fi
|
||||
{{- end }}
|
||||
|
||||
# AKS: If azure-vnet is installed on the node, and (still) configured in bridge mode,
|
||||
# configure it as 'transparent' to be consistent with Cilium's CNI chaining config.
|
||||
# If the azure-vnet CNI config is not removed, kubelet will execute CNI CHECK commands
|
||||
# against it every 5 seconds and write 'bridge' to its state file, causing inconsistent
|
||||
# behaviour when Pods are removed.
|
||||
if [ -f /etc/cni/net.d/10-azure.conflist ]; then
|
||||
echo "Ensuring azure-vnet is configured in 'transparent' mode..."
|
||||
sed -i 's/"mode":\s*"bridge"/"mode":"transparent"/g' /etc/cni/net.d/10-azure.conflist
|
||||
fi
|
||||
|
||||
{{- if .Values.azure.enabled }}
|
||||
# The azure0 interface being present means the node was booted with azure-vnet configured
|
||||
# in bridge mode. This means there might be ebtables rules and neight entries interfering
|
||||
# with pod connectivity if we deploy with Azure IPAM.
|
||||
if ip l show dev azure0 >/dev/null 2>&1; then
|
||||
|
||||
# In Azure IPAM mode, also remove the azure-vnet state file, otherwise ebtables rules get
|
||||
# restored by the azure-vnet CNI plugin on every CNI CHECK, which can cause connectivity
|
||||
# issues in Cilium-managed Pods. Since azure-vnet is no longer called on scheduling events,
|
||||
# this file can be removed.
|
||||
rm -f /var/run/azure-vnet.json
|
||||
|
||||
# This breaks connectivity for existing workload Pods when Cilium is scheduled, but we need
|
||||
# to flush these to prevent Cilium-managed Pod IPs conflicting with Pod IPs previously allocated
|
||||
# by azure-vnet. These ebtables DNAT rules contain fixed MACs that are no longer bound on the node,
|
||||
# causing packets for these Pods to be redirected back out to the gateway, where they are dropped.
|
||||
echo 'Flushing ebtables pre/postrouting rules in nat table.. (disconnecting non-Cilium Pods!)'
|
||||
ebtables -t nat -F PREROUTING || true
|
||||
ebtables -t nat -F POSTROUTING || true
|
||||
|
||||
# ip-masq-agent periodically injects PERM neigh entries towards the gateway
|
||||
# for all other k8s nodes in the cluster. These are safe to flush, as ARP can
|
||||
# resolve these nodes as usual. PERM entries will be automatically restored later.
|
||||
echo 'Deleting all permanent neighbour entries on azure0...'
|
||||
ip neigh show dev azure0 nud permanent | cut -d' ' -f1 | xargs -r -n1 ip neigh del dev azure0 to || true
|
||||
fi
|
||||
{{- end }}
|
||||
|
||||
{{- if .Values.nodeinit.revertReconfigureKubelet }}
|
||||
rm -f /tmp/node-deinit.cilium.io
|
||||
{{- end }}
|
||||
echo "Node initialization complete"
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,90 @@
|
|||
{{- if .Values.operator.enabled }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: cilium-operator
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
# to automatically delete [core|kube]dns pods so that are starting to being
|
||||
# managed by Cilium
|
||||
- pods
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- delete
|
||||
- apiGroups:
|
||||
- discovery.k8s.io
|
||||
resources:
|
||||
- endpointslices
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
# to perform the translation of a CNP that contains `ToGroup` to its endpoints
|
||||
- services
|
||||
- endpoints
|
||||
# to check apiserver connectivity
|
||||
- namespaces
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- cilium.io
|
||||
resources:
|
||||
- ciliumnetworkpolicies
|
||||
- ciliumnetworkpolicies/status
|
||||
- ciliumnetworkpolicies/finalizers
|
||||
- ciliumclusterwidenetworkpolicies
|
||||
- ciliumclusterwidenetworkpolicies/status
|
||||
- ciliumclusterwidenetworkpolicies/finalizers
|
||||
- ciliumendpoints
|
||||
- ciliumendpoints/status
|
||||
- ciliumendpoints/finalizers
|
||||
- ciliumnodes
|
||||
- ciliumnodes/status
|
||||
- ciliumnodes/finalizers
|
||||
- ciliumidentities
|
||||
- ciliumidentities/status
|
||||
- ciliumidentities/finalizers
|
||||
- ciliumlocalredirectpolicies
|
||||
- ciliumlocalredirectpolicies/status
|
||||
- ciliumlocalredirectpolicies/finalizers
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- watch
|
||||
# For cilium-operator running in HA mode.
|
||||
#
|
||||
# Cilium operator running in HA mode requires the use of ResourceLock for Leader Election
|
||||
# between mulitple running instances.
|
||||
# The preferred way of doing this is to use LeasesResourceLock as edits to Leases are less
|
||||
# common and fewer objects in the cluster watch "all Leases".
|
||||
# The support for leases was introduced in coordination.k8s.io/v1 during Kubernetes 1.14 release.
|
||||
# In Cilium we currently don't support HA mode for K8s version < 1.14. This condition make sure
|
||||
# that we only authorize access to leases resources in supported K8s versions.
|
||||
{{- if or (ge .Capabilities.KubeVersion.Minor "14") (gt .Capabilities.KubeVersion.Major "1") }}
|
||||
- apiGroups:
|
||||
- coordination.k8s.io
|
||||
resources:
|
||||
- leases
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- update
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if .Values.operator.enabled }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: cilium-operator
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: cilium-operator
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: cilium-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,255 @@
|
|||
{{- if .Values.operator.enabled }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
labels:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
name: cilium-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
# We support HA mode only for Kubernetes version > 1.14
|
||||
# See docs on ServerCapabilities.LeasesResourceLock in file pkg/k8s/version/version.go
|
||||
# for more details.
|
||||
{{- if or (ge .Capabilities.KubeVersion.Minor "14") (gt .Capabilities.KubeVersion.Major "1") }}
|
||||
replicas: {{ .Values.operator.replicas }}
|
||||
{{- else }}
|
||||
replicas: 1
|
||||
{{- end }}
|
||||
selector:
|
||||
matchLabels:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
{{- with .Values.operator.updateStrategy }}
|
||||
strategy:
|
||||
{{- toYaml . | trim | nindent 4 }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
{{- if .Values.operator.rollOutPods }}
|
||||
# ensure pods roll when configmap updates
|
||||
cilium.io/cilium-configmap-checksum: {{ include (print $.Template.BasePath "/cilium-configmap.yaml") . | sha256sum | quote }}
|
||||
{{- end }}
|
||||
{{- if and .Values.operator.prometheus.enabled (not .Values.operator.prometheus.serviceMonitor.enabled) }}
|
||||
prometheus.io/port: {{ .Values.operator.prometheus.port | quote }}
|
||||
prometheus.io/scrape: "true"
|
||||
{{- end }}
|
||||
{{- with .Values.operator.podAnnotations }}
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
spec:
|
||||
{{- if or (ge .Capabilities.KubeVersion.Minor "14") (gt .Capabilities.KubeVersion.Major "1") }}
|
||||
# In HA mode, cilium-operator pods must not be scheduled on the same
|
||||
# node as they will clash with each other.
|
||||
{{- if .Values.operator.affinity }}
|
||||
affinity:
|
||||
{{- toYaml .Values.operator.affinity | trim | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- args:
|
||||
- --config-dir=/tmp/cilium/config-map
|
||||
- --debug=$(CILIUM_DEBUG)
|
||||
command:
|
||||
{{- if .Values.eni }}
|
||||
- cilium-operator-aws
|
||||
{{- else if .Values.azure.enabled }}
|
||||
- cilium-operator-azure
|
||||
{{- else }}
|
||||
- cilium-operator-generic
|
||||
{{- end }}
|
||||
env:
|
||||
- name: K8S_NODE_NAME
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: spec.nodeName
|
||||
- name: CILIUM_K8S_NAMESPACE
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
apiVersion: v1
|
||||
fieldPath: metadata.namespace
|
||||
- name: CILIUM_DEBUG
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: debug
|
||||
name: cilium-config
|
||||
optional: true
|
||||
{{- if .Values.eni }}
|
||||
- name: AWS_ACCESS_KEY_ID
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
key: AWS_ACCESS_KEY_ID
|
||||
name: cilium-aws
|
||||
optional: true
|
||||
- name: AWS_SECRET_ACCESS_KEY
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
key: AWS_SECRET_ACCESS_KEY
|
||||
name: cilium-aws
|
||||
optional: true
|
||||
- name: AWS_DEFAULT_REGION
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
key: AWS_DEFAULT_REGION
|
||||
name: cilium-aws
|
||||
optional: true
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServiceHost }}
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: {{ .Values.k8sServiceHost | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServicePort }}
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: {{ .Values.k8sServicePort | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.azure.subscriptionID }}
|
||||
- name: AZURE_SUBSCRIPTION_ID
|
||||
value: {{ .Values.azure.subscriptionID }}
|
||||
{{- end }}
|
||||
{{- if .Values.azure.tenantID }}
|
||||
- name: AZURE_TENANT_ID
|
||||
value: {{ .Values.azure.tenantID }}
|
||||
{{- end }}
|
||||
{{- if .Values.azure.resourceGroup }}
|
||||
- name: AZURE_RESOURCE_GROUP
|
||||
value: {{ .Values.azure.resourceGroup }}
|
||||
{{- end }}
|
||||
{{- if .Values.azure.clientID }}
|
||||
- name: AZURE_CLIENT_ID
|
||||
value: {{ .Values.azure.clientID }}
|
||||
{{- end }}
|
||||
{{- if .Values.azure.clientSecret }}
|
||||
- name: AZURE_CLIENT_SECRET
|
||||
value: {{ .Values.azure.clientSecret }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.operator.extraEnv }}
|
||||
- name: {{ $key }}
|
||||
value: {{ $value }}
|
||||
{{- end }}
|
||||
{{- if .Values.eni }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.operator.image.repository }}-aws:{{ .Values.operator.image.tag }}
|
||||
{{- else if .Values.azure.enabled }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.operator.image.repository }}-azure:{{ .Values.operator.image.tag }}
|
||||
{{- else }}
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.operator.image.repository }}-generic:{{ .Values.operator.image.tag }}
|
||||
{{- end }}
|
||||
imagePullPolicy: {{ .Values.operator.image.pullPolicy }}
|
||||
name: cilium-operator
|
||||
{{- if .Values.operator.prometheus.enabled }}
|
||||
ports:
|
||||
- containerPort: {{ .Values.operator.prometheus.port }}
|
||||
hostPort: {{ .Values.operator.prometheus.port }}
|
||||
name: prometheus
|
||||
protocol: TCP
|
||||
{{- end }}
|
||||
livenessProbe:
|
||||
httpGet:
|
||||
{{- if .Values.ipv4.enabled }}
|
||||
host: '127.0.0.1'
|
||||
{{- else }}
|
||||
host: '::1'
|
||||
{{- end }}
|
||||
path: /healthz
|
||||
port: 9234
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 60
|
||||
periodSeconds: 10
|
||||
timeoutSeconds: 3
|
||||
volumeMounts:
|
||||
- mountPath: /tmp/cilium/config-map
|
||||
name: cilium-config-path
|
||||
readOnly: true
|
||||
{{- if .Values.etcd.enabled }}
|
||||
- mountPath: /var/lib/etcd-config
|
||||
name: etcd-config-path
|
||||
readOnly: true
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- mountPath: /var/lib/etcd-secrets
|
||||
name: etcd-secrets
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.kubeConfigPath }}
|
||||
- mountPath: {{ .Values.kubeConfigPath }}
|
||||
name: kube-config
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- range .Values.operator.extraHostPathMounts }}
|
||||
- mountPath: {{ .mountPath }}
|
||||
name: {{ .name }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- if .mountPropagation }}
|
||||
mountPropagation: {{ .mountPropagation }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.operator.resources }}
|
||||
resources:
|
||||
{{- toYaml .Values.operator.resources | trim | nindent 10 }}
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
{{- if (and .Values.etcd.managed (not .Values.etcd.k8sService)) }}
|
||||
# In managed etcd mode, Cilium must be able to resolve the DNS name of
|
||||
# the etcd service
|
||||
dnsPolicy: ClusterFirstWithHostNet
|
||||
{{- end }}
|
||||
restartPolicy: Always
|
||||
{{- if and (or (and (eq .Release.Namespace "kube-system") (gt .Capabilities.KubeVersion.Minor "10")) (ge .Capabilities.KubeVersion.Minor "17") (gt .Capabilities.KubeVersion.Major "1")) .Values.enableCriticalPriorityClass }}
|
||||
priorityClassName: system-cluster-critical
|
||||
{{- end }}
|
||||
serviceAccount: cilium-operator
|
||||
serviceAccountName: cilium-operator
|
||||
{{- with .Values.operator.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | trim | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
volumes:
|
||||
# To read the configuration from the config map
|
||||
- configMap:
|
||||
name: cilium-config
|
||||
name: cilium-config-path
|
||||
{{- if .Values.etcd.enabled }}
|
||||
# To read the etcd config stored in config maps
|
||||
- configMap:
|
||||
defaultMode: 420
|
||||
items:
|
||||
- key: etcd-config
|
||||
path: etcd.config
|
||||
name: cilium-config
|
||||
name: etcd-config-path
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
# To read the k8s etcd secrets in case the user might want to use TLS
|
||||
- name: etcd-secrets
|
||||
secret:
|
||||
defaultMode: 420
|
||||
optional: true
|
||||
secretName: cilium-etcd-secrets
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.kubeConfigPath }}
|
||||
- hostPath:
|
||||
path: {{ .Values.kubeConfigPath }}
|
||||
type: FileOrCreate
|
||||
name: kube-config
|
||||
{{- end }}
|
||||
{{- range .Values.operator.extraHostPathMounts }}
|
||||
- name: {{ .name }}
|
||||
hostPath:
|
||||
path: {{ .hostPath }}
|
||||
{{- if .hostPathType }}
|
||||
type: {{ .hostPathType }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,21 @@
|
|||
{{- if and (.Values.operator.enabled) (.Values.operator.prometheus.enabled) (.Values.operator.prometheus.serviceMonitor.enabled) }}
|
||||
kind: Service
|
||||
apiVersion: v1
|
||||
metadata:
|
||||
name: cilium-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
spec:
|
||||
clusterIP: None
|
||||
type: ClusterIP
|
||||
ports:
|
||||
- name: metrics
|
||||
port: 6942
|
||||
protocol: TCP
|
||||
targetPort: prometheus
|
||||
selector:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
{{- if .Values.operator.enabled }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: cilium-operator
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccounts.operator.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccounts.operator.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,26 @@
|
|||
{{- if and (.Values.operator.enabled) (.Values.operator.prometheus.enabled) (.Values.operator.prometheus.serviceMonitor.enabled) }}
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: cilium-operator
|
||||
{{- if .Values.operator.prometheus.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.operator.prometheus.serviceMonitor.namespace }}
|
||||
{{- else }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
io.cilium/app: operator
|
||||
name: cilium-operator
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
endpoints:
|
||||
- port: metrics
|
||||
interval: 10s
|
||||
honorLabels: true
|
||||
path: /metrics
|
||||
targetLabels:
|
||||
- io.cilium/app
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,109 @@
|
|||
{{- if .Values.preflight.enabled }}
|
||||
{{- /*
|
||||
Keep file in synced with cilium-agent-clusterrole.yaml
|
||||
*/ -}}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: cilium-pre-flight
|
||||
rules:
|
||||
- apiGroups:
|
||||
- networking.k8s.io
|
||||
resources:
|
||||
- networkpolicies
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- discovery.k8s.io
|
||||
resources:
|
||||
- endpointslices
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- namespaces
|
||||
- services
|
||||
- nodes
|
||||
- endpoints
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pods
|
||||
- pods/finalizers
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
- delete
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- nodes
|
||||
- nodes/status
|
||||
verbs:
|
||||
- patch
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
# Deprecated for removal in v1.10
|
||||
- create
|
||||
- list
|
||||
- watch
|
||||
- update
|
||||
|
||||
# This is used when validating policies in preflight. This will need to stay
|
||||
# until we figure out how to avoid "get" inside the preflight, and then
|
||||
# should be removed ideally.
|
||||
- get
|
||||
{{- if eq "k8s" .Values.tls.secretsBackend }}
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- get
|
||||
{{- end }}
|
||||
- apiGroups:
|
||||
- cilium.io
|
||||
resources:
|
||||
- ciliumnetworkpolicies
|
||||
- ciliumnetworkpolicies/status
|
||||
- ciliumnetworkpolicies/finalizers
|
||||
- ciliumclusterwidenetworkpolicies
|
||||
- ciliumclusterwidenetworkpolicies/status
|
||||
- ciliumclusterwidenetworkpolicies/finalizers
|
||||
- ciliumendpoints
|
||||
- ciliumendpoints/status
|
||||
- ciliumendpoints/finalizers
|
||||
- ciliumnodes
|
||||
- ciliumnodes/status
|
||||
- ciliumnodes/finalizers
|
||||
- ciliumidentities
|
||||
- ciliumidentities/finalizers
|
||||
- ciliumlocalredirectpolicies
|
||||
- ciliumlocalredirectpolicies/status
|
||||
- ciliumlocalredirectpolicies/finalizers
|
||||
verbs:
|
||||
- '*'
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if .Values.preflight.enabled }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: cilium-pre-flight
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: cilium-pre-flight
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: cilium-pre-flight
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,158 @@
|
|||
{{- if .Values.preflight.enabled }}
|
||||
apiVersion: apps/v1
|
||||
kind: DaemonSet
|
||||
metadata:
|
||||
name: cilium-pre-flight-check
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: cilium-pre-flight-check
|
||||
kubernetes.io/cluster-service: "true"
|
||||
template:
|
||||
metadata:
|
||||
{{- with .Values.preflight.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
k8s-app: cilium-pre-flight-check
|
||||
kubernetes.io/cluster-service: "true"
|
||||
spec:
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 6 }}
|
||||
{{- end }}
|
||||
initContainers:
|
||||
- name: clean-cilium-state
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.preflight.image.repository }}:{{ .Values.preflight.image.tag }}
|
||||
imagePullPolicy: {{ .Values.preflight.image.pullPolicy }}
|
||||
command: ["/bin/echo"]
|
||||
args:
|
||||
- "hello"
|
||||
containers:
|
||||
- name: cilium-pre-flight-check
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.preflight.image.repository }}:{{ .Values.preflight.image.tag }}
|
||||
imagePullPolicy: {{ .Values.preflight.image.pullPolicy }}
|
||||
command: ["/bin/sh"]
|
||||
args:
|
||||
- -c
|
||||
- "touch /tmp/ready; sleep 1h"
|
||||
livenessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/ready
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
readinessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/ready
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
volumeMounts:
|
||||
- mountPath: /var/run/cilium
|
||||
name: cilium-run
|
||||
{{- if .Values.etcd.enabled }}
|
||||
- mountPath: /var/lib/etcd-config
|
||||
name: etcd-config-path
|
||||
readOnly: true
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- mountPath: /var/lib/etcd-secrets
|
||||
name: etcd-secrets
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
{{- if ne .Values.preflight.tofqdnsPreCache "" }}
|
||||
- name: cilium-pre-flight-fqdn-precache
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.preflight.image.repository }}:{{ .Values.preflight.image.tag }}
|
||||
imagePullPolicy: {{ .Values.preflight.image.pullPolicy }}
|
||||
name: cilium-pre-flight-fqdn-precache
|
||||
command: ["/bin/sh"]
|
||||
args:
|
||||
- -c
|
||||
- "cilium preflight fqdn-poller --tofqdns-pre-cache {{ .Values.preflight.tofqdnsPreCache }} && touch /tmp/ready-tofqdns-precache"
|
||||
livenessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/read-tofqdns-precachey
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
readinessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/read-tofqdns-precachey
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
env:
|
||||
{{- if .Values.k8sServiceHost }}
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: {{ .Values.k8sServiceHost | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServicePort }}
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: {{ .Values.k8sServicePort | quote }}
|
||||
{{- end }}
|
||||
volumeMounts:
|
||||
- mountPath: /var/run/cilium
|
||||
name: cilium-run
|
||||
{{- if .Values.etcd.enabled }}
|
||||
- mountPath: /var/lib/etcd-config
|
||||
name: etcd-config-path
|
||||
readOnly: true
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- mountPath: /var/lib/etcd-secrets
|
||||
name: etcd-secrets
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
# This is here to seamlessly allow migrate-identity to work with
|
||||
# etcd-operator setups. The assumption is that other cases would also
|
||||
# work since the cluster DNS would forward the request on.
|
||||
# This differs from the cilium-agent daemonset, where this is only
|
||||
# enabled when etcd.managed=true
|
||||
dnsPolicy: ClusterFirstWithHostNet
|
||||
restartPolicy: Always
|
||||
serviceAccount: cilium-pre-flight
|
||||
serviceAccountName: cilium-pre-flight
|
||||
terminationGracePeriodSeconds: 1
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
volumes:
|
||||
# To keep state between restarts / upgrades
|
||||
- hostPath:
|
||||
path: /var/run/cilium
|
||||
type: DirectoryOrCreate
|
||||
name: cilium-run
|
||||
- hostPath:
|
||||
path: /sys/fs/bpf
|
||||
type: DirectoryOrCreate
|
||||
name: bpf-maps
|
||||
{{- if .Values.etcd.enabled }}
|
||||
# To read the etcd config stored in config maps
|
||||
- configMap:
|
||||
defaultMode: 420
|
||||
items:
|
||||
- key: etcd-config
|
||||
path: etcd.config
|
||||
name: cilium-config
|
||||
name: etcd-config-path
|
||||
# To read the k8s etcd secrets in case the user might want to use TLS
|
||||
{{- if or .Values.etcd.ssl .Values.etcd.managed }}
|
||||
- name: etcd-secrets
|
||||
secret:
|
||||
defaultMode: 420
|
||||
optional: true
|
||||
secretName: cilium-etcd-secrets
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,86 @@
|
|||
{{- if .Values.preflight.enabled }}
|
||||
{{- if .Values.preflight.validateCNPs }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: cilium-pre-flight-check
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: cilium-pre-flight-check-deployment
|
||||
kubernetes.io/cluster-service: "true"
|
||||
template:
|
||||
metadata:
|
||||
{{- with .Values.preflight.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
k8s-app: cilium-pre-flight-check-deployment
|
||||
kubernetes.io/cluster-service: "true"
|
||||
spec:
|
||||
affinity:
|
||||
podAffinity:
|
||||
requiredDuringSchedulingIgnoredDuringExecution:
|
||||
- labelSelector:
|
||||
matchExpressions:
|
||||
- key: "k8s-app"
|
||||
operator: In
|
||||
values:
|
||||
- cilium
|
||||
topologyKey: "kubernetes.io/hostname"
|
||||
{{- if .Values.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{ toYaml .Values.imagePullSecrets | indent 8 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
{{- if .Values.preflight.validateCNPs }}
|
||||
- name: cnp-validator
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.preflight.image.repository }}:{{ .Values.preflight.image.tag }}
|
||||
imagePullPolicy: {{ .Values.preflight.image.pullPolicy }}
|
||||
command: ["/bin/sh"]
|
||||
args:
|
||||
- -c
|
||||
- "cilium preflight validate-cnp && touch /tmp/ready-validate-cnp && sleep 1h"
|
||||
livenessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/ready-validate-cnp
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
readinessProbe:
|
||||
exec:
|
||||
command:
|
||||
- cat
|
||||
- /tmp/ready-validate-cnp
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 5
|
||||
{{- if not ( and ( empty ( .Values.k8sServiceHost )) ( empty ( .Values.k8sServicePort ))) }}
|
||||
env:
|
||||
{{- if .Values.k8sServiceHost }}
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: {{ .Values.k8sServiceHost | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.k8sServicePort }}
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: {{ .Values.k8sServicePort | quote }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
hostNetwork: true
|
||||
restartPolicy: Always
|
||||
serviceAccount: cilium-pre-flight
|
||||
serviceAccountName: cilium-pre-flight
|
||||
terminationGracePeriodSeconds: 1
|
||||
{{- with .Values.preflight.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | trim | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | trim | nindent 6 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
{{- if and .Values.preflight.enabled .Values.serviceAccounts.preflight.create }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: cilium-pre-flight
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccounts.preflight.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccounts.preflight.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,35 @@
|
|||
{{- if or .Values.resourceQuotas.enabled (and (ne .Release.Namespace "kube-system") .Values.gke.enabled) }}
|
||||
{{- if .Values.agent }}
|
||||
apiVersion: v1
|
||||
kind: ResourceQuota
|
||||
metadata:
|
||||
name: cilium-resource-quota
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
hard:
|
||||
pods: {{ .Values.resourceQuotas.cilium.hard.pods | quote }}
|
||||
scopeSelector:
|
||||
matchExpressions:
|
||||
- operator: In
|
||||
scopeName: PriorityClass
|
||||
values:
|
||||
- system-node-critical
|
||||
{{- end }}
|
||||
{{- if .Values.operator.enabled }}
|
||||
---
|
||||
apiVersion: v1
|
||||
kind: ResourceQuota
|
||||
metadata:
|
||||
name: cilium-operator-resource-quota
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
hard:
|
||||
pods: {{ .Values.resourceQuotas.operator.hard.pods | quote }}
|
||||
scopeSelector:
|
||||
matchExpressions:
|
||||
- operator: In
|
||||
scopeName: PriorityClass
|
||||
values:
|
||||
- system-cluster-critical
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
{{- if and .Values.agent (not .Values.preflight.enabled) (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) }}
|
||||
{{- if or (and (.Values.clustermesh.apiserver.tls.auto.enabled) (eq .Values.clustermesh.apiserver.tls.auto.method "helm")) (and .Values.clustermesh.apiserver.tls.admin.cert .Values.clustermesh.apiserver.tls.admin.key) }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: clustermesh-apiserver-admin-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
type: kubernetes.io/tls
|
||||
data:
|
||||
{{- if and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm") }}
|
||||
{{ include "clustermesh.apiserver.admin.gen-cert" . | indent 2 }}
|
||||
{{- else }}
|
||||
tls.crt: {{ .Values.clustermesh.apiserver.tls.admin.cert }}
|
||||
tls.key: {{ .Values.clustermesh.apiserver.tls.admin.key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
{{- if and .Values.agent (not .Values.preflight.enabled) (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) }}
|
||||
{{- if or (and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm")) (and .Values.clustermesh.apiserver.tls.ca.cert .Values.clustermesh.apiserver.tls.ca.key) }}
|
||||
---
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: clustermesh-apiserver-ca-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
data:
|
||||
{{- if and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm") }}
|
||||
{{ include "clustermesh.apiserver.ca.gen-cert" . | indent 2 }}
|
||||
{{- else }}
|
||||
ca.crt: {{ .Values.clustermesh.apiserver.tls.ca.cert }}
|
||||
ca.key: {{ .Values.clustermesh.apiserver.tls.ca.key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
{{- if and .Values.agent (not .Values.preflight.enabled) .Values.externalWorkloads.enabled }}
|
||||
{{- if or (and (.Values.clustermesh.apiserver.tls.auto.enabled) (eq .Values.clustermesh.apiserver.tls.auto.method "helm")) (and .Values.clustermesh.apiserver.tls.client.cert .Values.clustermesh.apiserver.tls.client.key) }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: clustermesh-apiserver-client-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
type: kubernetes.io/tls
|
||||
data:
|
||||
{{- if and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm") }}
|
||||
{{ include "clustermesh.apiserver.client.gen-cert" . | indent 2 }}
|
||||
{{- else }}
|
||||
tls.crt: {{ .Values.clustermesh.apiserver.tls.client.cert }}
|
||||
tls.key: {{ .Values.clustermesh.apiserver.tls.client.key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,44 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.serviceAccounts.clustermeshApiserver.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: clustermesh-apiserver
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- endpoints
|
||||
- namespaces
|
||||
- services
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- discovery.k8s.io
|
||||
resources:
|
||||
- endpointslices
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
- list
|
||||
- apiGroups:
|
||||
- cilium.io
|
||||
resources:
|
||||
- ciliumnodes
|
||||
- ciliumnodes/status
|
||||
- ciliumexternalworkloads
|
||||
- ciliumexternalworkloads/status
|
||||
- ciliumidentities
|
||||
- ciliumidentities/status
|
||||
- ciliumendpoints
|
||||
- ciliumendpoints/status
|
||||
verbs:
|
||||
- '*'
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.serviceAccounts.clustermeshApiserver.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: clustermesh-apiserver
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: clustermesh-apiserver
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: clustermesh-apiserver
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,165 @@
|
|||
{{- if (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: clustermesh-apiserver
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
replicas: {{ .Values.clustermesh.apiserver.replicas }}
|
||||
selector:
|
||||
matchLabels:
|
||||
k8s-app: clustermesh-apiserver
|
||||
{{- with .Values.clustermesh.apiserver.updateStrategy }}
|
||||
strategy: {{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
{{- with .Values.clustermesh.apiserver.podAnnotations }}
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver
|
||||
spec:
|
||||
{{- with .Values.imagePullSecrets }}
|
||||
imagePullSecrets: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
restartPolicy: Always
|
||||
serviceAccount: clustermesh-apiserver
|
||||
initContainers:
|
||||
- name: etcd-init
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.clustermesh.apiserver.etcd.image.repository }}:{{ .Values.clustermesh.apiserver.etcd.image.tag }}
|
||||
imagePullPolicy: {{ .Values.clustermesh.apiserver.etcd.image.pullPolicy }}
|
||||
env:
|
||||
- name: ETCDCTL_API
|
||||
value: "3"
|
||||
- name: HOSTNAME_IP
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: status.podIP
|
||||
command: ["/bin/sh", "-c"]
|
||||
args:
|
||||
- >
|
||||
rm -rf /var/run/etcd/*;
|
||||
export ETCDCTL_API=3;
|
||||
/usr/local/bin/etcd --data-dir=/var/run/etcd --name=clustermesh-apiserver --listen-client-urls=http://127.0.0.1:2379 --advertise-client-urls=http://127.0.0.1:2379 --initial-cluster-token=clustermesh-apiserver --initial-cluster-state=new --auto-compaction-retention=1 &
|
||||
export rootpw=`head /dev/urandom | tr -dc A-Za-z0-9 | head -c 16`;
|
||||
echo $rootpw | etcdctl --interactive=false user add root;
|
||||
etcdctl user grant-role root root;
|
||||
export vmpw=`head /dev/urandom | tr -dc A-Za-z0-9 | head -c 16`;
|
||||
echo $vmpw | etcdctl --interactive=false user add externalworkload;
|
||||
etcdctl role add externalworkload;
|
||||
etcdctl role grant-permission externalworkload --from-key read '';
|
||||
etcdctl role grant-permission externalworkload readwrite --prefix cilium/state/noderegister/v1/;
|
||||
etcdctl role grant-permission externalworkload readwrite --prefix cilium/.initlock/;
|
||||
etcdctl user grant-role externalworkload externalworkload;
|
||||
export remotepw=`head /dev/urandom | tr -dc A-Za-z0-9 | head -c 16`;
|
||||
echo $remotepw | etcdctl --interactive=false user add remote;
|
||||
etcdctl role add remote;
|
||||
etcdctl role grant-permission remote --from-key read '';
|
||||
etcdctl user grant-role remote remote;
|
||||
etcdctl auth enable;
|
||||
exit
|
||||
volumeMounts:
|
||||
- mountPath: /var/run/etcd
|
||||
name: etcd-data-dir
|
||||
containers:
|
||||
- name: etcd
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.clustermesh.apiserver.etcd.image.repository }}:{{ .Values.clustermesh.apiserver.etcd.image.tag }}
|
||||
imagePullPolicy: {{ .Values.clustermesh.apiserver.etcd.image.pullPolicy }}
|
||||
env:
|
||||
- name: ETCDCTL_API
|
||||
value: "3"
|
||||
- name: HOSTNAME_IP
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: status.podIP
|
||||
command:
|
||||
- /usr/local/bin/etcd
|
||||
args:
|
||||
- --data-dir=/var/run/etcd
|
||||
- --name=clustermesh-apiserver
|
||||
- --client-cert-auth
|
||||
- --trusted-ca-file=/var/lib/etcd-secrets/ca.crt
|
||||
- --cert-file=/var/lib/etcd-secrets/tls.crt
|
||||
- --key-file=/var/lib/etcd-secrets/tls.key
|
||||
- --listen-client-urls=https://127.0.0.1:2379,https://$(HOSTNAME_IP):2379
|
||||
- --advertise-client-urls=https://$(HOSTNAME_IP):2379
|
||||
- --initial-cluster-token=clustermesh-apiserver
|
||||
- --auto-compaction-retention=1
|
||||
volumeMounts:
|
||||
- mountPath: /var/lib/etcd-secrets
|
||||
name: etcd-server-secrets
|
||||
readOnly: true
|
||||
- mountPath: /var/run/etcd
|
||||
name: etcd-data-dir
|
||||
- name: "apiserver"
|
||||
image: {{ template "system_default_registry" . }}{{ .Values.clustermesh.apiserver.image.repository }}:{{ .Values.clustermesh.apiserver.image.tag }}
|
||||
imagePullPolicy: {{ .Values.clustermesh.apiserver.image.pullPolicy }}
|
||||
command:
|
||||
- /usr/bin/clustermesh-apiserver
|
||||
args:
|
||||
{{- if .Values.debug.enabled }}
|
||||
- --debug
|
||||
{{- end }}
|
||||
- --cluster-name=$(CLUSTER_NAME)
|
||||
- --kvstore-opt
|
||||
- etcd.config=/var/lib/cilium/etcd-config.yaml
|
||||
env:
|
||||
- name: CLUSTER_NAME
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: cluster-name
|
||||
name: cilium-config
|
||||
- name: CLUSTER_ID
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: cluster-id
|
||||
name: cilium-config
|
||||
optional: true
|
||||
- name: IDENTITY_ALLOCATION_MODE
|
||||
valueFrom:
|
||||
configMapKeyRef:
|
||||
key: identity-allocation-mode
|
||||
name: cilium-config
|
||||
{{- with .Values.clustermesh.apiserver.resources }}
|
||||
resources: {{- toYaml . | nindent 10 }}
|
||||
{{- end }}
|
||||
volumeMounts:
|
||||
- mountPath: /var/lib/cilium/etcd-secrets
|
||||
name: etcd-admin-client
|
||||
readOnly: true
|
||||
volumes:
|
||||
- name: etcd-server-secrets
|
||||
projected:
|
||||
defaultMode: 0420
|
||||
sources:
|
||||
- secret:
|
||||
name: clustermesh-apiserver-ca-cert
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
- secret:
|
||||
name: clustermesh-apiserver-server-cert
|
||||
- name: etcd-admin-client
|
||||
projected:
|
||||
defaultMode: 0420
|
||||
sources:
|
||||
- secret:
|
||||
name: clustermesh-apiserver-ca-cert
|
||||
items:
|
||||
- key: ca.crt
|
||||
path: ca.crt
|
||||
- secret:
|
||||
name: clustermesh-apiserver-admin-cert
|
||||
- name: etcd-data-dir
|
||||
emptyDir: {}
|
||||
{{- with .Values.clustermesh.apiserver.nodeSelector }}
|
||||
nodeSelector: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.clustermesh.apiserver.tolerations }}
|
||||
tolerations: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "cronJob") .Values.clustermesh.apiserver.tls.auto.schedule }}
|
||||
apiVersion: batch/v1beta1
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver-generate-certs
|
||||
spec:
|
||||
schedule: {{ .Values.clustermesh.apiserver.tls.auto.schedule | quote }}
|
||||
concurrencyPolicy: Forbid
|
||||
jobTemplate:
|
||||
{{- include "clustermesh-apiserver-generate-certs.job.spec" . | nindent 4 }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) (eq .Values.clustermesh.apiserver.tls.auto.method "cronJob") }}
|
||||
apiVersion: batch/v1
|
||||
kind: Job
|
||||
metadata:
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver-generate-certs
|
||||
{{ include "clustermesh-apiserver-generate-certs.job.spec" . }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,34 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "cronJob") .Values.serviceAccounts.certgen.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: Role
|
||||
metadata:
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
resourceNames:
|
||||
- clustermesh-apiserver-ca-cert
|
||||
verbs:
|
||||
- get
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
resourceNames:
|
||||
- clustermesh-apiserver-server-cert
|
||||
- clustermesh-apiserver-admin-cert
|
||||
- clustermesh-apiserver-remote-cert
|
||||
- clustermesh-apiserver-client-cert
|
||||
verbs:
|
||||
- update
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,15 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "cronJob") .Values.serviceAccounts.certgen.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: RoleBinding
|
||||
metadata:
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: Role
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "cronJob") .Values.serviceAccounts.certgen.create }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: clustermesh-apiserver-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- with .Values.serviceAccounts.certgen.annotations }}
|
||||
annotations: {{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
{{- if and .Values.agent (not .Values.preflight.enabled) .Values.clustermesh.useAPIServer }}
|
||||
{{- if or (and (.Values.clustermesh.apiserver.tls.auto.enabled) (eq .Values.clustermesh.apiserver.tls.auto.method "helm")) (and .Values.clustermesh.apiserver.tls.remote.cert .Values.clustermesh.apiserver.tls.remote.key) }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: clustermesh-apiserver-remote-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
type: kubernetes.io/tls
|
||||
data:
|
||||
{{- if and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm") }}
|
||||
{{ include "clustermesh.apiserver.remote.gen-cert" . | indent 2 }}
|
||||
{{- else }}
|
||||
tls.crt: {{ .Values.clustermesh.apiserver.tls.remote.cert }}
|
||||
tls.key: {{ .Values.clustermesh.apiserver.tls.remote.key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,17 @@
|
|||
{{- if and .Values.agent (not .Values.preflight.enabled) (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) }}
|
||||
{{- if or (and (.Values.clustermesh.apiserver.tls.auto.enabled) (eq .Values.clustermesh.apiserver.tls.auto.method "helm")) (and .Values.clustermesh.apiserver.tls.server.cert .Values.clustermesh.apiserver.tls.server.key) }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: clustermesh-apiserver-server-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
type: kubernetes.io/tls
|
||||
data:
|
||||
{{- if and .Values.clustermesh.apiserver.tls.auto.enabled (eq .Values.clustermesh.apiserver.tls.auto.method "helm") }}
|
||||
{{ include "clustermesh.apiserver.server.gen-cert" . | indent 2 }}
|
||||
{{- else }}
|
||||
tls.crt: {{ .Values.clustermesh.apiserver.tls.server.cert }}
|
||||
tls.key: {{ .Values.clustermesh.apiserver.tls.server.key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,24 @@
|
|||
{{- if (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) }}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: "clustermesh-apiserver"
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: clustermesh-apiserver
|
||||
{{- with .Values.clustermesh.apiserver.service.annotations }}
|
||||
annotations: {{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
type: {{ .Values.clustermesh.apiserver.service.type }}
|
||||
selector:
|
||||
k8s-app: clustermesh-apiserver
|
||||
ports:
|
||||
- port: 2379
|
||||
{{- if and (eq "NodePort" .Values.clustermesh.apiserver.service.type) .Values.clustermesh.apiserver.service.nodePort }}
|
||||
nodePort: {{ .Values.clustermesh.apiserver.service.nodePort }}
|
||||
{{- end }}
|
||||
{{- if and (eq "LoadBalancer" .Values.clustermesh.apiserver.service.type) .Values.clustermesh.apiserver.service.loadBalancerIP }}
|
||||
loadBalancerIP: {{ .Values.clustermesh.apiserver.service.loadBalancerIP }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
{{- if and (or .Values.externalWorkloads.enabled .Values.clustermesh.useAPIServer) .Values.serviceAccounts.clustermeshApiserver.create -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: clustermesh-apiserver
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- with .Values.serviceAccounts.clustermeshApiserver.annotations }}
|
||||
annotations: {{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,54 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: etcd-operator
|
||||
rules:
|
||||
- apiGroups:
|
||||
- etcd.database.coreos.com
|
||||
resources:
|
||||
- etcdclusters
|
||||
- etcdbackups
|
||||
- etcdrestores
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- apiextensions.k8s.io
|
||||
resources:
|
||||
- customresourcedefinitions
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pods
|
||||
- services
|
||||
- endpoints
|
||||
- persistentvolumeclaims
|
||||
- events
|
||||
- deployments
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- extensions
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- get
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: etcd-operator
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: etcd-operator
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: cilium-etcd-sa
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
{{- if .Values.etcd.managed }}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: cilium-etcd-sa
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.serviceAccounts.etcd.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccounts.etcd.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,18 @@
|
|||
{{- if and (not .Values.preflight.enabled) .Values.agent .Values.hubble.enabled .Values.hubble.tls.enabled }}
|
||||
{{- $hubbleCAProvided := .Values.hubble.tls.ca.cert }}
|
||||
{{- $hubbleCAGenerate := and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "helm") .Values.hubble.relay.enabled -}}
|
||||
{{- if or $hubbleCAProvided $hubbleCAGenerate }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: hubble-ca-cert
|
||||
namespace: {{ .Release.Namespace }}
|
||||
data:
|
||||
{{- if $hubbleCAGenerate }}
|
||||
{{ include "hubble.ca.gen-cert-only" . | indent 2 }}
|
||||
{{- else }}
|
||||
ca.crt: |-
|
||||
{{ .Values.hubble.tls.ca.cert | b64dec | indent 4 -}}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
{{- if and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "cronJob") .Values.hubble.tls.ca.cert .Values.hubble.tls.ca.key }}
|
||||
---
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: hubble-ca-secret
|
||||
namespace: {{ .Release.Namespace }}
|
||||
data:
|
||||
ca.crt: {{ .Values.hubble.tls.ca.cert }}
|
||||
ca.key: {{ .Values.hubble.tls.ca.key }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,40 @@
|
|||
{{- if and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "cronJob") .Values.serviceAccounts.certgen.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: hubble-generate-certs
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
- configmaps
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
resourceNames:
|
||||
- hubble-server-certs
|
||||
- hubble-relay-client-certs
|
||||
- hubble-relay-server-certs
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
resourceNames:
|
||||
- hubble-ca-cert
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
resourceNames:
|
||||
- hubble-ca-secret
|
||||
verbs:
|
||||
- get
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "cronJob") .Values.serviceAccounts.certgen.create }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: hubble-generate-certs
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: hubble-generate-certs
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: hubble-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
{{- if and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "cronJob") .Values.hubble.tls.auto.schedule }}
|
||||
apiVersion: batch/v1beta1
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: hubble-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: hubble-generate-certs
|
||||
spec:
|
||||
schedule: {{ .Values.hubble.tls.auto.schedule | quote }}
|
||||
concurrencyPolicy: Forbid
|
||||
jobTemplate:
|
||||
{{- include "hubble-generate-certs.job.spec" . | nindent 4 }}
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
{{- if and .Values.hubble.tls.auto.enabled (eq .Values.hubble.tls.auto.method "cronJob") }}
|
||||
apiVersion: batch/v1
|
||||
kind: Job
|
||||
metadata:
|
||||
name: hubble-generate-certs
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
k8s-app: hubble-generate-certs
|
||||
{{ include "hubble-generate-certs.job.spec" . }}
|
||||
{{- end }}
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue